- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Security Policies Not Applied When Client Use Web Proxy on Their Browser
- LIVEcommunity
- Discussions
- General Topics
- Re: Security Policies Not Applied When Client Use Web Proxy on Their Browser
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Security Policies Not Applied When Client Use Web Proxy on Their Browser
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-04-2017 03:19 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2017 06:24 AM
Hi @hibagus,
Does these rules involve user identification as well or are they simply on source and destination IP's.
What is the application getting identified in the rules which are working and non working ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2017 06:35 AM
Hi @hpunjabi,
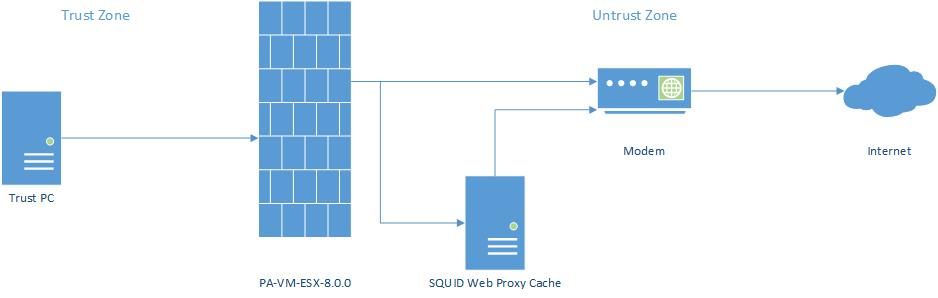
Here is the simplified topology of my network.
There are two zones, the Untrust Zone and Trust Zone. I configure all of the security policies with Source=Trust Zone and Destination=Untrust Zone. Here are the two of my security rules as an example.
* User can access Facebook but cannot use chat and comment or like the post.
* User cannot upload PDF file.
All of the rules are working perfectly if the User (Trust PC) access the web directly. But, if I configure the browser in Trust PC to access the web via SQUID Web Proxy Cache, the security rules seem do not have effects (i.e. User can still upload PDF file or use Facebook chat).
Thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2017 06:54 AM
Ok, so is squid traffic hitting same policy as that of Direct traffic ?
Also can you try to configure a policy for below website and see if it works in both the scenarios, if it works then decryption might be one of the reason for it not working.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2017 07:10 AM
You are right, I cannot upload PDF into the non-SSL website both by connecting directly through internet or by connecting via Squid Proxy.
If the site uses SSL and I connect through the Squid Proxy, then the rules will not be applied (i.e. still can upload PDF file).
I use SSL Forward Proxy in the decryption. Is there anything I need to configure?
Thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2017 07:30 AM
For Decryption you might need to look at your decryption policies first see if squid proxy (IP or port) is mentioned in decryption and see if it is working fine.
One simple way to check if decryption is working or not is to check certificate in your browser when working through squid are you getting certificate from firewall or from the server directly.
Also in the logs, if you see logs detail and in flags section check if you are able to see decrypt flag.
Below article can help you to troubleshoot decryption if it is not working:
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2017 05:02 AM
Hi @hpunjabi.
Sorry for the late response.
I have checked that by using SSL Forward Proxy, all of the clients get the certificate from the firewall. I also enable the SSL decryption opt-out page for making sure whether the SSL decryption works or not. Fortunately, yes, it is working and the opt-out page is displayed on the client browser.
But, the policies (e.g. file blocking, application blocking) are still not applied when the users browse through the squid proxy. If the users browse directly (without web proxy), the policies are applied. I have no idea why.
Any ideas?
Thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2017 08:17 AM
Hi @hibagus,
Can you check which rule is it hitting while you are accessing through squid proxy is it the same rule created for squid proxy or different.
If the rule hitting is different than one thing which I can think of now is that you have 'application-default' enabled under service section in the squid policy, change that to 'any' and check if it is working after that.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-12-2017 02:12 AM
Dear @hpunjabi.
I did what you have suggested and it did not work as expected.
I think it looks like there is a difference between the "direct access" request and "through proxy" request.
I've read the article below
https://blog.webernetz.net/at-a-glance-http-proxy-packets-vs-normal-http-packets/
I suspect that the application traffic from the proxy does not match the default application signature defined in Palo Alto Firewall thus it let them through. I think I need to define a new application in the Palo Alto Firewall and define a new "proxy" signature to help the Firewall to identify.
Do you know how to copy and modify the applications that already have defined in Palo Alto Firewall? It seems that I cannot clone it and modify the signature.
Thank you.
Sincerely,
Bagus Hanindhito
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-12-2017 08:09 AM
Hi Bagus,
You wont be able to clone an http-proxy application, you will have to define a custom application:
I am pretty sure it is something to tweak with your security/decryption policies,try correlating logs when accessing directly and when going through squid proxy, check if facebook chat and other applications are getting identified.
If you can paste decryption policy and security policy for facebook then we can take a look.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-13-2017 12:26 AM
It really is highly unusual to have your proxy outside your firewall. Why isn't your proxy in the Trust zone? If it were inside, the PA would see it as just another client and your policies would work as you expect.
Connections via proxies are not quite the same as those that go direct, so I suspect that your firewall is not seeing the traffic as web traffic and is not applying your policies to it.
- 7896 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PAN-OS 12.1, IPv6 and Region/GeoIP in General Topics
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- Problem with downloading PAN OS in General Topics
- Security Policy with Destination Criteria in Strata Cloud Manager
- web file blocking in Next-Generation Firewall Discussions