- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Wildcard certificate for management interface access
- LIVEcommunity
- Discussions
- General Topics
- Re: Wildcard certificate for management interface access
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-07-2022 04:30 PM
Hi,
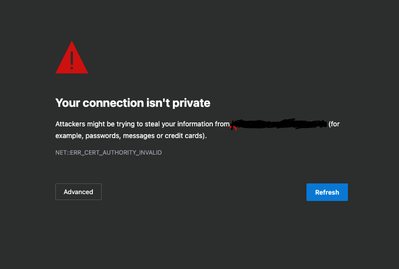
A client is trying to install a wildcard certificate on their firewall for management access, but is receiving a certificate error in the browser.
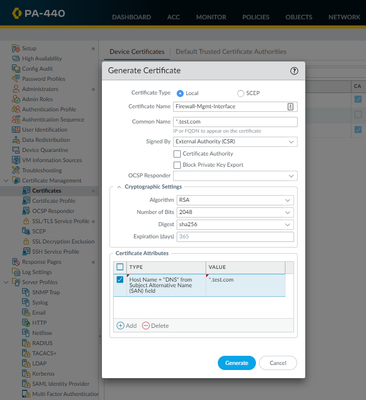
Is the below the correct way to generate the required CSR for the firewall for a wildcard certificate?
Can a certificate with the attributes shown be uploaded to the firewall and work, without a CSR being generated on the firewall?
@BPry
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2022 05:14 PM
Deleted the wildcard certificate and re-imported and that has fixed the issue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2022 07:08 AM
Hi @Ben-Price ,
In order to get better traction for this, I have moved your post to the General Topics area, as the Feedback area is only for feedback to the LIVE community.
I would recommend that you visit the General Topics area to see and follow up on your discussion.
Cheers,
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2022 08:14 AM
What's the error they get?
If you use a PKCS12 certificate that includes a private key, you can upload a certificate without a CSR being generated on the PA.
Why would you use a wildcard for a device management certificate?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2022 01:46 PM
@rmfalconer Thanks for the feedback. Client is using the wildcard for GP and Management interface. Wildcard cert is working for GP. Client said the Wildcard certificate was working for the Mgmt Interface, when they were on PAN OS 10.0.9, they rolled back to 10.0.8 as they were having commit issues on 10.0.9 and now on 10.0.8 the certificate is broken. I don't see any known issues for this type of thing in PAN OS 10.0.8.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2022 08:20 PM
Have you inspected the certificate and actually verified that the rollback didn't somehow break the firewall's service profile association? I can't say I've ever used a wildcard for our firewalls, I just issue them their own certificates through internal PKIs instead, but it should work perfectly fine just testing it out in my lab. I would expect to have additional information detailed in the certificate (Country, State, Org is generally the minimum I've seen referenced), but as long as it's signed by your internal CA that shouldn't matter.
The error that you have in your screenshot though points to an issue with the actual issuing certificate authority trust. That makes me think that it either wasn't signed, it's presenting an unexpected certificate versus what the customer is expecting, or it's reverted back to the default and removed the specified SSL/TLS service profile that used to be specified while it was working.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2022 05:14 PM
Deleted the wildcard certificate and re-imported and that has fixed the issue.
- 1 accepted solution
- 5642 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- IPSEC VPN for the FW MGMT in Next-Generation Firewall Discussions
- How do I access init-cfg.txt in VM-Series in the Public Cloud
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- PA-415-5G not working with fresh T-Mobile SIM in General Topics
- PA-440 won't talk via network in Next-Generation Firewall Discussions