- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Password Reset using Global Protect App without PreLogon
- LIVEcommunity
- Discussions
- General Topics
- Password Reset using Global Protect App without PreLogon
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Password Reset using Global Protect App without PreLogon
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-21-2019 01:25 PM
Has anyone been able to configure their firewall so that users will be able to change thier password via the global protect app while using LDAP for authentication and NOT using Pre-Logon
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2019 01:02 PM
Hello Victor,
This is supported in the newer versions of PANOS and GP, however there are some requirements that have to be met on the RADIUS server.
1. The firewall only supports changing expired passwords when utilizing RADIUS with PEAP-MSCHAP-V2 authentication.
2. The RADIUS server has to be registered in AD and have permissions in the RAS and IAS Servers group.
3. The RADIUS server must have a certificate configured from a CA that can be validated/trusted by the firewall with a client certificate profile.
4. The firewall has to be a RADIUS client configured on the RADIUS server and have the desired authentication policies in place.
I have a lengthy guide for setting this up from scratch and utilizing Microsoft NPS. I will also warn you that in the event that the user tries to change their password to something that isn't in compliance with the AD Password policy, the message to the user is just a generic error, so its something to make people aware of that will be using the feature.
Thanks,
Brandon
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-13-2020 07:26 AM
Hello,
I have the same problem. Requirements you were talking about seem to be met.
When a user has a valid, non expired password everything works fine.
When using a user with an expired password, nothing is logged in event viewer in NPS server, authentication fails, and user is not prompted to change his password.
Could you please share the guide you were talking before?
Thanks in advance.
Regards,
Cristiano.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-14-2020 01:21 PM
Hello Cristiano,
See the document I've posted here -> https://drive.google.com/file/d/1_wjjrIILr2akt63ueUIK-xAq9zPwGqWw/view?usp=sharing
Keep in mind that you should use a Windows PKI issued Certificate on the RADIUS server, but I wrote this up since I've run into customers in the past that may not have that infrastructure available.
Thanks,
Brandon
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-17-2020 09:16 AM
Hi Brandon,
great doc.
I'll give it a try asap.
Thanks again.
Cristiano.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-19-2020 03:33 AM
Hi Brandon,
I've tried your document, but I have two problems:
1) at connection request level, it always hit the default (99999) policy, but I think this should not be a problem: reading your document It seemed to me that your making a specific policy only to override authentication polcy for a more clear readbility, am I right?
2) This insted is more problematic: I see that network policy hit is correct, but then I see this error in security event id on nps server:
"unable to authenticate client. Eap type could not be processed by the server". Googling around I always hit into certificate problems, but I don't think this is my case. In fact first of all, this only happens when I have a user password expired or in change password at next logon. Second, if I take a look at certificate in properties of peap it shows the right certificate ( signed by PA-CA ), so I think certificate chain should be ok.
Do you have any advices?
Thanks in advance,
Regards,
Cristiano.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2020 10:15 AM
HI Brandon, this setup should work regardless what type of GP agents one uses, correct? we have users using ios GP agents. Thank you very much in advance for your response.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2020 12:07 PM
Hello Cristiano,
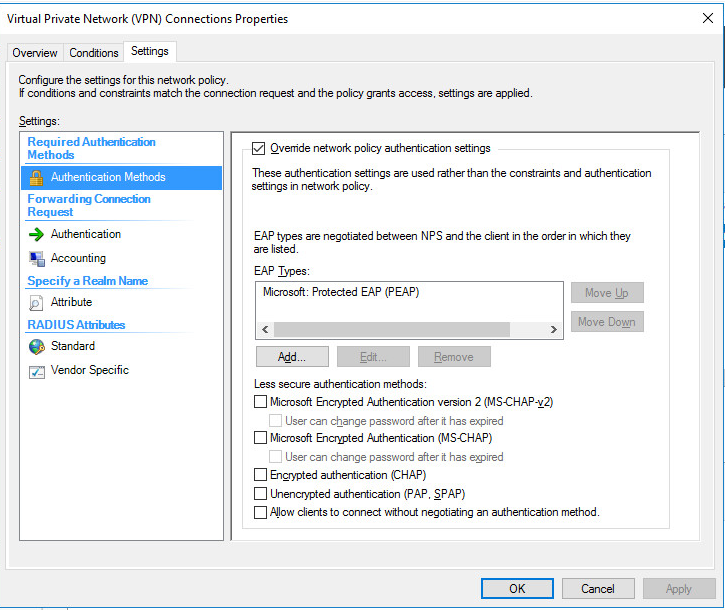
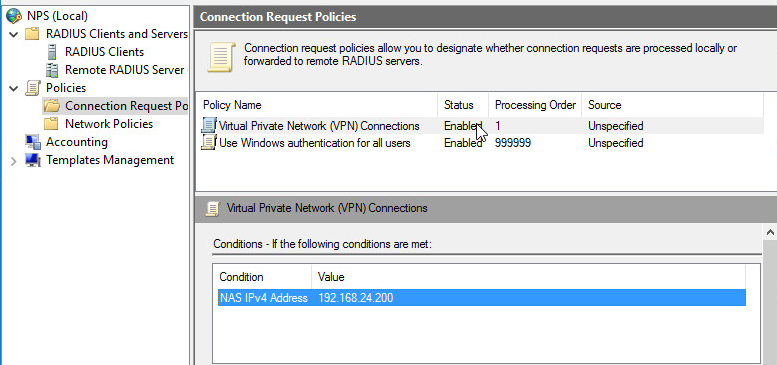
Make sure that you have EAP type added for PEAP, on the connection policy:
Also ensure you have a condition set for the connection request policy:
Also ensure that after you put the cert and key pair on the RADIUS server that you make sure that's being used by the RADIUS server, and that the profile is set to trust from that CA. It needs to be in the Machine store I believe:
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2020 12:09 PM
Hello Cristiano,
I believe it should work with any variant of the GP client since the RADIUS challenge response stuff is built into all of the clients.
Thanks,
Brandon
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-07-2020 09:55 AM
Not supported on SAML?
- 18903 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- False Positive - Compresso.exe in VirusTotal
- RADIUS flows for Authenticating GP with username, password and OTP in GlobalProtect Discussions
- Password spraying in Cortex XDR Discussions
- Unable to connect VPN in GlobalProtect Discussions
- Any.run Cloud Sandbox Integration - Instructions not Clear in Cortex XSOAR Discussions