- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Packets dropped: forwarded to different zone
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Packets dropped: forwarded to different zone
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Packets dropped: forwarded to different zone
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2024 02:22 AM
We have a PaloAlto firewall that we have configured differrent zones, everything is working fine, except for a specific traffic between IP 10.40.129.49 and 172.26.2.58. The 10.40.129.49 is located on a subnet directly in a zone defined on the firewall, 172.26.2.58 is a remote host over a WAN link going via another zone on the firewall. Traffic to and from both IPs is reaching the firewall but does not get through it despite having a Policy that is allowing the traffic. Upon doing further troubleshooting, it looks like the firewall is dropping the packets with a message that "Packets dropped: forwarded to different zone"
See the test below:
vnkhwazi@PDC_EDGE_FW_P(active)> debug dataplane packet-diag set filter match source 10.40.129.49 destination 172.26.2.58
vnkhwazi@PDC_EDGE_FW_P(active)> debug dataplane packet-diag set filter on
debug packet filter: on
vnkhwazi@PDC_EDGE_FW_P(active)> show counter global filter packet-filter yes delta yes severity drop
Global counters:
Elapsed time since last sampling: 19.244 seconds
name value rate severity category aspect description
----------------------------------------------------------------------------------------------------
flow_fwd_zonechange 8 0 drop flow forward Packets dropped: forwarded to different zone
------------------------------------------------------------------------------------------------------
Total counters shown: 1
-------------------------------------------------------------------------------------------------------
What could be the cause of this?
Regards.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2024 03:29 AM
this is typically a routing problem (concentrated on the reply packets)
some of the most common issues are
-either you don't have routes for both subnets set to the right destination interface (connected subnets don't need that, remote do, subnets that are 'local' but don't have an IP on the firewall interface also need this)
-or if you're using policy based forwarding, symmetric return was not enabled and reply packets are being sent out a different interface due to routing
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2024 04:49 AM
i am able to ping between the two IPs, but SIP (UDP 5060) is the one failing.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2024 06:40 AM - edited 01-17-2024 06:41 AM
aha
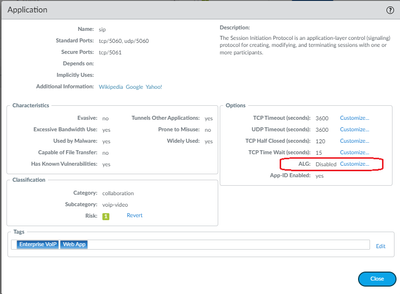
sip uses an ALG, maybe that's derailing the whole process
try disabling the ALG by going to objects > applications, find sip and open it. on the right hand side you'll see the ALG
PANgurus - Strata & Prisma Access specialist
- 3389 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- port issue / nmapping in Next-Generation Firewall Discussions
- Question about HTTPS log forwarding to Microsoft Sentinel in Next-Generation Firewall Discussions
- GP connction failed in GlobalProtect Discussions
- Issue after onboard Azure VM into SCM in Strata Cloud Manager
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud