- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
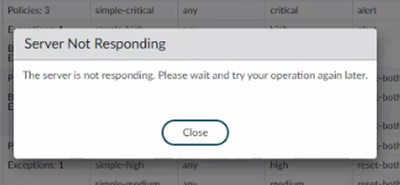
Custom created Anti-Spyware profiles not opening, showing “The server is not responding. Please wait and try your operation again later”.
- LIVEcommunity
- Discussions
- General Topics
- Re: Custom created Anti-Spyware profiles not opening, showing “The server is not responding. Please wait and try your operation again later”.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2022 11:38 PM
Hello all
Model: PA-3220
Firmware version: 10.1.16
- I am not able to open some custom-created Anti-Spyware profiles after moving to 10.1.15-h2 from 10.0.X then upgraded to 10.1.16 (being a preferred version ). showing the below error.
- - default & Strict are there by predefined and are opening perfecty without any issue.
- Created a test policy I am able to open that also.
- Every service had been restarted as the firewall was upgraded.
- Firewall in HA and the passive one shows the same error while checking the same spyware profiles.
- Tried to clone the affected policy and faced the same error.
- Checked the resource usage by show system resources follow and checked that there is no significant spike in the any parameter , more precisely %wa
Do we have any known Bug related to the same?
#paloalto #PA-3220
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2022 06:06 AM
Resolved the issue by fixing the connectivity to https://data.threatvault.paloaltonetworks.com:443/search_by_id by allowing the same in security policy.
The issue was due to curl error: 35 when i clicked on the spyware profile, the firewall was trying to fetch the threat signature in background which was present in botnet exceptions, but due to connection error , it was getting timeout after particular period of time, there was a service route present for paloalto network services therefore i added *.paloaltonetworks.com in the security olicy and allowed it. and it worked fine.
It is not cool to throw an error that device is not responding.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-26-2022 11:22 PM
I am able to figure out that this is due to threat-Id fetch from threat vault, that is not happening.
From show_log_system.txt
2022/06/21 12:01:16 medium general general 0 Could not access threat vault
Later fixed the connectivity because of service route being used
Then from wf_curl.log
2.786 +0300 debug: main(pan_wf_curl.c:931): Device Cert Status node not found, not using device certificate for mTLS with AF2022-06-21 10:51:52.786 +0300 Max timeout: 4
2022-06-21 10:51:52.786 +0300 debug: curl_set_opts(pan_wf_curl.c:280): use_sdb = 0
2022-06-21 10:51:52.805 +0300 debug: main(pan_wf_curl.c:697): full addr: https://data.threatvault.paloaltonetworks.com:443/search_by_id
2022-06-21 10:51:52.806 +0300 debug: main(pan_wf_curl.c:731): dest_addr: data.threatvault.paloaltonetworks.com
2022-06-21 10:51:53.055 +0300 debug: pan_ssl_cloud_ssl_cb(pan_ssl_curl_utils.c:707): set ssl parameters into curl ssl cb
2022-06-21 10:51:53.055 +0300 debug: pan_cryptod_sysd_access_key(pan_cryptod_sysd_api.c:1028): Sending GET: id:client-ssl-cert, flag:4 to cryptod
2022-06-21 10:51:53.056 +0300 debug: pan_cryptod_sysd_access_key(pan_cryptod_sysd_api.c:1037): Send GET msg to cryptod for id:client-ssl-cert successful
2022-06-21 10:51:53.056 +0300 debug: pan_cryptod_sysd_access_key(pan_cryptod_sysd_api.c:1057): Received (for id:client-ssl-cert), key data (len=1849):
2022-06-21 10:51:53.056 +0300 debug: pan_cryptod_dump_buf(pan_cryptod_sysd_api.c:749): [xxx] ...
2022-06-21 10:51:53.056 +0300 debug: pan_cryptod_sysd_access_key(pan_cryptod_sysd_api.c:1028): Sending GET: id:client-ssl-private-key, flag:4 to cryptod
2022-06-21 10:51:53.057 +0300 debug: pan_cryptod_sysd_access_key(pan_cryptod_sysd_api.c:1037): Send GET msg to cryptod for id:client-ssl-private-key successful
2022-06-21 10:51:53.057 +0300 debug: pan_cryptod_sysd_access_key(pan_cryptod_sysd_api.c:1057): Received (for id:client-ssl-private-key), key data (len=1857):
2022-06-21 10:51:53.057 +0300 debug: pan_cryptod_dump_buf(pan_cryptod_sysd_api.c:749): [xxx] ...
2022-06-21 10:51:53.313 +0300 debug: verify_cb(pan_ssl_curl_utils.c:660): Basic Validation of x509 cert is success
2022-06-21 10:51:53.313 +0300 debug: pan_wf_cert_verify(pan_ssl_curl_utils.c:584): pan_wf_cert_verify : cert is valid
2022-06-21 10:51:53.313 +0300 debug: verify_cb(pan_ssl_curl_utils.c:660): Basic Validation of x509 cert is success
2022-06-21 10:51:53.313 +0300 debug: pan_wf_cert_verify(pan_ssl_curl_utils.c:584): pan_wf_cert_verify : cert is valid
2022-06-21 10:51:53.313 +0300 debug: verify_cb(pan_ssl_curl_utils.c:660): Basic Validation of x509 cert is success
2022-06-21 10:51:53.313 +0300 debug: pan_wf_cert_verify(pan_ssl_curl_utils.c:584): pan_wf_cert_verify : cert is valid
2022-06-21 10:51:53.313 +0300 debug: verify_cb(pan_ssl_curl_utils.c:660): Basic Validation of x509 cert is success
2022-06-21 10:51:53.313 +0300 debug: pan_wf_cert_verify(pan_ssl_curl_utils.c:584): pan_wf_cert_verify : cert is valid
2022-06-21 10:51:53.319 +0300 Error: main(pan_wf_curl.c:957): curl error: 35
2022-06-21 10:51:53.319 +0300 sysd worker 0: shutting down
2022-06-21 10:51:53.319 +0300 sysd worker 1: shutting down
2022-06-21 10:51:53.320 +0300 sysd main thread: shutting down
2022-06-21 10:51:53.320 +0300 debug: destruct_ex_url_token_hash(pan_logdb_indexer_v2.c:6438): destruct_ex_url_token_hash
2022-06-21 11:00:27.411 +0300 sysd worker[0]: 7f5190286700: starting up...
2022-06-21 11:00:27.411 +0300 sysd worker[1]: 7f518fe85700: starting up...
2022-06-21 11:00:29.411 +0300 debug: sysd_queue_sched(sysd_queue.c:672): QUEUE: sysd queue schedule: no connection yet, ignore
2022-06-21 11:00:29.412 +0300 Sysd Event: SUCCESS
2022-06-21 11:00:29.412 +0300 connected to sysd
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2022 06:06 AM
Resolved the issue by fixing the connectivity to https://data.threatvault.paloaltonetworks.com:443/search_by_id by allowing the same in security policy.
The issue was due to curl error: 35 when i clicked on the spyware profile, the firewall was trying to fetch the threat signature in background which was present in botnet exceptions, but due to connection error , it was getting timeout after particular period of time, there was a service route present for paloalto network services therefore i added *.paloaltonetworks.com in the security olicy and allowed it. and it worked fine.
It is not cool to throw an error that device is not responding.
- 1 accepted solution
- 4641 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Pan OS upgrade dependency on Dynamic Updates ERRORS in Panorama Discussions
- Custom created Anti-Spyware profiles not opening, showing “The server is not responding. Please wait and try your operation again later”. in General Topics
- GlobalProtect VPN - Multiple ISPs - Single Client IP Space Desired in General Topics
- XDR Prevent 7.2.0 Performance Issue on Win10 x64 v1903? in Cortex XDR Discussions
- Prisma Access - Cannot read property 'msg' of undefined in Prisma Access Discussions