- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect: Initial Set Up
- LIVEcommunity
- Products
- Network Security
- GlobalProtect
- GlobalProtect Articles
- GlobalProtect: Initial Set Up
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 04-10-2020 11:58 AM - edited on 07-07-2022 01:57 PM by jennaqualls

In my blog, "GlobalProtect: Overview," I provided a synopsis of the GlobalProtect series and overall objectives, including a description of each article in this series. I would recommend starting there prior to moving forward.
In this post, I will cover the initial setup of GlobalProtect, which includes a portal, external gateway, and user authentication via local database. You can see a diagram of the environment here.
Part I - Initial Setup
- Navigate to Device > GlobalProtect Client then download and activate the latest version (5.0.8 is a TAC-preferred version at the time of this blog post)
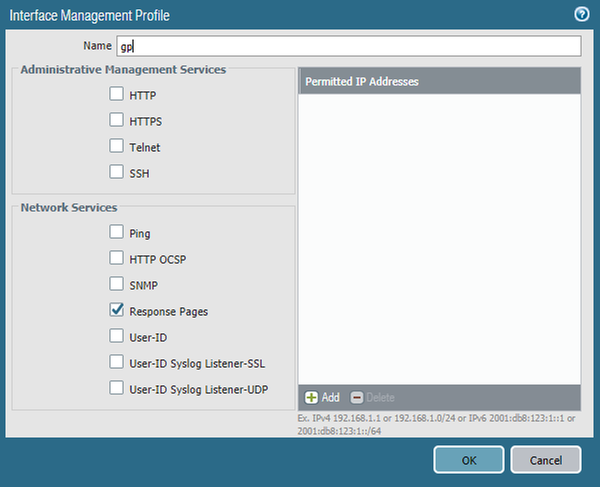
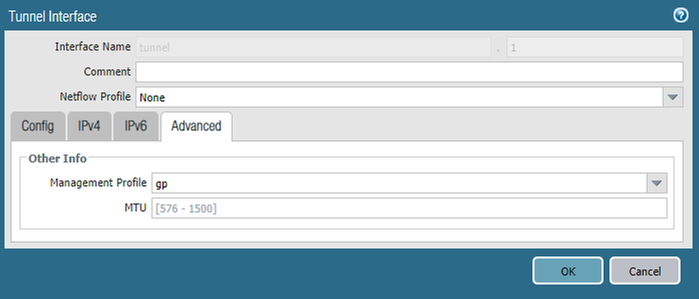
- Navigate to Network > Network Profiles > Interface Mgmt > Add and create a management profile to apply to the tunnel interface to which remote users will connect
- Enable Response Pages
- NOTE: It is not required to enable Response Pages, but this feature will be used in a subsequent article
- Click OK
- Enable Response Pages
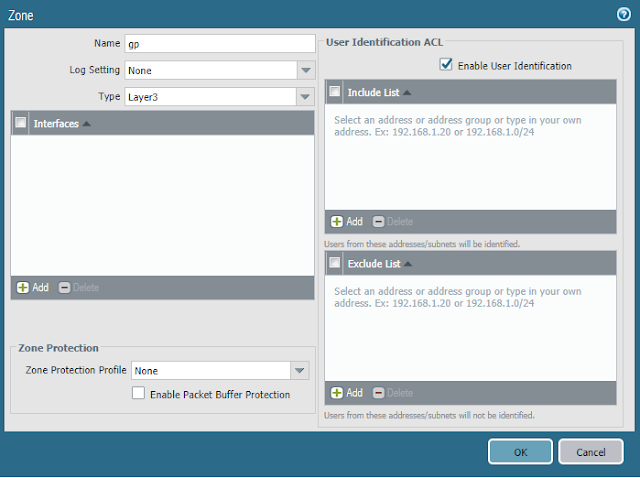
- Navigate to Network > Zones > Add and create a new Layer 3 security zone for your GlobalProtect users
- Provide a name (e.g., gp)
- Set Type to Layer3
- Check the Enable User Identification box
- Click OK
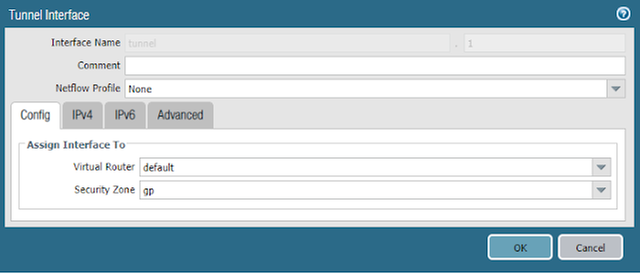
- Navigate to Network > Interfaces > Tunnel > Add and create a new tunnel interface
- Assign the interface a number (e.g., 1)
- Assign the interface to the appropriate Virtual Router
- Assign the interface to the appropriate Security Zone
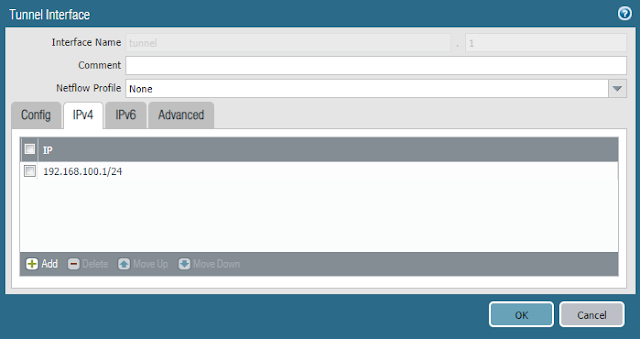
- Navigate to the IPv4 tab and assign a subnet to be used for your mobile users
- NOTE: It should be a unique network. Also, note that an IP address on this interface is not a requirement.
- Navigate to the Advanced tab and apply the Management Profile created for the tunnel interface above
- Click OK
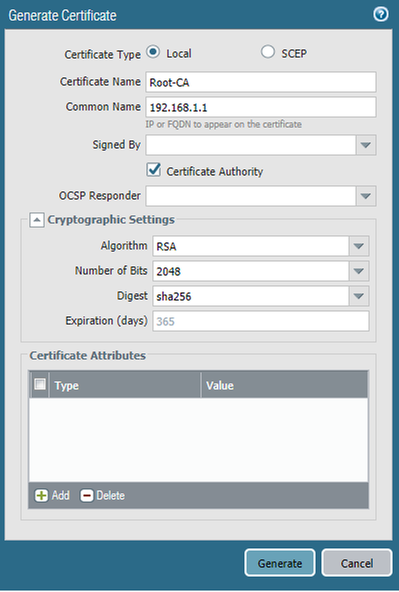
- Navigate to Device > Certificate Management > Certificates > Generate and create a trusted root certificate
- NOTE: In this series of posts, we will be using self-signed certificates. It is recommended to use third-party certificates in a production environment, but self-signed certificates will work as well.
- Enter a Certificate Name
- Enter the management IP of the firewall for the Common Name
- Check the Certificate Authority box
- Enter information in other fields if desired (optional)
- Click Generate
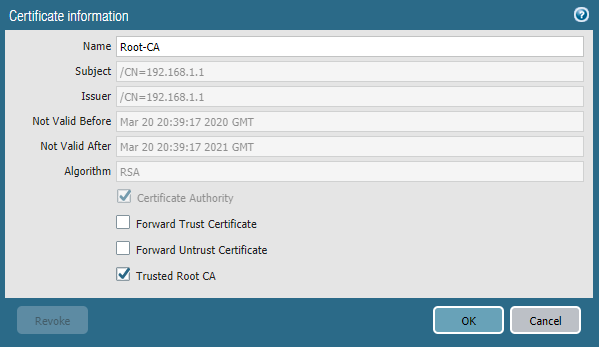
- Select the certificate you just created, and check the Trusted Root CA box
- Click OK
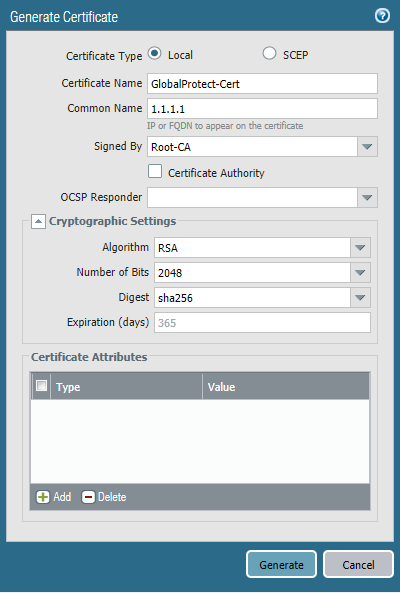
- Navigate to Device > Certificate Management > Certificates > Generate and a create certificate for GlobalProtect
- Enter a Certificate Name
- Enter the IP address or the DNS name of the interface to which remote users will connect for Common Name
- NOTE: In this series of posts, we will be using the public IP address for the common name (represented by 1.1.1.1), and it is recommended to use a DNS name in a production environment but IP addresses will work as well
- Select the certificate previously created under "Signed By"
- Enter information in other fields if desired (optional)
- Click Generate
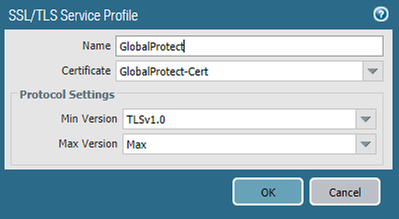
- Navigate to Device > Certificate Management > SSL/TLS Service Profile > Add
- Enter a Name
- Select the Certificate previously created
- Click OK
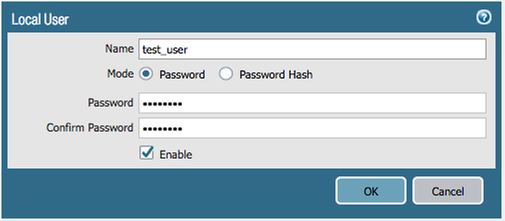
- Navigate to Device > Local User Database > Users > Add
- Enter a Name and Password
- Click OK
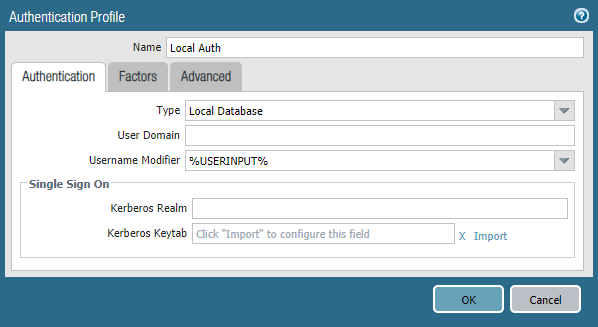
- Navigate to Device > Authentication Profile > Add
- Enter a Name
- Select Local Database for Type
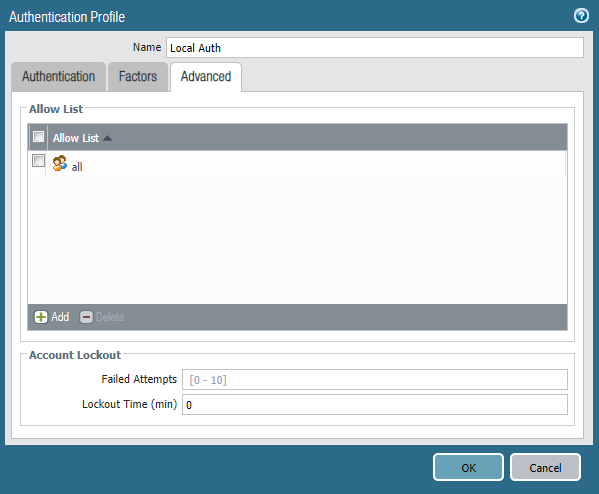
- Navigate to Advanced > Add
- Select All
- Click OK
- Navigate to Network > GlobalProtect > Gateway > Add
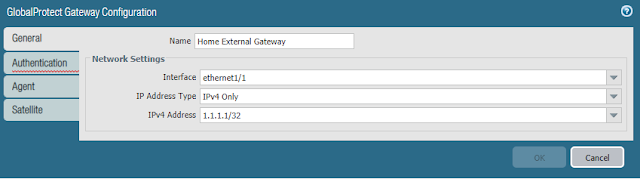
- In the General tab
- Enter a Name
- Select the interface to which remote users will connect
- Select the IPv4 Address of the interface
- NOTE: If your interface is assigned an IP address via DHCP, then you will not have an option to select an IPv4 Address. Just leave this field set to None.
- In the General tab
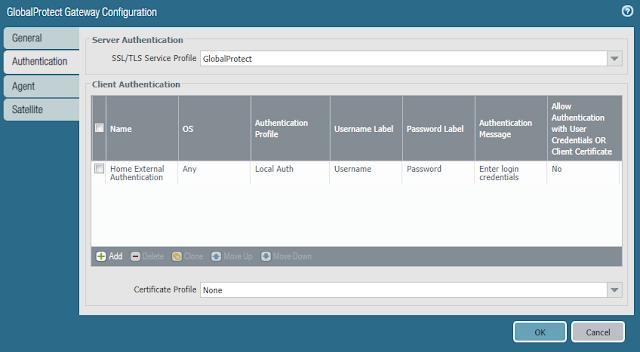
- In the Authentication tab
- Select the SSL/TLS Service Profile previously created
- Under Client Authentication click Add
- Enter a Name
- Select the Authentication Profile previously created
- Click OK
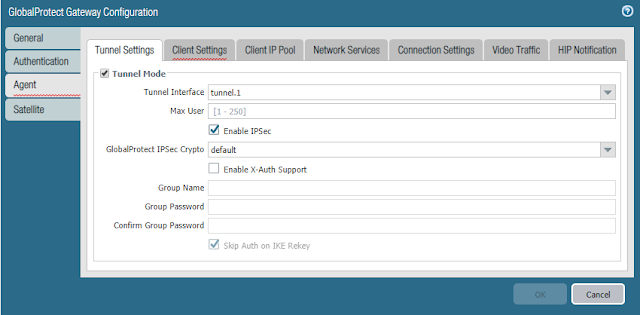
- In the Agent tab
- In the Tunnel Settings tab
- Enable Tunnel Mode
- Select the Tunnel Interface previously created
- In the Tunnel Settings tab
- In the Client Settings tab
- Click Add
- In the Config Selection Criteria tab, enter a Name
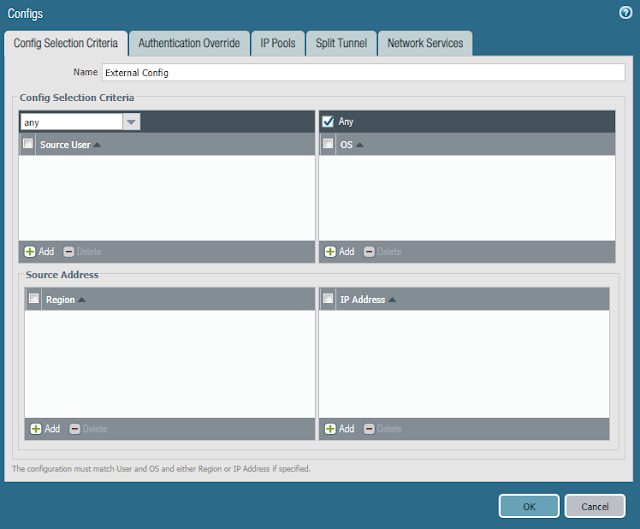
- In the IP Pools tab
- Add an IP Pool
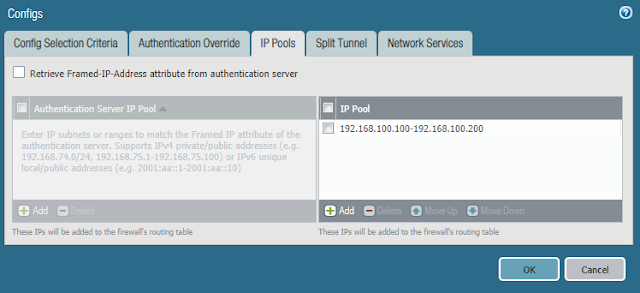
- In the Split Tunnel tab
- Add an access route to the Include section
- NOTE: In this series of posts we will be routing all traffic through the tunnel. It is recommended to tunnel all traffic in a production environment to ensure consistent protection.
- Click OK
- Add an access route to the Include section
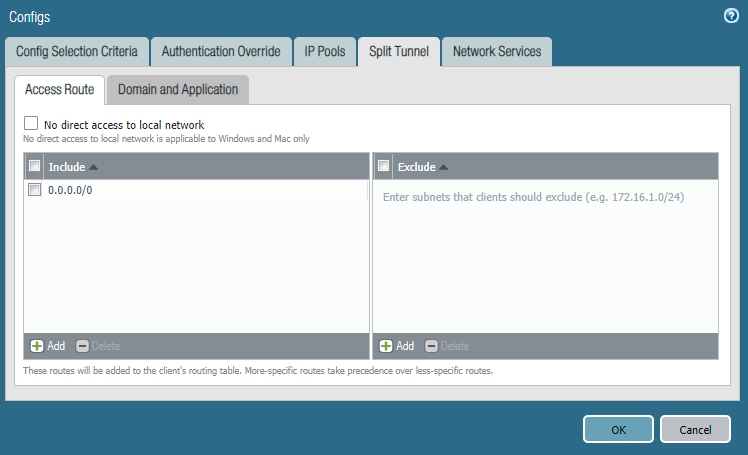
- In the Network Services tab
- Enter values for Primary DNS and Secondary DNS
- Click OK
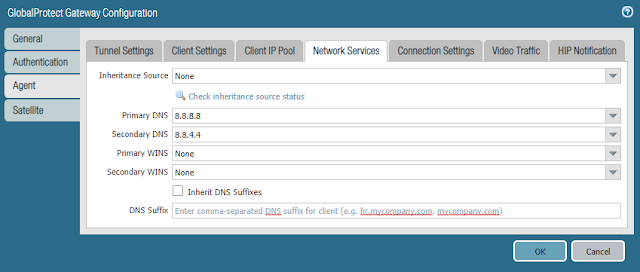
- Navigate to Network > GlobalProtect > Portal > Add
- In the General tab
- Enter a Name
- Select the Interface to which remote users will connect
- Select the IP Address of the interface
- In the General tab
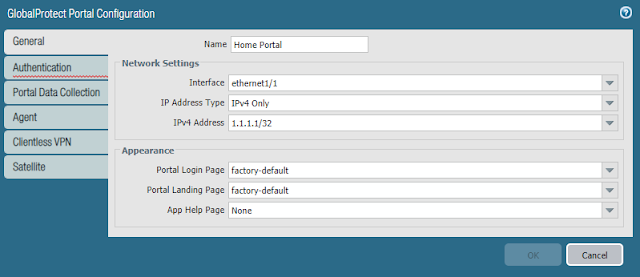
- In the Authentication tab
- Select the SSL/TLS Service Profile previously created
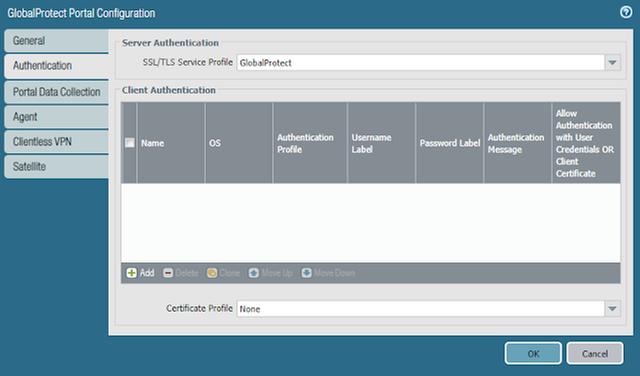
- Under Client Authentication click Add
- Enter a Name
- Select the Authentication Profile previously created
- Click OK
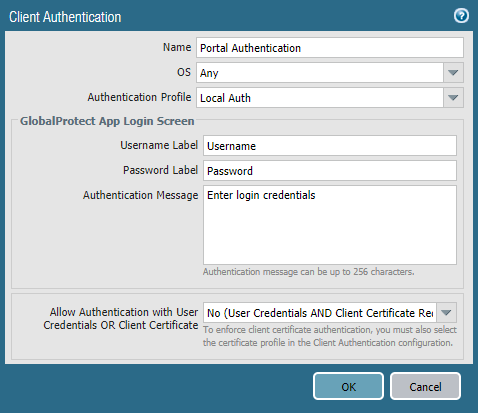
- In the Agent tab
- Click Add under Configs
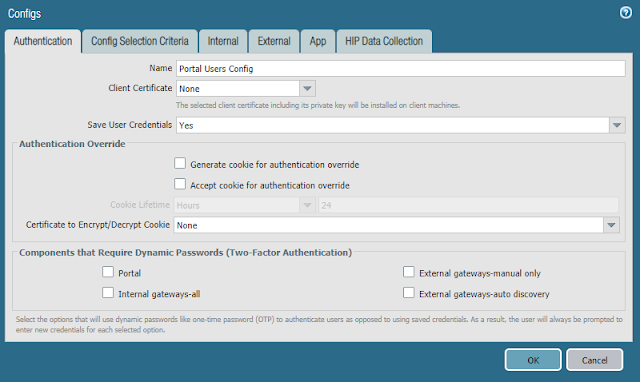
- In the Authentication tab
- Enter a Name
- In the Authentication tab
- Click Add under Configs
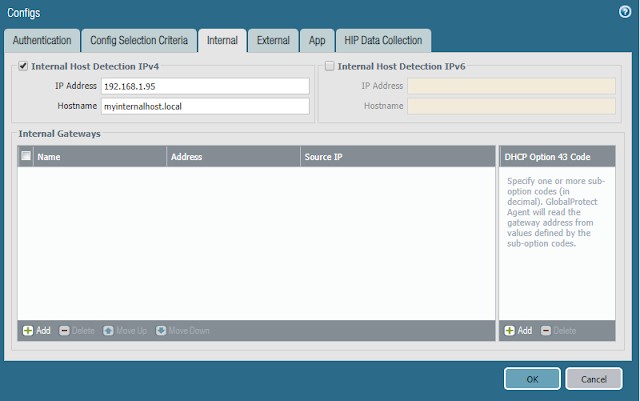
- In the Internal tab
- Enable Internal Host Detection IPv4
- Enter an IP Address of resource that is always available internally
- Enter the Hostname of the IP address to which it resolves
- NOTE: Internal Host Detection uses a reverse lookup to determine whether or not a device is on the internal network in order to establish a VPN tunnel. See this post for additional details if you do not have an internal DNS server.
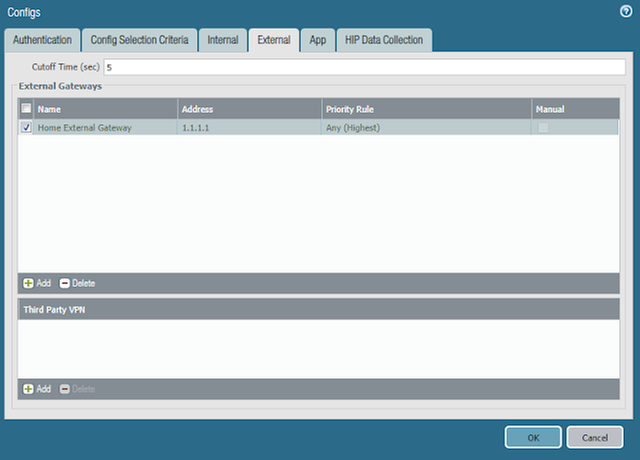
- In the External tab
- Add an External Gateway
- Enter a Name
- Enter the Address to which remote users will connect
- Add an External Gateway
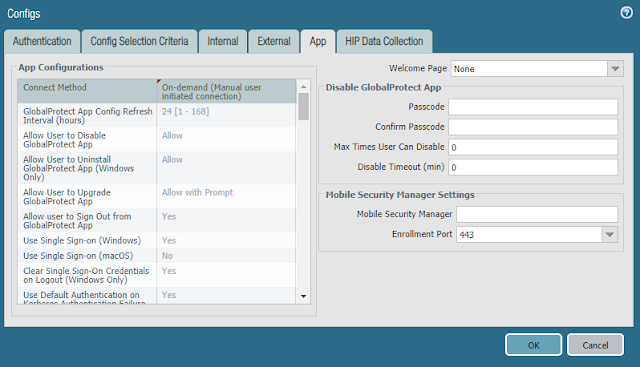
- In the App tab
- Change the Connect Method to On-demand
- Click OK
- NOTE: In subsequent posts, we will be setting the Connect Method to User-Logon (Always On), as that is the recommended best practice
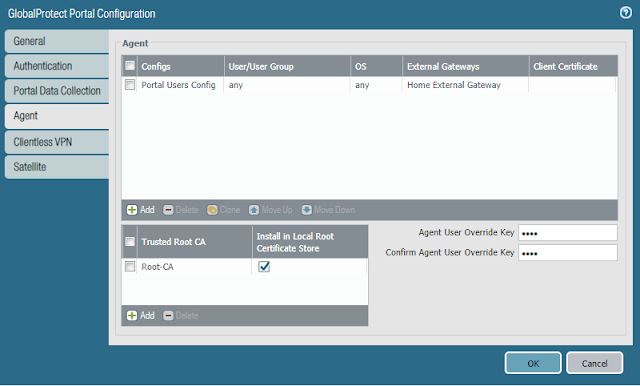
- Back in the Agent tab, click Add under Trusted Root CA
- Add the Root CA
- Check the Install in Local Root Certificate Store
- NOTE: Selecting this option will transparently install the trusted root CA so that we can test SSL Forward Proxy decryption in the future. It is not required in order for GlobalProtect to function.
- Click OK
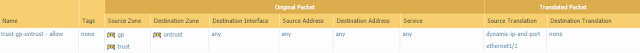
- Navigate to Policies > NAT and add the gp zone you created previously to your source NAT rule so that users in the gp zone can get out to the Internet
- Navigate to Policies > Security and add security policy rules so that users in the gp zone can access internal as well as public resources
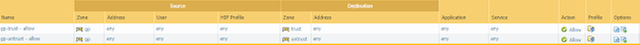
- Navigate to Policies > Security and add a security policy rule that allows remote users to access GlobalProtect portal
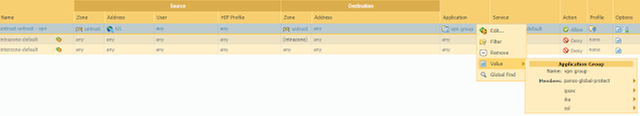
- Commit the configuration
You should now be able to log into the portal, download and install the GlobalProtect App, and test connectivity.
In my next post, "GlobalProtect: Expanded Setup," we will make changes to the configuration to include different forms of authentication and add an internal gateway.
- 27301 Views
- 1 comments
- 6 Likes
- Host Compliance Service for GlobalProtect in GlobalProtect Articles
- Seamless Single Sign-On with Palo Alto Networks GlobalProtect in GlobalProtect Articles
- GlobalProtect Support for DHCP-Based IP Address Assignments in GlobalProtect Articles
- GlobalProtect Portal Internal Gateway Not Filtering by Source IP Address in GlobalProtect Articles
- Updates on Certificates for GlobalProtect App Log Collection Feature in GlobalProtect Articles
-
DHCP
1 -
ESXi
1 -
Global Protect
1 -
GlobalProtect
19 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect-COVID19
12 -
GlobalProtect-Resources
9 -
Layer 3
1 -
NGFW Configuration
11 -
Prisma Access
1 -
PrismaAccess-COVID19
1 -
VM-Series
1
- Previous
- Next




