- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Enable FTP and FTPS for Active/Passive?
- LIVEcommunity
- Discussions
- General Topics
- Enable FTP and FTPS for Active/Passive?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Enable FTP and FTPS for Active/Passive?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-22-2018 03:00 PM - edited 06-25-2018 08:37 AM
Hello Folks,
We have a CrushFTP server installed on a server behind our PA 3020 PANOS: 7.1.14, SSL decrypt not enabled.
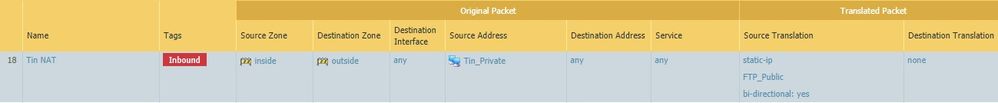
Security Rule:
NAT Rule:
Trying to figure out why Active and Passive with FTP over TLS (SSL) will not retrieve the directory listing and will not complete connection. Works fine with just FTP (insecure).
Do I need to add SSL to the security rule?
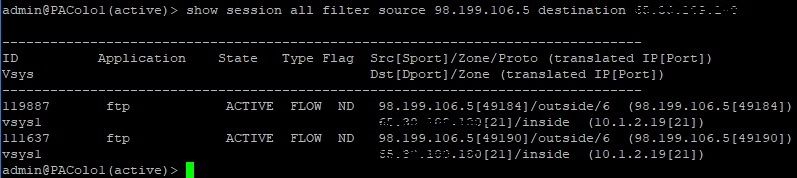
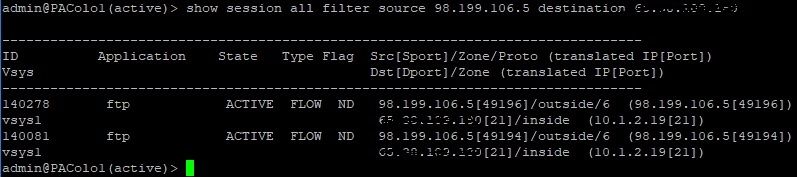
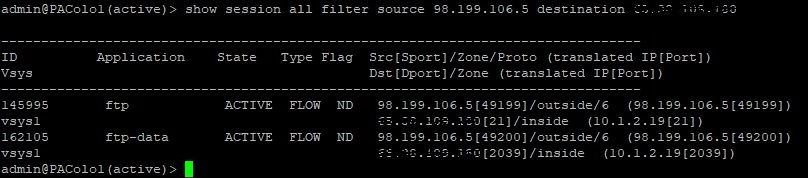
Filezilla client set to Active - FTP Only (Insecure) - Why do I not see the data transfer port 20 when I upload a file?
Filezilla Client set to Active - FTP over TLS
Filezilla client set to Passive - FTP Only (Insecure)
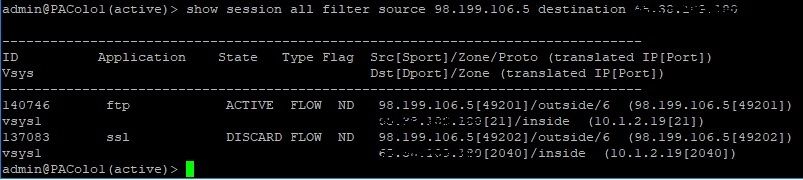
Filezilla client set to Passive - FTP over TLS (SSL) - Does this mean that FTPS is detected as SSL and discarded because not added to the security rule?
For reference:
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2018 04:42 AM
No response so far. I will close this thread by the end of the week.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2018 08:39 AM
You need SSL included in the policy if you are using FTPS and you aren't going to be decrypting the traffic. I suspect that the reason that you really haven't gotten any response is nobody here is using CrushFTP and therefore can't tell you which applications will actually be identified.
It really sounds like what you need to do is actually see what the firewall is identifying the traffic and allow what it can see. Most of the traffic will likely actually identify as 'ssl' and be spread across whatever ports your FTPS server is actually using. You can see this easily if you temporarily build out an 'allow all' policy with one specific allowed testing IP and actually perfrom an upload and a download while logging the transactions.
Just as an FYI the current Security Policy that you have specified really isn't that great since it has to allow a small amount of data to determine the application across all ports. I would verify which applications are actually coming across and then specify that application [ x y z ] can use services [ service-https whateverelse ] as you now have a much smaller threat vector.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2018 02:58 PM
Thank you for the feedback!
Good advice about allow all and see the applications used in the traffic.
After that could narrow the rule to ftp and ssl (and or if other).
Will update.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2020 11:11 PM
Creating the application override for the FTPS works for me.
Thanks!!!
- 18542 Views
- 5 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!