- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
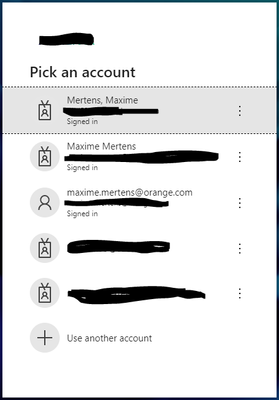
Azure SAML double windows to select account
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Azure SAML double windows to select account
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2023 06:36 PM
Hello everyone,
We have configured a new set-up for GlobalProtect which use Auzre SAML authentication and Microsoft Authenticator
It's all working fine with the exception of this weird behavior:
- User connect to the portal with SAML authentication
- A window open for the user to select an AD account to use
- User select account
- New window open asking to ack the MS authenticator prompt, user accept.
- Authentication is successful
(So far so good)
- Then a second window asking to select an account appears
- User select the account and is logged in.
We want to get rid of that second windows but after scouring all the resources I could find, I can't figure out where this windows is coming from. Assuming it's the gateway.
As a test , I removed the authentication on the external gateway, but access is not working at all.
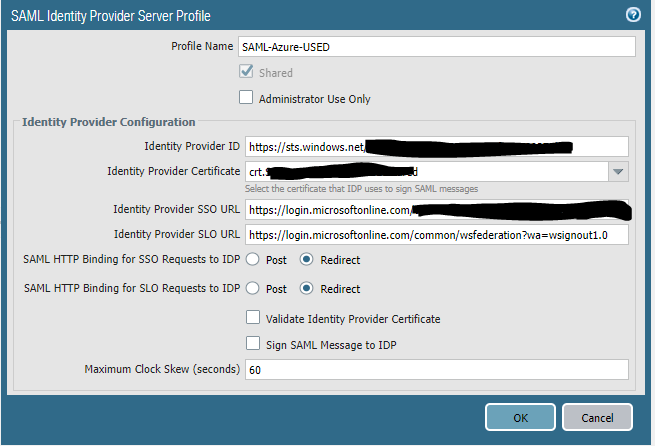
SAML is configured with Single sign-out.
User is using GP 5.2.11-10
Palo is 9.1.11-h3
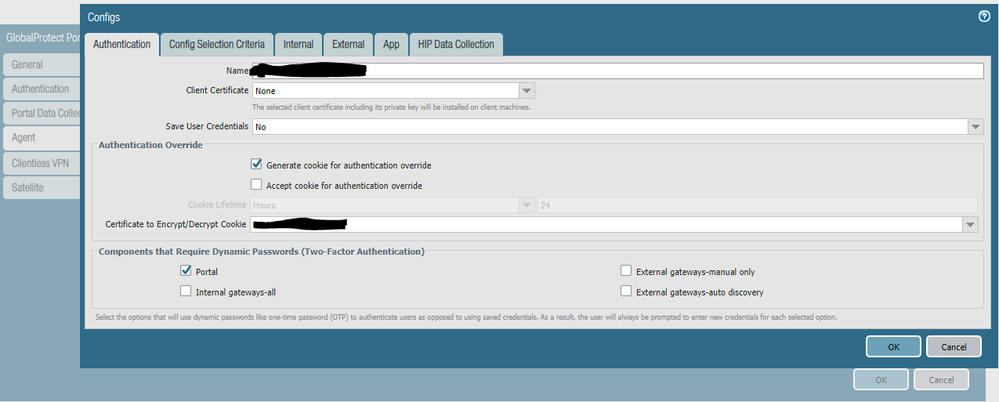
Portal is configured to generate a cookie for auth override.
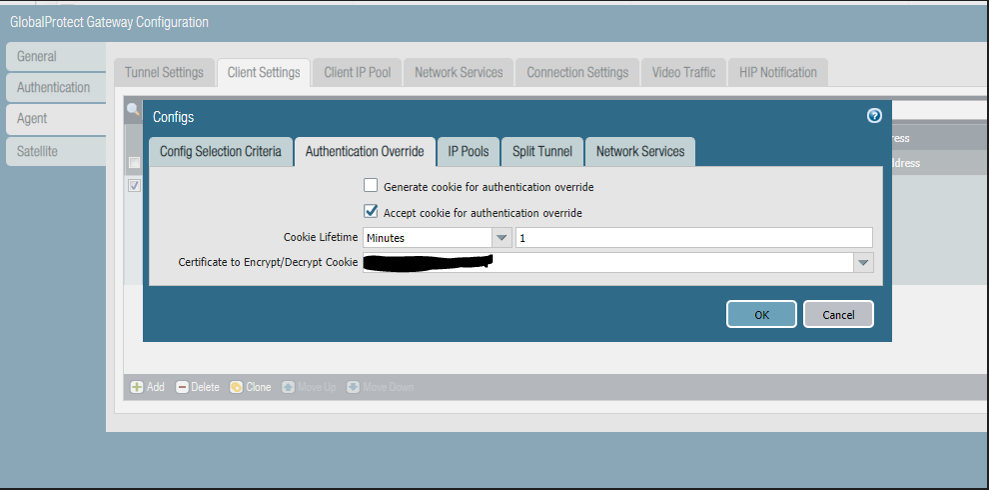
Gateway is configured to accept the cookie.
Certificate to encrypt/decrypt on Portal and Gateway is the same.
Use Default Browser for SAML Authentication in the App config is set to NO
Did anyone faced the same behavior and manage to have it fixed?
A ticket has been opened, and suggest to Validate Identity Provider Certificate in the SAML server profile. I don't see how it will solve the issue as the authentication is successful.
Best regards,
Max
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-30-2023 09:07 PM - edited 01-30-2023 09:09 PM
So,
We redid a battery of test today and found a work around.
1- When the portal and gateway are set to generate and accept cookie, the double prompt is happening.
Happening as well if Portal is set to generate and Gateway to accept.
2- When the portal is set to only accept and the gateway to generate and accept. Two prompt prompt the first time, then after the cookie is generated by the gateway, it can be used by the portal for the authentication.
The client is not able to read the cookie generated by the portal. It's been generated, can see it in the folder C:\Users\%USERNAME%\AppData\Local\Palo Alto Networks\GlobalProtect but it can't be read.
(P5076-T10004)Debug(9092): 01/31/23 14:36:11:444 ----Portal Login starts----
(P5076-T10004)Debug(2284): 01/31/23 14:36:11:444 Failed to open file C:\Users\USER\AppData\Local\Palo Alto Networks\GlobalProtect\PanPUAC_xxxxxxxxxxxxxxxxxxxx.dat
This is a know bug by Palo and expected to be fixed in 10.2.4
I still have to try with GP client version 5.2.12 with Portal generating the cookie and the Gateway accepting it.
Work around for now is to set the lifetime of the cookie to a few days or a year (max value). In this case users will only have the two prompts for account selection the first time they connect or until the cookie is no longer valid.
Thank you all for your help.
Edit: We did remove the AD group from Portal, Gateway and Auth profile to no avail. It was the work around that Palo provided but didn't work in our case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2023 06:42 PM
To clarify the double windows, it's not coming from the GlobalProtect client.
It's a Windows window like this one
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2023 07:03 PM
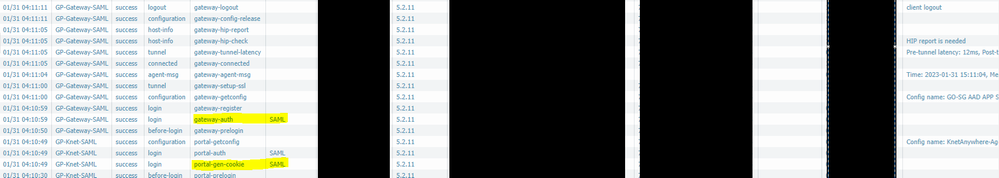
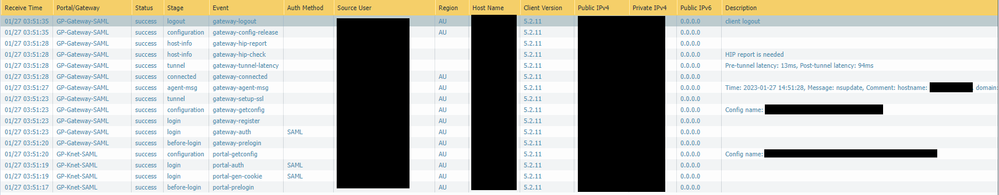
Go to Monitor > Logs > GlobalProtect, filter out login events ( stage eq login ) and check "Auth Method" column.
If cookie works then Portal auth method should show SAML and gateway Cookie.
New cookie is generated only if old cookie is expired.
Try to change portal cookie lifetime to 1 minute as well.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2023 08:22 PM
Hello Raido,
Thanks for your answer.
Both Portal and Gateway shows "SAML" for auth method, so I assume the cookie is not used for the gateway authentication.
Portal and GW have the same Client authentication with the same authentication profile.
I did try to remove the Client authentication on the Gateway but then the user was not able to connect at all.
Kind regards,
Max
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2023 08:37 PM
As step 1 try newer GlobalProtect agent.
You are using 5.2.11
For example 5.2.12 had some GlobalProtect auth and SAML issues fixed.
Like
If newer agent don't fix it then try to enable cookie generation on gateway temporarily and set accept time a bit longer (like 5 mins).
Connect to Globalprotect.
Disconnect from GlobalProtect.
Connect to GlobalProtect again.
Was cookie used during second connection attempt if cookie was first generated by gateway itself?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2023 08:43 PM
Let me try that, I'll update the topic with result
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2023 11:17 PM
Did you add both fqdn's (portal and gateway) to the SAML config (on Microsoft)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-29-2023 11:45 PM
Hello,
For the new version, It'll be installed tomorrow, user doesn't have admin right.
We tested the cookie generation and accept on the gateway to no avail. Still see both SAML on the auth method.
@JoergSchuetter , the FQND is used on the SAML config on Azure. That FQDN is resolving to the IP of the Portal and Gateway.
On the PAN GPS log, I see this entry in the ----Gateway Pre-login starts---- part:
(P5076-T16812)Debug(2284): 01/30/23 16:29:13:678 Failed to open file C:\Users\XXX\AppData\Local\Palo Alto Networks\GlobalProtect\PanPUAC_xxxxxxxxxxx.dat
That file is PanPUAC.dat file is the Portal authentication cookie, we checked the access right of the folder and it looks ok. The user has full control to the folder.
Kind regards,
Maxime
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-30-2023 09:07 PM - edited 01-30-2023 09:09 PM
So,
We redid a battery of test today and found a work around.
1- When the portal and gateway are set to generate and accept cookie, the double prompt is happening.
Happening as well if Portal is set to generate and Gateway to accept.
2- When the portal is set to only accept and the gateway to generate and accept. Two prompt prompt the first time, then after the cookie is generated by the gateway, it can be used by the portal for the authentication.
The client is not able to read the cookie generated by the portal. It's been generated, can see it in the folder C:\Users\%USERNAME%\AppData\Local\Palo Alto Networks\GlobalProtect but it can't be read.
(P5076-T10004)Debug(9092): 01/31/23 14:36:11:444 ----Portal Login starts----
(P5076-T10004)Debug(2284): 01/31/23 14:36:11:444 Failed to open file C:\Users\USER\AppData\Local\Palo Alto Networks\GlobalProtect\PanPUAC_xxxxxxxxxxxxxxxxxxxx.dat
This is a know bug by Palo and expected to be fixed in 10.2.4
I still have to try with GP client version 5.2.12 with Portal generating the cookie and the Gateway accepting it.
Work around for now is to set the lifetime of the cookie to a few days or a year (max value). In this case users will only have the two prompts for account selection the first time they connect or until the cookie is no longer valid.
Thank you all for your help.
Edit: We did remove the AD group from Portal, Gateway and Auth profile to no avail. It was the work around that Palo provided but didn't work in our case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-14-2023 07:28 PM
GP version 5.2.12 is the same behavior. Will retest after upgrade PANOS to 9.1.15-h1
- 1 accepted solution
- 9111 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- New cert GP cert prompt for people testing Yubikeys for windows logon in GlobalProtect Discussions
- Cannot log into global protect, testing configuration on EVE-NG in GlobalProtect Discussions
- CIE agent not connecting to AD servers in Cloud Identity Engine Discussions
- Clientless VPN and Remote Desktop in Next-Generation Firewall Discussions
- User-ID Integration with AD Failing (Access Denied / Kerberos Errors – Event ID 10036) in Next-Generation Firewall Discussions