
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Written by John Chavanne and Rob Baccus
In today's cloud world there are a number of challenges in securing the resources and applications running in the cloud. One of these is the permissions that both users and objects have to sensitive information and access to others' resources. How do you, as a security professional, know when an attacker can use your own over permissive roles and accounts to access an S3 bucket containing personal customer information? Palo Alto Networks Unit 42 team has done extensive research in this area as well as helped customers who have suffered from breaches in the cloud. The Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface highlights examples where attackers exfiltrated cloud credentials, escalated privileges, and exfiltrated data from many database tables and storage buckets. In this article, we will focus on some of the most important best practices for Cloud Infrastructure Entitlement Management (CIEM) and Identity Access Management (IAM) Security for cloud applications, resources, and services.
This blog will provide you with:
Managing cloud IAM is complex and challenging for any organization. Having a very clear cloud IAM strategy that can be communicated across the organization can go a long way to establishing proper rules and guardrails for how all identities will be managed in the cloud.
It is important to work with various teams in your organization to establish Cloud Infrastructure Entitlement Management (CIEM) and Identity Access Management (IAM) Security best practices and strategies for future changes. Your cloud IAM best practices will need to align with your cloud IAM Strategy such that both security and development teams agree on the best way to secure roles, permissions, and resource access across cloud environments.
The risks that your company will incur if you don't adequately tackle cloud CIEM and IAM Security could be significant, from fines and/or jail time from the SEC (given the new reporting requirements), to brand damage and loss of significant customer trust, to loss of revenue.
An example of neglecting the implementation of an IAM strategy and best practices may lead to the existence of overly permissive roles in source code repositories, such as public GitHub, allowing attackers to discover and exploit credentials for purposes like introducing malware or engaging in nefarious activities within your cloud environments. Catching these risky permissions and roles earlier in the application lifecycle can prevent alerts to the security teams downstream.
Another example of a strong business objective addressed by a cloud IAM Best Practice is the incorporation of Multi-Factor Authentication (MFA) for IAM users. This strategic measure serves as a robust defense, preventing unauthorized access to user accounts and the potential compromise of critical data and infrastructure. Neglecting these best practices could lead to substantial consequences, including downtime for mission critical applications, as illustrated and witnessed during the breaches at MGM and Caesars in late 2023.
Diagram 1 is an example approach to help your teams simplify and visualize a cloud IAM strategy based on your company's unique risks. This approach demonstrates how you can simplify a complex and difficult subject by creating a clear visual representation of the potential risks based on specific business needs and easily share it with other teams.
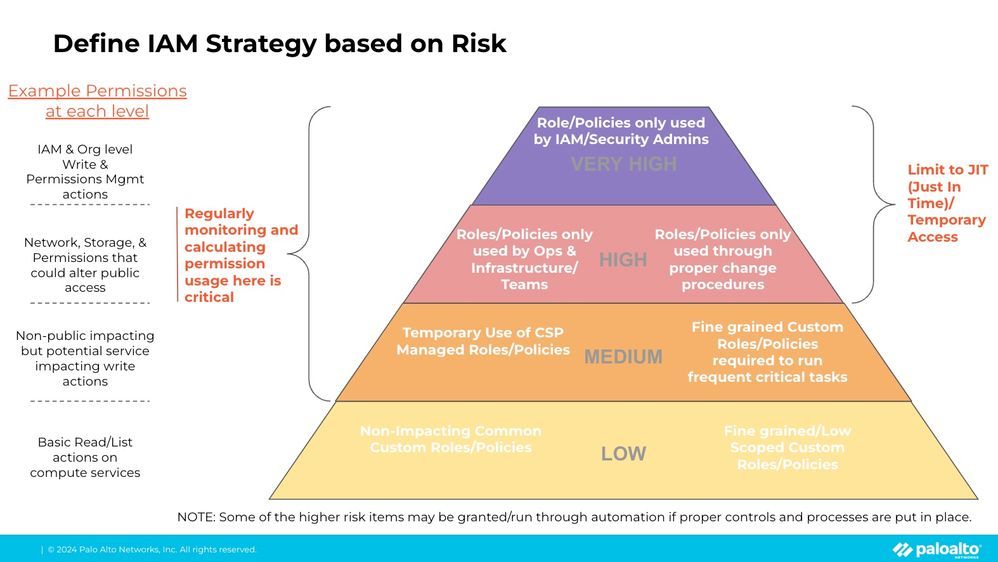
NOTE: Examples in italics are Prisma Cloud RQL examples.
|
Best Practice Category |
Best Practices |
Prisma Cloud Specific Implementation of Best Practices |
Reference/Examples |
|
IAM Controls |
Enforce MFA for cloud identities |
OOB config MFA policies |
|
|
IAM Controls |
Enforce password policies for cloud users |
OOB config Password policies |
|
|
IAM Controls |
Ensure all Users belong to Groups and mitigate use of any directly attached roles or policies. |
Run query in Investigate for all clouds or a specific cloud for granted by entity type of user. |
|
|
IAM Scope Visibility |
Central IdP Visibility across multi-cloud environments |
Support of direct IdP integration |
|
|
Inactive Access |
Identify inactive cloud users. |
OOB config policies & Custom policies. |
|
|
Inactive Access |
Identify inactive access keys/long-standing credentials. |
OOB config policies & Custom policies. |
|
|
Inactive Access |
Identify unused machine accounts (i.e. service accounts, managed identities). |
Custom config policies |
|
|
Risk Prioritization |
Mitigate high priority attack path risks with comprehensive context |
OOB & custom attack path policies |
|
|
Permissions Risk |
Mitigate usage of highly privileged CSP Managed/Built-in roles. |
OOB high privilege role policies. |
|
|
Permissions Risk |
Mitigate unnecessary usage of high risk permissions/privileges for both human and machine identities. |
OOB risky permission policies. |
|
|
Permissions Risk |
Mitigate toxic combination of privilege escalation permissions for both human and machine identities. |
OOB & custom privilege escalation permission policies. |
|
|
Least Privilege |
Mitigate unused permissions/privileges and create least-privilege access policies & roles for both human and machine identities. |
OOB unused permission policies for each CSP for 90 and 7 days and automated generation of least privilege access policies & roles. |
|
|
Least Privilege |
Mitigate wildcard/broad resource access for both human and machine identities. |
OOB wildcard access policies. |
|
|
Least Privilege |
Manage resource access to lower level scopes and avoid role assignments at broad levels (i.e. Orgs, subscriptions, folders, etc.) |
OOB permissions & Custom policies. |
|
|
Cross Account Access |
Mitigate and control cross-account access for both human and machine identities. |
OOB permissions & Custom policies to discover and mitigate identities that have access to accounts/subscriptions/projects/organizations that do not belong to those same entities. |
|
|
Cross Account Access |
Mitigate and control access with organizational conditions |
Custom permission policies |
|
|
Tagging |
Manage and enforce IAM access by tags. |
Custom config & permission policies |
|
|
Identity Anomalies |
Detect & mitigate identity based anomalies |
OOB Anomaly policies |
|
|
Compliance |
Ensure cloud IAM access and configuration meets compliance standards |
Robust OOB compliance standards with identity controls |
|
|
Reporting |
Provides IAM compliance reports for auditing |
OOB compliance reporting |
|
|
Reporting |
Provides reports on top identity risks |
Autogenerate reports from the Command Center |
Managing identities has always been a challenge for companies, and it becomes even more complex in the cloud. Taking proactive steps, like creating and implementing a cloud IAM strategy, helps define controls and guidelines for the organization as it transitions to the cloud. Adopting cloud IAM best practices further reduces risk. Utilizing a powerful tool like Prisma Cloud enables successful implementation and maintenance of the strategy and best practices.
This blog post was intended to help get you started on improving your security posture when it comes to managing your cloud identities. Your cloud identity security journey should not end here though. Identities and their credentials are used throughout cloud environments, to access sensitive data, run CI/CD pipelines, automation activities, and can be found embedded in code, VMs, containers, code repositories. Prisma Cloud has the most robust and comprehensive approach when it comes to protecting your applications, data, and identities. Attackers continue to become more sophisticated and use automation and AI to launch their attacks at faster and faster speeds. Taking an in-depth approach such as described in the blog: Mitigate Cloud Breaches With a Holistic Approach to Cloud Identity and Access will help you continue to learn more about how you can further protect your company from a breach.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 4 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |
| User | Likes Count |
|---|---|
| 7 | |
| 4 | |
| 2 | |
| 2 | |
| 2 |




