- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
- LIVEcommunity
- Products
- Cloud Native Application Protection
- Prisma Cloud
- Prisma Cloud Articles
- Who rated this article
Who rated this article
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-27-2022 03:59 PM - edited 11-13-2024 02:44 PM
By Brandon Goldstein, Senior Customer Success Engineer
Overview
This guide describes how to configure agentless vulnerability and compliance scanning for virtual machines in Microsoft Azure subscriptions.
This article will use a credential dedicated to the agentless scanning process.
Before You Begin
To follow along, you will need:
- A self-hosted Prisma Cloud Compute console running v32 or later.
- Permission in your Compute console to create Cloud Account credentials, view console logs, the vulnerability monitor and the compliance monitor.
- Sufficient permissions in your Azure subscription to create service principals, custom roles and role assignments
- The Azure CLI installed and authenticated with the subscription you want to scan
A helpful list of reference material can be found at the end of this document.
Configuration
Procedure 1: Create a New Azure Service Principal
Create a Service Principal dedicated to the agentless scanning procedure.
Step 1: Using the Azure CLI, execute the command below. Replace the name and subscription ID with your own custom values:
az ad sp create-for-rbac --name your-service-principal-name name --scopes /subscriptions/your-subscription-id-here --role reader --sdk-auth
You should receive a result as this:
$ az ad sp create-for-rbac --name sp-new-azure-agentless-scanner --scopes /subscriptions/your-subscription-ID --role reader --sdk-auth
Creating 'reader' role assignment under scope '/subscriptions/your-subscription-ID'
The output includes credentials that you must protect. Be sure that you do not include these credentials in your code or check
the credentials into your source control. For more information, see https://aka.ms/azadsp-cli
{
"clientId": "service-principal-client-ID",
"clientSecret": "service-principal-client-secret",
"subscriptionId": "subscription-ID",
"tenantId": "tenant-ID",
"activeDirectoryEndpointUrl": "https://login.microsoftonline.com",
"resourceManagerEndpointUrl": "https://management.azure.com/",
"activeDirectoryGraphResourceId": "https://graph.windows.net/",
"sqlManagementEndpointUrl": "https://management.core.windows.net:8443/",
"galleryEndpointUrl": "https://gallery.azure.com/",
"managementEndpointUrl": "https://management.core.windows.net/"
}
Procedure 2: Configure the Compute Cloud Credentials
We need to configure the cloud credentials in order to get the permissions template assigned to the service principal.
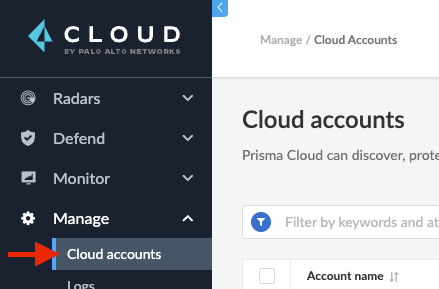
Step 1: Login to the Compute console and navigate to Manage > Cloud Accounts
Figure 1: Manage/Cloud Accounts_PaloAltoNetworks
Step 2: Click Add Account.
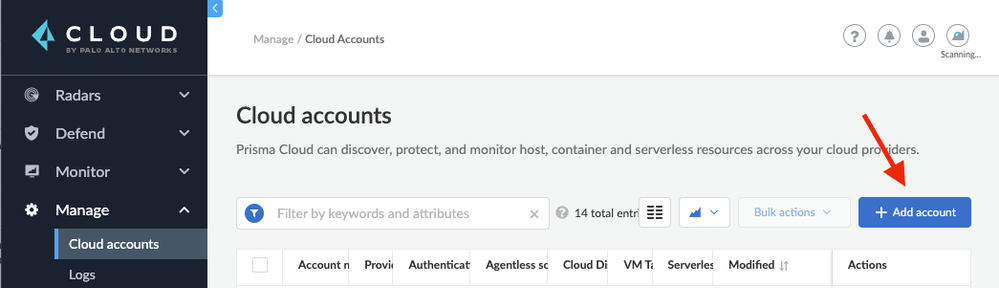
Figure 2: Add Account_PaloAltoNetworks
Step 3: Select Azure from the “Select Cloud Provider” dropdown menu, enter a name, a description (optional), and then select the “Service Key” radio button.
Step 4: Copy and paste the entire JSON output from Step 1 into the “Service Key” field. Then click “Next”
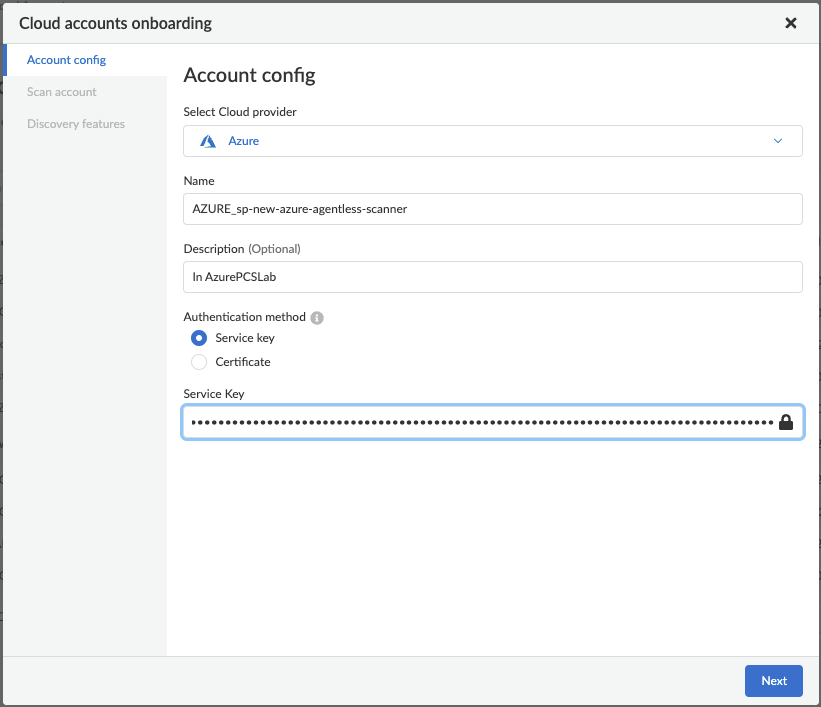
Figure 3: Account Config_PaloAltoNetworks
Step 5: Enter your Console URL and port, then click “Download” to get a file archive with the permission templates.
Note: you will receive an archive similar to this .tar.gz
It will have the following .json files in it:

Figure 4: Scan Account_PaloAltoNetworks
- Role_assignment.json
- Role_definition.json
Step 6: All of the Advanced Settings are optional.
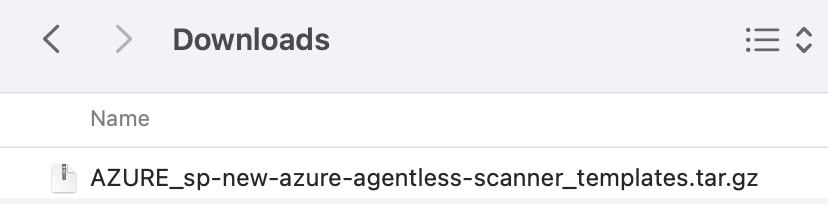
Figure 5: Downloads_PaloAltoNetworks
Step 7: Click “Next” to proceed to the next section.
Step 8: You can leave Cloud Discovery disabled because this credential will not have sufficient permissions to perform Cloud Discovery.
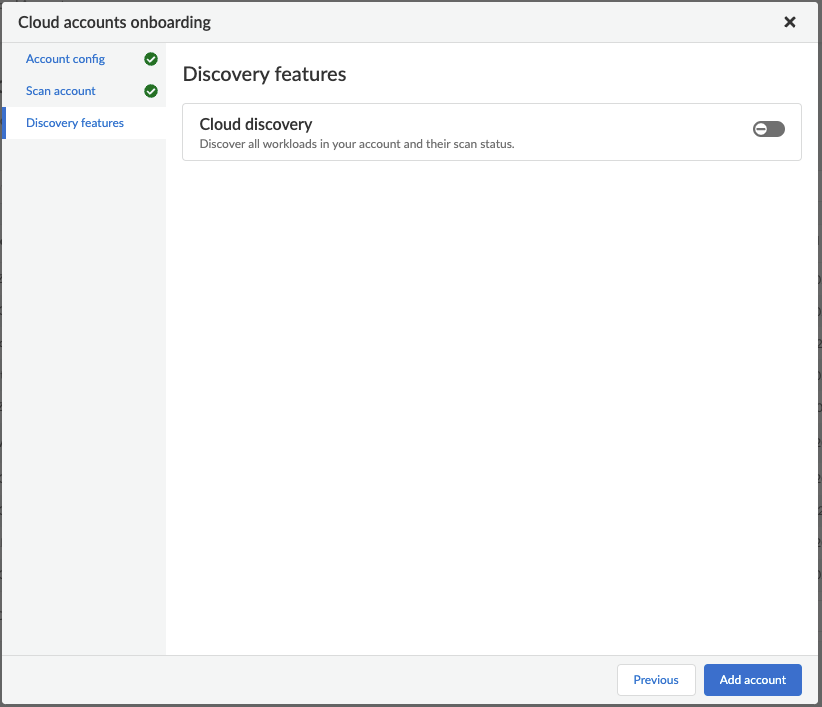
Figure 6: Cloud Discovery_PaloAltoNetworks
Step 9: Then click “Add Account” to complete the credential setup within Compute. You will find that the new credential has a green checkmark under “Agentless scan”; however, we still aren’t ready for a successful scan.
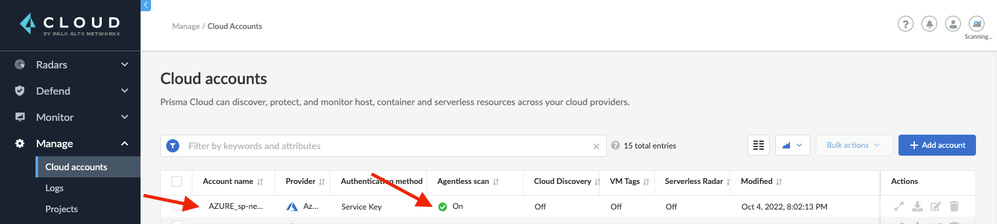
Figure 7: Add Accounts_PaloAltoNetworks
Procedure 3: Create the Custom Role for Azure Agentless Scanning
Step 1: Use the role_definition.json file to create a new custom role.
az role definition create --role-definition "role_definition.json"
You should receive a result like this:
$ az role definition create --role-definition "role_definition.json"
The underlying Active Directory Graph API will be replaced by Microsoft Graph API in Azure CLI 2.37.0. Please carefully review all breaking changes introduced during this migration:
https://docs.microsoft.com/cli/azure/microsoft-graph-migration
{
"assignableScopes": [
"/subscriptions/your-subscription-ID"
],
"description": "Can create and manage VMs, snapshots, disks, network interfaces and security groups",
"id": "/subscriptions/your-subscription-ID/providers/Microsoft.Authorization/roleDefinitions/05504b7f-8d89-49ae-9a9e-e8e075185423",
"name": "05504b7f-8d89-49ae-9a9e-e8e075185423",
"permissions": [
{
"actions": [
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Resources/subscriptions/resourceGroups/write",
"Microsoft.Network/networkInterfaces/read",
…
"Microsoft.Compute/virtualMachines/write",
"Microsoft.Compute/virtualMachines/delete",
"Microsoft.Compute/virtualMachines/instanceView/read"
],
"dataActions": [],
"notActions": [],
"notDataActions": []
}
],
"roleName": "Prisma Cloud Compute Agentless Scanner",
"roleType": "CustomRole",
"type": "Microsoft.Authorization/roleDefinitions"
}
Step 2: Assign the new role to the new service principal.
az role assignment create --assignee "new-service-principal-id" --role "Prisma Cloud Compute Agentless Scanner" --scope "/subscriptions/your-subscription-id"
You should receive a result like this:
$ az role assignment create --assignee "new-service-principal-ID" --role "Prisma Cloud Compute Agentless Scanner" --scope "/subscriptions/new-service-principal-ID"
The underlying Active Directory Graph API will be replaced by Microsoft Graph API in Azure CLI 2.37.0. Please carefully review all breaking changes introduced during this migration:
https://docs.microsoft.com/cli/azure/microsoft-graph-migration
{
"canDelegate": null,
"condition": null,
"conditionVersion": null,
"description": null,
"id": "/subscriptions/new-service-principal-ID/providers/Microsoft.Authorization/roleAssignments/9d3943e7-fe1f-4230-82cf-2cfc6719196a",
"name": "9d3943e7-fe1f-4230-82cf-2cfc6719196a",
"principalId": "e4856716-f8e1-4c8c-9867-0d333a1dccf0",
"principalType": "ServicePrincipal",
"roleDefinitionId": "/subscriptions/new-service-principal-ID/providers/Microsoft.Authorization/roleDefinitions/05504b7f-8d89-49ae-9a9e-e8e075185423",
"scope": "/subscriptions/new-service-principal-ID",
"type": "Microsoft.Authorization/roleAssignments"
}
Procedure 4: Trigger the first agentless scan
Step 1: Return to the Compute console and the Cloud Accounts page.
Step 2: Click the icon for “Trigger Discovery or Scan Agentless” to open a dropdown menu and then click “Start Agentless scan”.
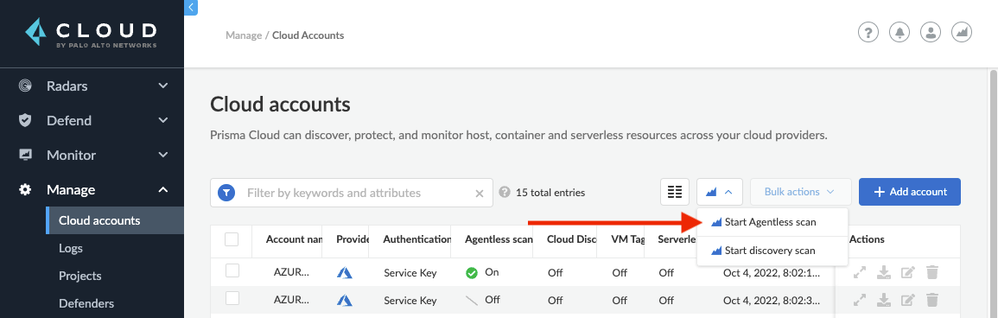
Figure 8: Start Agentless Scanning_PaloAltoNetworks
Figure 9: Trigger Discovery_PaloAltoNetworks
Step 3: You should find the activity and progress for Azure agentless scanning in the top right corner of the console window.

Figure 10: Scanning Status_PaloAltoNetworks
Step 4: You can also search for the keyword “scan” in the Virtual Machine list within the Azure console to confirm that the temporary scanners have been created.
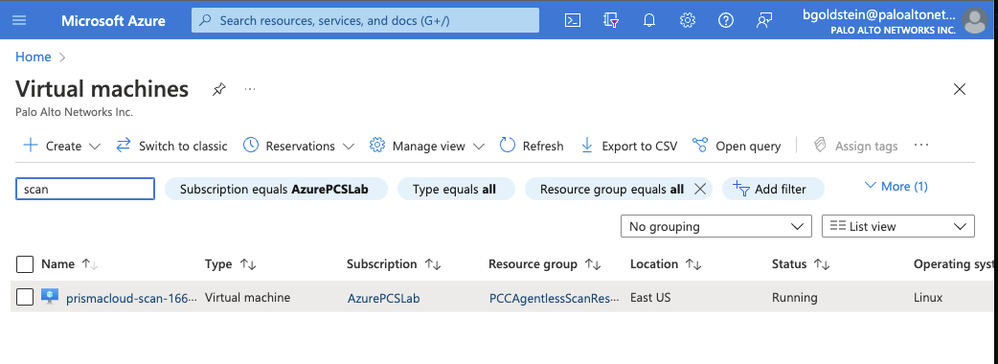
Figure 11: Scanning Virtual Machines_PaloAltoNetworks
Step 5: Eventually you will see more progress in the Compute console status.
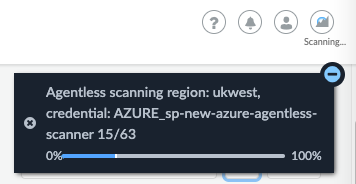
Figure 12: Scanning Progress_PaloAltoNetworks
Step 6: View the console logs at Manage > Logs > Console and search for “agentless”
to see the related API activity.
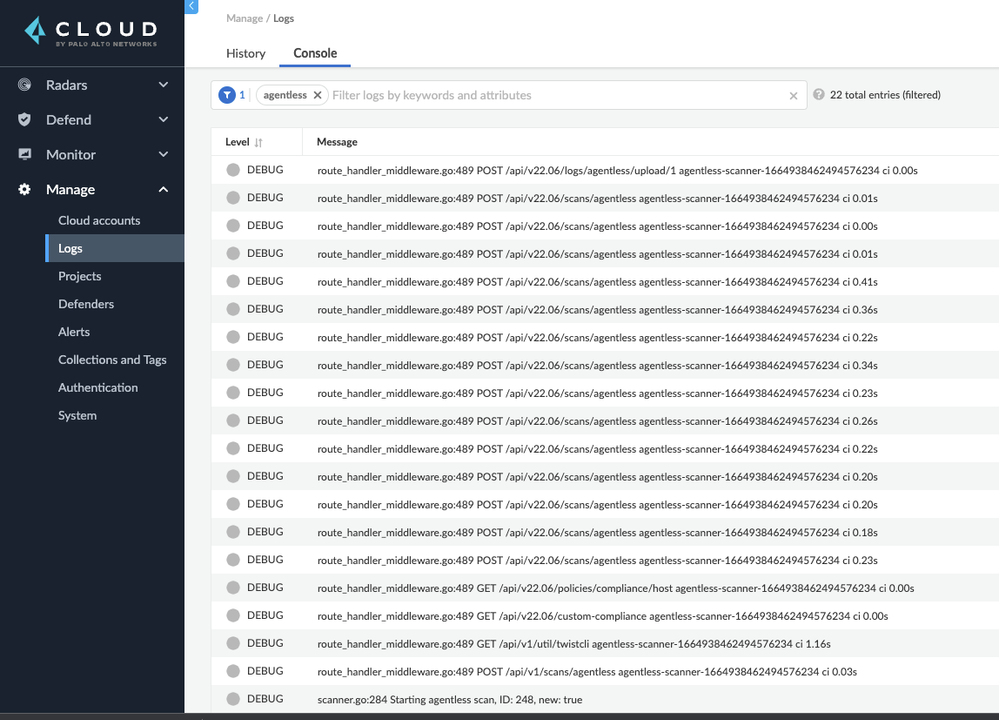
Figure 13: View Console Logs_PaloAltoNetworks
Procedure 5: Confirm Success!
Step 1: In the Compute console, navigate to Monitor > Vulnerabilities > Hosts then select the Hosts subsection. Set the filter to “Scanned by: Agentless” and add a VM name or keyword to the search for virtual machines which are to be scanned.
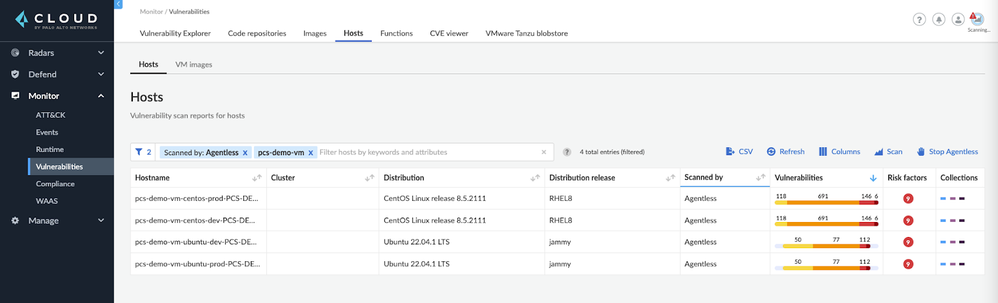
Figure 14: Search Virtual Machines_PaloAltoNetworks
Step 2: Click on one of the entries to see the scan details. Check the scan time to see that it was recent. You will also be able to confirm that it was discovered in Azure.
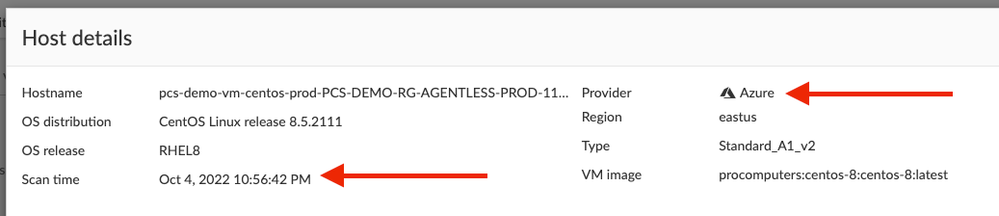
Figure 15: Scan Details_PaloAltoNetworks
Step 3: Check the Compliance Monitor under Monitor > Compliance > Hosts and the Hosts subsection to ensure you are getting valuable results there as well!
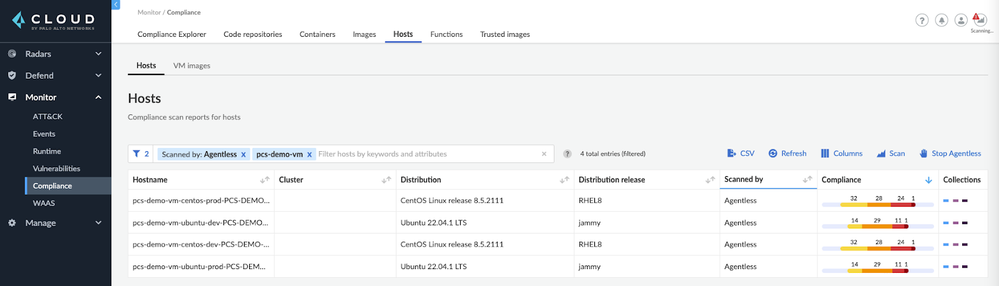
Figure 16: Compliance Monitor_PaloAltoNetworks
Procedure 6: You’re Done! You have successfully configured and completed agentless virtual machine scanning of your Azure subscription!
Related Information
- Compute - Agentless Scanning
- Compute - Azure Agentless Permissions
- Compute - Create a Role and a Service Principal in Azure
- Microsoft - How to install the Azure CLI
- Microsoft - Create an Azure service principal with the Azure CLI
- Microsoft - Create or update Azure custom roles using Azure CLI
- Assign Azure roles using Azure CLI
About the Author
Brandon Goldstein is the senior customer success engineer specializing in Prisma Cloud, Next-Generation Firewall, AWS, Azure, GCP, containers and Kubernetes. They use collaborative approaches to break down complex problems into solutions for global enterprise customers and leverage their multi-industry knowledge to inspire success.