- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to decrypt ESP IPSEC packet using wireshark
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- How to decrypt ESP IPSEC packet using wireshark
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
How to decrypt ESP IPSEC packet using wireshark
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-28-2023 01:13 AM
Sometimes you want to see how the tunnel mode encapsulation occurs, especially when using GRE over IPsec and VTI IPsec and you would like to decrypt the ESP or IPSEC packet to see how packet is encaspulated on both scenarios (GRE over IPsec and VTI IPsec, especially for studying or may be for troubleshooting.
Below how to do it:
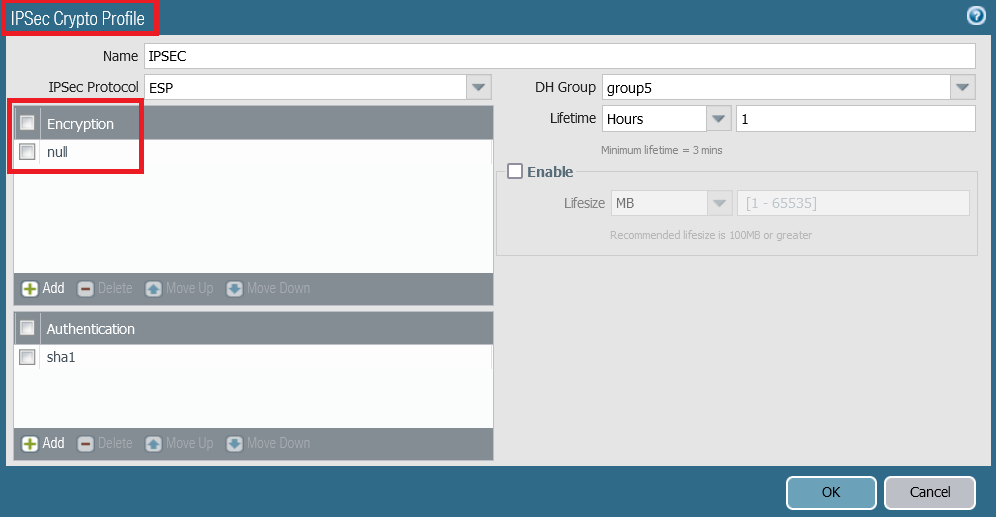
Configue the ESP encryption with null in the IPsec Crypto Profile.
Run the packet capture on PaloAlto to capture the PCAP File.
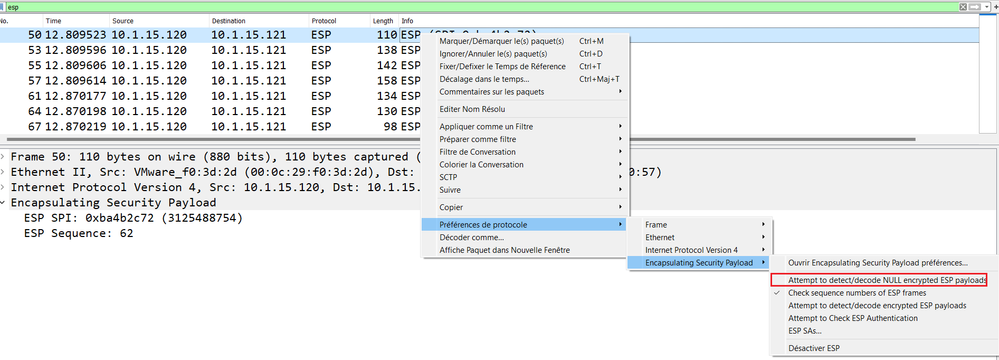
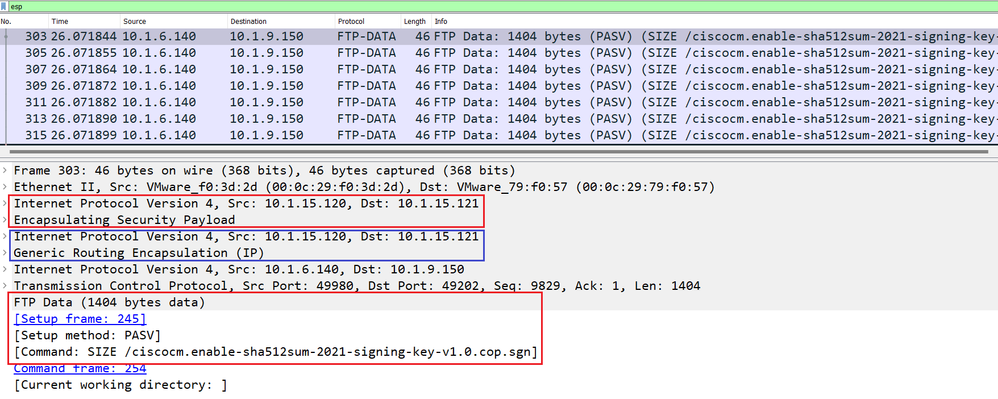
Open wireshark. right-click on the ESP packet, in this scenario the ESP SA from the source 10.1.15.120 to the destination 10.1.15.121. Under the Protocol Preferences, check the the option "Attempt to Detect/Decode NULL Encrypted ESP Payload" as shown below.
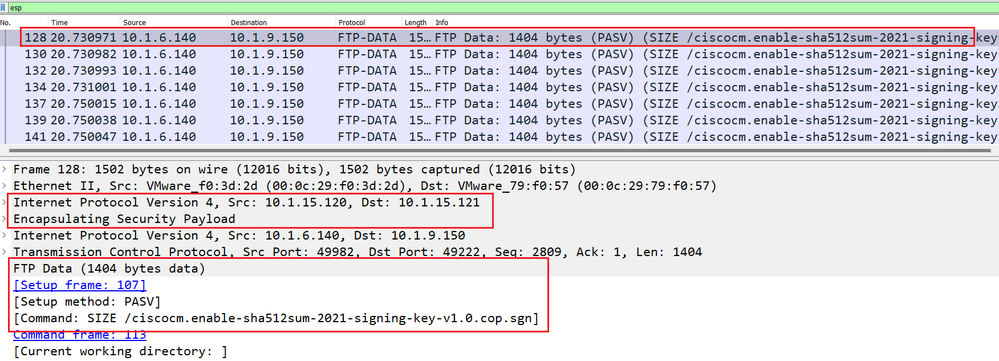
Finally you can see the ESP Packet payload in clear text:
ESP Packet with VTI IPsec
ESP Packet with GRE Over IPsec
- 8861 Views
- 0 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- How to trigger a "Response page" on Palo Alto NGFWs using URL filtering & Decryption in Next-Generation Firewall Discussions
- NGFW Global Protect 6.2.7 Global Counters Negotiation Error TLS 1.3 MAC-OS in GlobalProtect Discussions
- Byte swapping needed on packet captures taken from tunnel interfaces in Next-Generation Firewall Discussions
- How can I extract the IKEv2 encryption keys SK_ei and SK_er on PAN-OS 11.2? in Next-Generation Firewall Discussions