- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Exclusion criteria import
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Exclusion criteria import
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2022 09:31 AM
Hi all.
Does anyone know of a way - or a work around for the following situation.
I have a long list (about 700) IPs that I want to create an alert exclusion from. These are external scanners that our firewall blocks and we get a large amount of alerts because of this. I would like to create an alert exclusion so we no longer have to deal with these cluttering up our console. Manually entering 700 IPs into the Remote IP criteria field is not an option. Is there a way to get all the IPs into that criteria, or a way to silence these alerts in another way? I would prefer not to use CIDR ranges as I need a little more granularity than that.
Thanks!
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2022 06:01 PM
Hi @RicardoWaffle ,
You could use an EDL -> https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/policy/use-an-external-dynamic-list-in-po... with the 700 IP addresses and add them to a block security rule (source address) with logging disabled. The cool thing about an EDL is that updates are pushed to the security policy without the need for a commit.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-28-2022 02:05 AM
Hi @RicardoWaffle there are a few workarounds to the ask
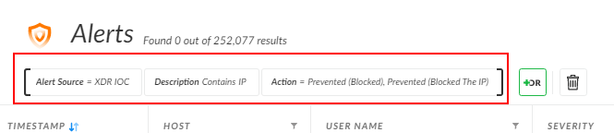
1. import all IP addresses to IOC list, and create an exclusion policy for all alert sources as IOC, description containing IP addresses and action as Prevented (or variations of it, depending on how the firewall events are enumerated in XDR). This will exclude all alerts having the term IP in the description (including the ones that are not in the list of 700 IP's).
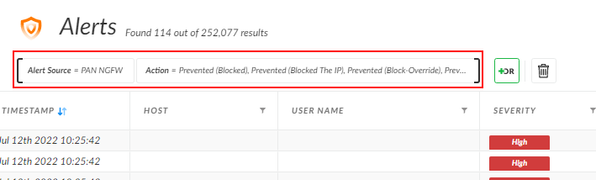
2. a wider action would be exclude all blocked events from the firewall
Give either action a shot depending on your preference, and see what works best for your environment.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2022 06:01 PM
Hi @RicardoWaffle ,
You could use an EDL -> https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/policy/use-an-external-dynamic-list-in-po... with the 700 IP addresses and add them to a block security rule (source address) with logging disabled. The cool thing about an EDL is that updates are pushed to the security policy without the need for a commit.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-28-2022 02:05 AM
Hi @RicardoWaffle there are a few workarounds to the ask
1. import all IP addresses to IOC list, and create an exclusion policy for all alert sources as IOC, description containing IP addresses and action as Prevented (or variations of it, depending on how the firewall events are enumerated in XDR). This will exclude all alerts having the term IP in the description (including the ones that are not in the list of 700 IP's).
2. a wider action would be exclude all blocked events from the firewall
Give either action a shot depending on your preference, and see what works best for your environment.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2022 08:20 AM
Thank you both for your replies. Very helpful!
I'll look into each solution for our environment.
Cheers!
- 2 accepted solutions
- 2935 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!