- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Security policy rule - allowing a specific host access to ftp.sophos.com
- LIVEcommunity
- Discussions
- General Topics
- Re: Security policy rule - allowing a specific host access to ftp.sophos.com
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Security policy rule - allowing a specific host access to ftp.sophos.com
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-04-2018 03:12 AM
Hello,
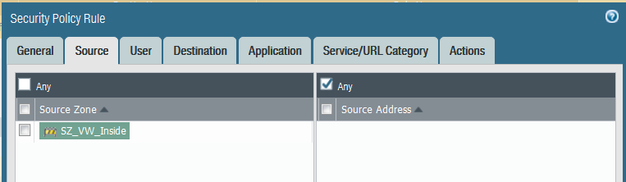
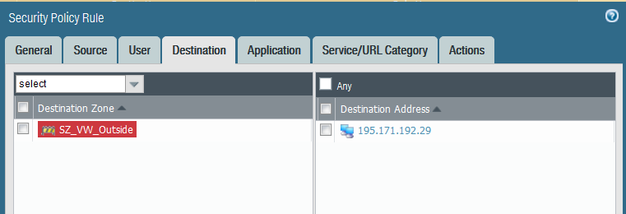
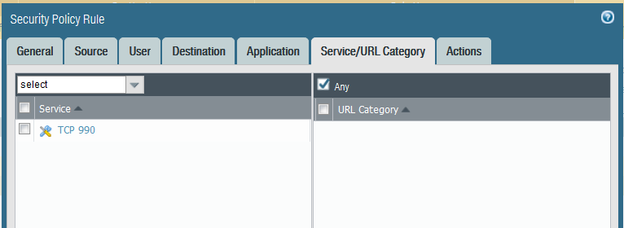
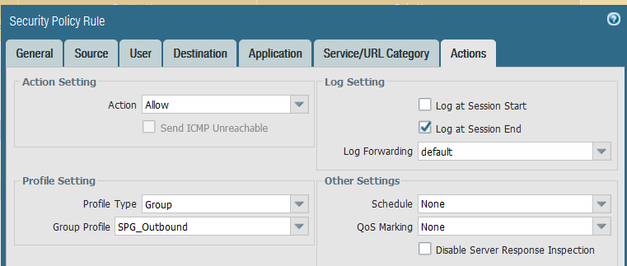
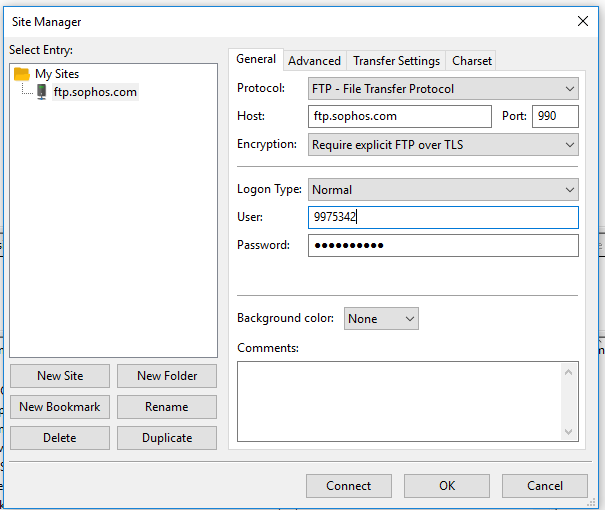
A colleague needs to access ftp.sophos.com (195.171.192.29) using Filezilla as their SFTP client, via TCP port 990. I set up the security policy rule as follows:
They could not log onto the ftp.sophos.com site. The password credentials they used are correct. Is the rule set up correctly? On a Cisco ASA I would have used the following ACL:
access-list aclinside extended permit tcp any host 195.171.192.29 eq 990
Any advice is much appreciated.
Regards,
Roberto
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-04-2018 05:27 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-04-2018 05:39 AM
I've had to add the SSH application to many SFTP rules, as the firewall usually sees that. Look in your Unified Logs and it should show you why it was denied.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-04-2018 05:56 AM
Hello Hodor,
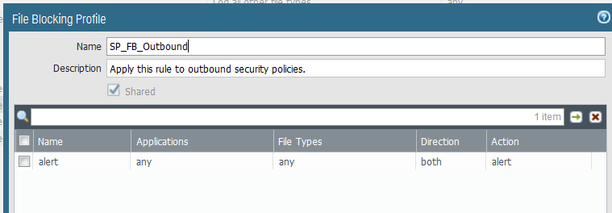
Thanks for your reply. The file blocking profile looks good.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-04-2018 06:21 AM
Like @DPoppleton mentioned what do the deny logs say is the reason for traffic being stopped? What is the FW seeing?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-04-2018 06:49 AM
Hi DPoppleton,
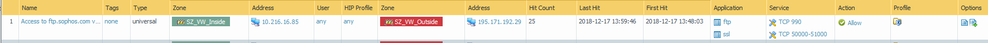
I don't see any 'deny' in the Actions when the user is trying to access 195.171.192.29
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-04-2018 06:57 AM
That screen shot shows the application as FTP, which means the FileZilla client isn't encrypting. The client may need to be set to use SFTP (and the firewall will see that as SSH, so you will need to add that application to your rule.)
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-05-2018 03:08 AM
Hi DPoppleton,
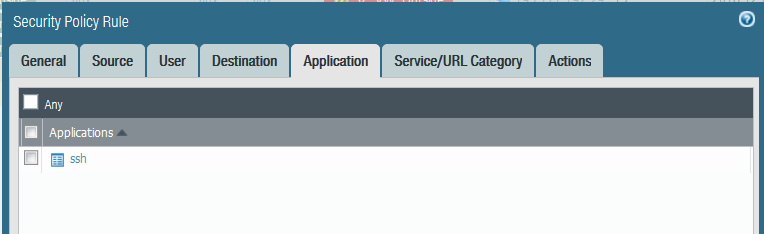
Thanks for your reply again. I have now added SSH under Application within my rule.
I will have the user test.
Many thanks,
Roberto
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-05-2018 03:12 AM
@DPoppleton, forgot to mention that the Filezilla client was configured for SFTP and was tested on a ADSL line and the user was able to connect fine.
Thanks,
Roberto
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-07-2018 06:24 AM
Have you found a solution to this issue yet?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-11-2018 03:57 AM
Hi DPoppleton,
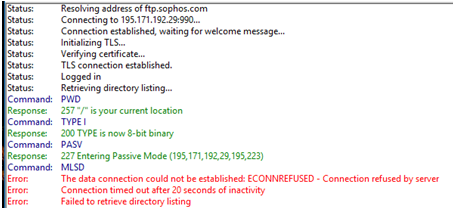
Still not working.
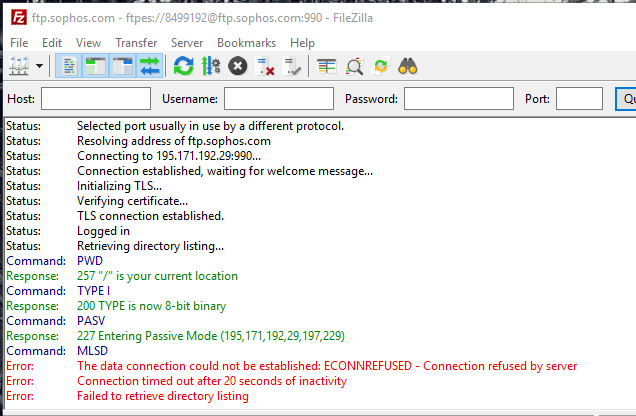
I get this from the log in the Filezila FTP client.
Filezila client configured as so for FTP over SSL/TLS
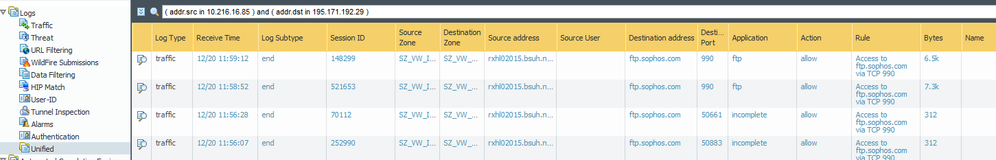
Logs from Unified today.
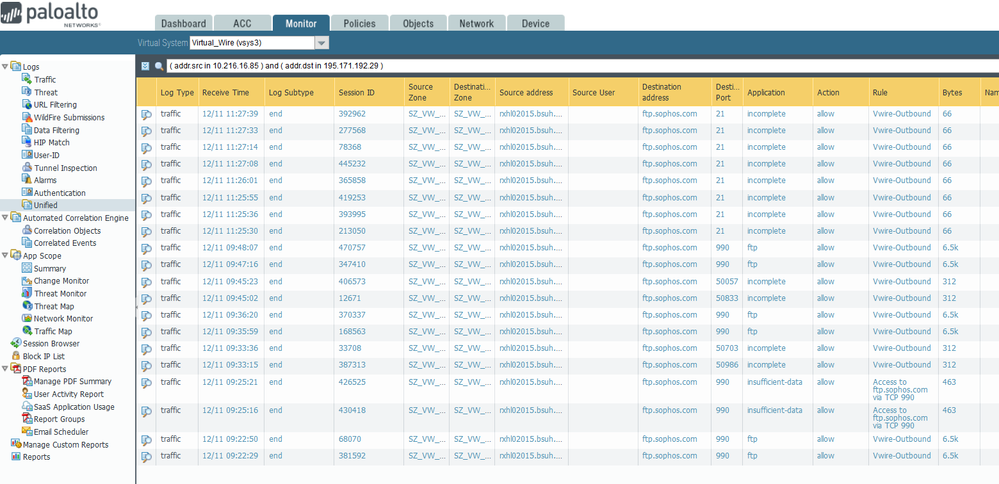
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-13-2018 01:22 PM
This isn't caused by the firewall.... I seem to remember a problem with the MLSD command with certain clients or servers while running a passive FTP connection. Try it as an active connection and I think it would work.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-16-2018 07:35 AM
Thanks for the info on allowing a specific host access to ftp.sophos.com jira
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2018 05:32 AM
Very important this is NOT sftp (which is a file transfer protocol using the same port and encryption as ssh). We are talking about ftp over ssl.
this is explicit ftp over ssl. Meaning the client wil use ftp to connect to ftp.sophos.com and than do TLS encryption and than with an encrypted connection it will do authentication and negotation which ports to use for the data connection.
fom https://community.sophos.com/kb/en-us/113454
you will need to allow the application: ftp to connect to tcp port 990 for ftp.sophos.com.
after that you will need to allow the application ssl with ports 50000-51000
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2018 04:03 AM
Hi Rikkert_Kooy,
Thank you for your reply. My mistake, it is explicit FTP over SSL, not SFTP.
I have added ftp to the Application and already had TCP port 990 under the Service. I also added SSL and the port range 50000-51000, but it is still not working. The Palo is not configured for SSL decrypt/encrypt. Could this be why it is still not working?
Unified logs - it says incomplete in Application. What does this mean please?
Error message on the Filezilla client
Thanks.
- 12970 Views
- 18 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Syncing Specific Entra ID Groups to Cloud Identity Engine in GlobalProtect Discussions
- Max number of units (aeX.Y subinterfaces) supported under a single AE interface? in Next-Generation Firewall Discussions
- Cortex XDR – Unable to Assign Read/Write Permissions for Mobile Device (Detected as CD-ROM) in Permanent Exceptions in Cortex XDR Discussions
- Vulnerability Assessment in XSIAM 3.3 in Cortex XSIAM Discussions
- Inquiry Regarding Publishing Custom Third-Party IOC Feed via EDL Hosting Service in Next-Generation Firewall Discussions