- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decryption
- LIVEcommunity
- Discussions
- General Topics
- SSL Decryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Decryption
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-29-2012 05:06 PM
Hi All, I have an issue with SSL decryption and using the inbuilt CA. What appears to happen is that various parts of SSL websites don't trust the CA on the palo alto and as a consequence sites do not load fully and report various certificate issues.
This is what https facebook looks like:
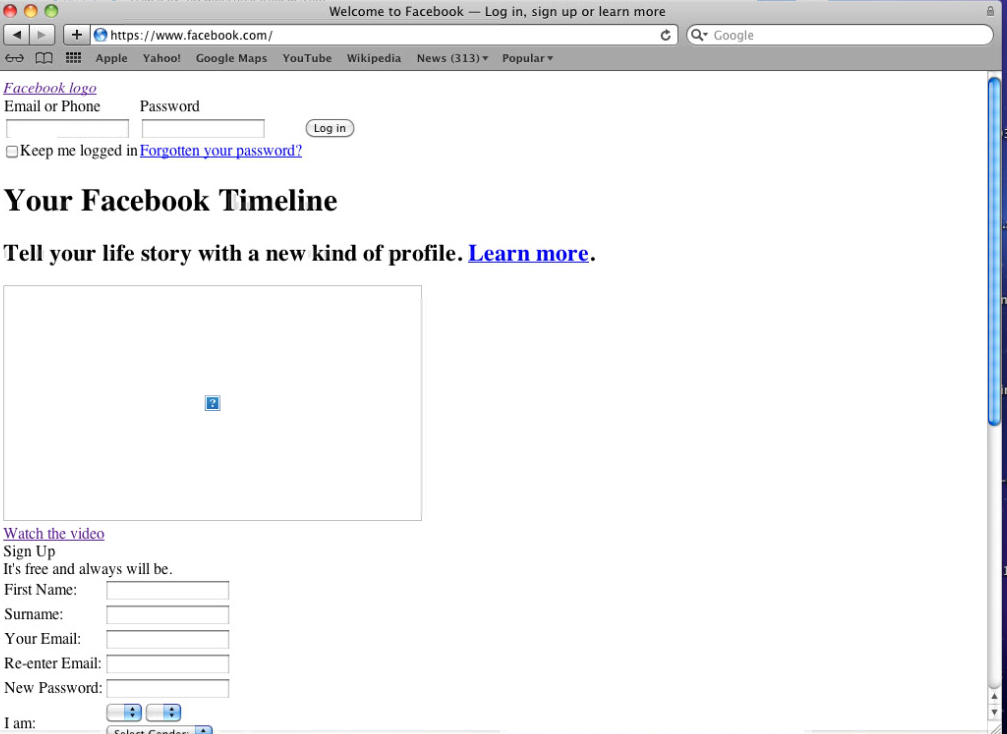
The corresponding browser complaints:
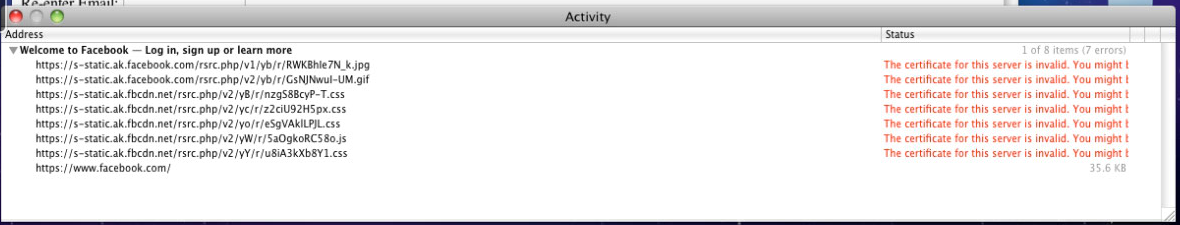
I'm running the very latest OS 4.1.6 but I was running 4.1.3 and this problem was evident then as well. I've tried uploading a trusted certificate from rapidssl and I don't get the option to select that is a valid certificate for a forward SSL proxy which is understandable as I don't have a key.
So I'm obviously doing something wrong - whats the accepted procedure to get this up and running?
Thanks in advance for your help
- Labels:
-
Configuration
-
Management
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2012 12:51 AM
Hi Andre,
Firstly thanks for the config guide, but unfortunately it doesn't work for me in my scenario. We don't use AD or windows so I can't push out certificates using GPO. We are linux/Mac based and rely on users clicking the right option when their browser prompts them to accept a certificate. In the facebook case above the browser does not load the s-static.ak.fbcdn.net certificate. I need to manually load this into the browser on my test machine for https facebook to work.
I have tried other SSL sites, (gmail,hotmail,yahoo) these exhibit the same issue where the site doesn't trust the CA on the palo alto and doesn't load some certificates. This causes various parts of these sites to break.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2012 01:00 AM
Hi
I don't run WIndows either, pure Mac based environment 🙂
Yes, you have to import the forward-trust CA certificate into the client browsers, there is no way around it. If you do so, all runs smoothly even on a Mac.
If you go with two vert CAs (like in my guide), import both CAs into the clients browser
And don't forget to use a forward-untrust vert (do NOT import it). Doing so should allow you to see the certificate chain of both working and not working SSL Sites.
What I don't get: You say the Website does'n trust the Palo Alto CA? What do you mean by this? The PA behaves like a normal client to the original server, so it doesn't use any (of it's own) certificates.
Andre
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2012 02:44 AM
Ok so here's what I've done. Downloaded the forward_trust CA and imported that into the keychain on an OS X machine. Fire up safari and go to ssl facebook. The browser complains that the identity of www.facebook.com can't be identified and asks me what to do. I click continue. Nothing appears to have changed from my first post and the safari activity window reports that the certificate for s-static.ak.fbcdn.net is invalid because the certificate issuer can't be identified.
Various other parts of SSL websites also break in this manner - hotmail,yahoo and gmail all report at some point that a certificate is invalid.
This is the screenshot of the certificates page

And a screenshot of the decryption settings
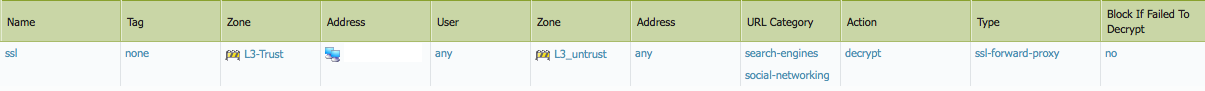
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2012 04:08 AM
Looks good so far
you need to import the forward_trust and the root_ca into Mac OS-X.
Also: is the forward_trust signed by the root_ca?
Can you send a screenshot of the https certificate chain when calling the facebook site?
Andre
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2013 07:17 AM
were you ever able to resolve this issue? I am having the exact same problem
- 8454 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Chatgpt enteprise login only in Next-Generation Firewall Discussions
- web file blocking in Next-Generation Firewall Discussions



