- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Palo Alto Updates Detected as a Threat
- LIVEcommunity
- Discussions
- General Topics
- Re: Palo Alto Updates Detected as a Threat
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Palo Alto Updates Detected as a Threat
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2022 09:09 PM
Hello all,
im using content update app and threat 8628-7631 and antivirus 4233-4746 on this day.
is there any url database update on app and threat 8628-7631 and antivirus 4233-4746?
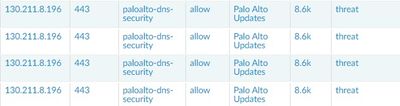
i have a problem on firewall palo alto, that firewall detected palo alto updates as a threat. the management traffic is traverse the firewall.
i have policy to allow the paloalto updates app. when i check the log it show palo alto updates detected as a threat
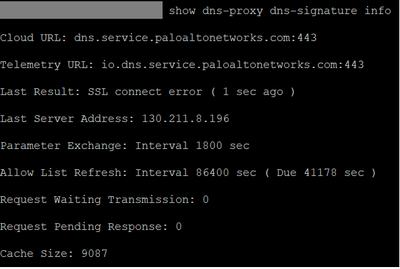
i check using command show dns-proxy dns-signature info and shows SSL Connect Error
i take a sample log on updates to wildfire, thereis no threat vault information
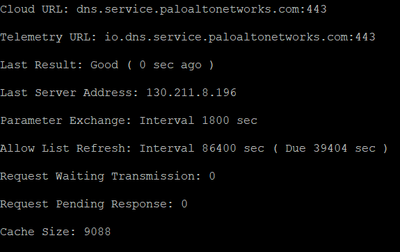
After i whitelist the url *.paloaltonetworks.com, im getting Good Result, but sometimes the updates still detected as a threat in traffic log.
second option is, the traffic from management to the palo alto updates i change the security profile to alert only(before it was strict)
Thanks,
Denny
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2022 05:20 AM
Hey @DennyChanditya ,
What threat log you see for the above corresponding traffic logs?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2022 01:38 PM
Hello,
Its best practice to not inspect the palo alto updates with any service including ssl decryption.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2022 07:59 PM
after some troubleshooting, there is no log on threat log, i see on url filtering that show category not-resolved that the action is block.
first i see the connection from firewall management to palo alto cloud is disconnect. so firewall cant identify the app traffic from internal to extenal since the connection is broke. so the firewall make all the traffic into category not-resolved with the block action, the internal traffic is getting block to external.
i have whitelist *.paloaltonetworks.com in url category , then make policy with alert security profile/remote this security profile from the policy than it will works.
still dont know why the connection from firewall to palo alto cloud is broke, but i assume that theres was a issue with the dns.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2022 08:08 PM
Thanks otakar, i didn't about this best practice.
for some reason our users dont want a policy that dont have any security profile, but in this case i attach the security profile but with alert only. we dont use the ssl decryption on the firewall.
- 4433 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Add Virus exception in General Topics
- Threat Protection Coverage for LockBit 5.0 in General Topics
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Welcome to the Advanced Threat Prevention Discussion Area! in Advanced Threat Prevention Discussions
- Palo Alto PAN-OS Adv threat and AV Update scheduling in General Topics