- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IPSec VPN with overlapping networks
- LIVEcommunity
- Discussions
- General Topics
- Re: IPSec VPN with overlapping networks
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2018 06:51 AM - edited 11-02-2018 10:49 AM
To begin with I know the document Configuring IPSec VPN between overlapping networks.
Due to my lack of experience still I am not able to understand how I should create the NAT rules.
My objective is to configure the IPSec tunnel only on "my" side - one that will be accessed and should allow access to some servers in the 192.168.2.0/24 network.
Below I put some aqnonymised configuration info:
IKE Gateway
Parameter | Value |
Version | IKEv1 only mode |
Address type | IPv4 |
Local IP Address | a.b.c.99 |
Peer IP Address | x.y.z.255 |
Exchange mode | auto |
IPSec Tunnel Proxy IDs
Parameter | Value |
Local | 10.0.2.0/24 (NAT 1:1 – original subnet 192.168.2.0/24 ) |
Remote |
The overlapping network addresses are 192.168.2.0/24
I have to create a NAT rule to show them to the accessing partner as 10.0.2.0/24 network.
I would be grateful if someone could tell me how to create this NAT rule with static translation.
Thank You a LOT! 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-12-2018 05:17 PM - edited 11-12-2018 05:18 PM
Pkt Decap and Bytes Decap have values, the restof columns are zeros.
I have not overridden the default rules.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-12-2018 07:09 PM
Is vpn tunnel interface in dedicated vpn zone? If yes do you have security policy to allow traffic from vpn zone to internal zone?
If you have not overridden default policies at the end then no log will appear to Monitor > Traffic if this traffic does not match to any existing security policy.
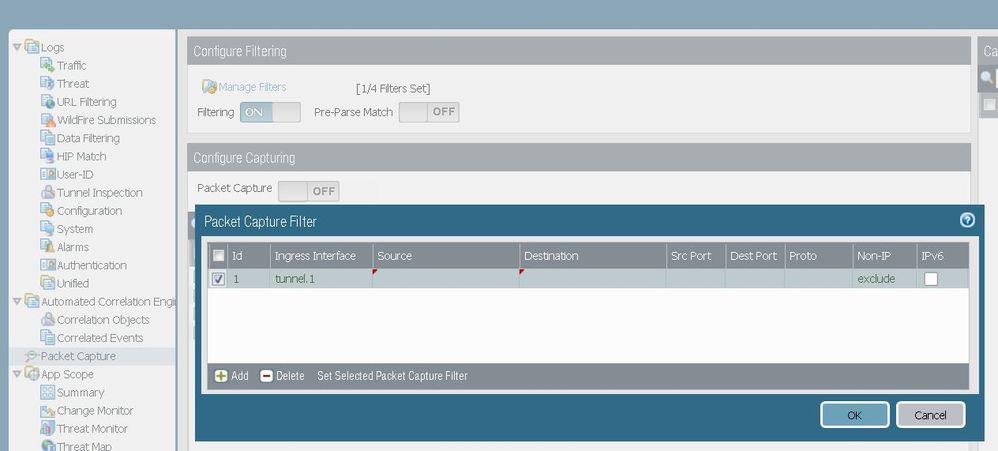
I suggest to enable packet capture filter and choose ingress interface tunnel interface that you have configured for that vpn.
And then check global counters with command below. Run it few times. What is output? Any drops?
> show counter global filter delta yes packet-filter yes
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-13-2018 06:25 AM
I would definitelly first check logs (and make sure you log everything).
If you can't find packet in logs then i would say PA isn't doing proxy ARP for static NAT rules.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2018 03:37 AM
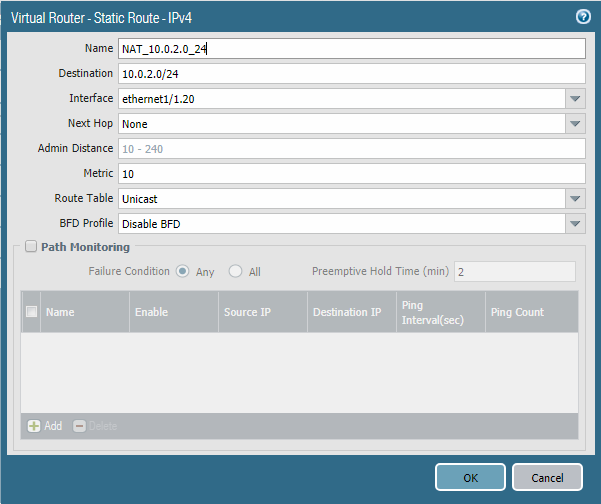
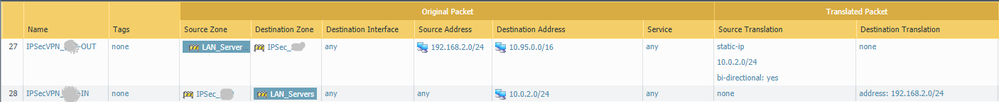
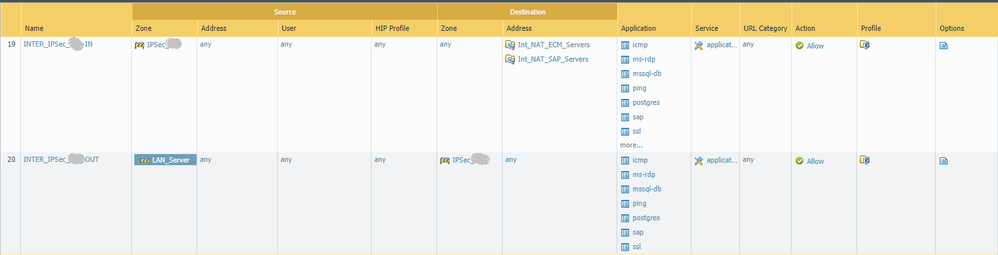
Below is the configuration that finally worked.
Static Route
NAT
Security rules
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2018 11:12 PM
Did you try only static route and only adding inbound NAT rule seperately? I'm curious what really was the original cause of issues.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-21-2018 01:55 AM
I think the main problem was the lack of the static route.
The firewall was directing the traffic to 10.0.2.0 to the Internet as it was part of 0.0.0.0 route.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-12-2020 09:03 PM
Thank you for this!! I was just about to open a ticket when I came across this post.
I have the exact situation, tried every possible NAT permutation possible and packets would still drop coming into the source-NAT'ed tunnel -- which do NOT show up in any log except the debug packet captures (and I have enabled logging on both inter and intra zone defaults).
The fix is creating that fake route back to the LAN interface in the static routes, worked immediately after adding that entry in. Really would be nice if Palo Alto's shotty 10-year old documentation on this subject (https://live.paloaltonetworks.com/docs/DOC-1594) actually worked or hinted that you need to create a dummy route back internally somewhere.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-16-2020 11:39 AM
Hey,
I have treid to do the same but seems the NAT rule and the security rule is not working.
Also can you please let me know that in the second NAT rule what is the translated packet? destination address translation with static IP or dynamic?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2021 11:35 PM
Hello,
What addresses do we use in the security rules? The translated once or original?
Thanks
- 28199 Views
- 23 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- Request for Documentation on VPN and Routing Log Events in General Topics
- Dynamic IP at Spoke site in PAN-OS SD-WAN Hub/Spoke topology in Next-Generation Firewall Discussions
- On-Boarding of Cisco SDWAN to Prisma in Prisma Access Discussions
- Situation with PA-5250s and Global Protect connections in GlobalProtect Discussions