- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSH Proxy decryption disables vulnerability protection?
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- SSH Proxy decryption disables vulnerability protection?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSH Proxy decryption disables vulnerability protection?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2021 01:56 AM
Hello everyone,
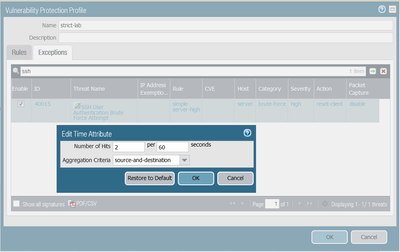
I'm doing some tests with decryption and vulnerability protection. I configured NAT and security policies to permit ssh access to an internal ssh server from the outside and I attached a vulnerability protection profile to the policy. In the vulnerability protection profile I set an exception to block bruteforce login attacks after 2 failed attempts:
This configuration works fine and connections are reset after 2 failed login. Anyway, if I add a SSH decryption policy (SSH proxy) to this connection, the bruteforce login signature is no more triggered by the failed login attempts, so it is no more effective.
Is this an issue or is it "by design", due to the fact that the firewall acts as a man in the middle for the ssh connections?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2021 03:58 AM
I opened a case with the support and they confirmed this issue. Waiting for their research and feedback.
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-24-2021 02:22 AM
The engineering team confirmed that this is an expected behavior. This is their explanation:
In case SSH-proxy is enabled, the signature 31914 will act on decrypted traffic. Hence, this sig will not trigger because it can not detect the pattern of the failed authentication in the decrypted traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2023 09:45 AM - edited 03-10-2023 09:48 AM
I've got an interesting variation on this issue. I have an SSH proxy that inspects all incoming SSH traffic going to various SFTP servers. I have one particular SFTP server that has a security rule that allows SSH, but this one rule ( to just one server) also has a VPP with the same 40015 exception with the action set to alert. Despite the SSH proxy rule covering all incoming SSH, any SSH traffic to that server is showing as NOT decrypted. All the other traffic hitting any other security rules without that exception shows as decrypted. Would adding the Brute Force exception cause the firewall to not decrypt the traffic so the exception can work?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2023 11:52 AM
Hi @GM001 ,
SSH proxy only allows the detection and block (if configured in the security policy) of the ssh-tunnel App-ID. https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/decryption/decryption-concepts/ssh-proxy "The firewall can’t decrypt traffic inside an SSH tunnel." It only identifies the channel type.
Thanks,
Tom
- 5690 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Upgrade from Basic Threat Prevention to Advanced Threat Prevention in Advanced Threat Prevention Discussions
- High alert with signature in Advanced Threat Prevention Discussions
- security profile malfunction detection in Advanced Threat Prevention Discussions
- Vulnerability Protection Profile in Advanced Threat Prevention Discussions