- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Not able to normalize UPN name retrieved from SAML assertion
- LIVEcommunity
- Discussions
- General Topics
- Not able to normalize UPN name retrieved from SAML assertion
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Not able to normalize UPN name retrieved from SAML assertion
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2019 11:09 AM
Hi Team,
We have configured SAML SSO authentication for Global protect. Microsoft Azure has the active directory we have configured it as identity provider and service provider as Palo alto global protect. Trust established between Idp and SP and we are able to authenticate portal using microsoft azure.
But the problem in allowing list in authentication profile and user/user group in Global protect gateway, When azure signs the SAML assertion from Palo alto it authenticates and sends the SAML response as UPN name from the username attribute in azure.
Palo alto retived this UPN name and allowing the global protect portal and gateway configuraion only if we set the allowlist to any and user/user group to any. If we specify the username in UPN format or domain name format it is not able to validate the username and throws an error while connecting to gateway as "Matching client config not found".
palo alto says you cannot configure the firewall to modify the domain/username string that a user enters during SAML logins, the login username must exactly match an Allow List entry.
But when I configure this UPN name as a match in allowlist or user/user group it is not matching and working. Group mapping also not working in this case as server profile will normalize only for AD.
Is there a way to normalize UPN name to domain format or any other way to restrict the allowlist in authentication profile and user/user group in gateway.
Please let me know if you need more information.
Regards
Venky
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-10-2019 12:00 PM - edited 12-10-2019 02:05 PM
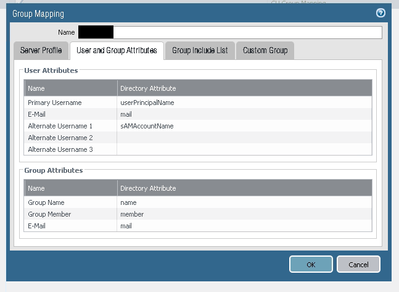
I ran into this issue as well and had to open a case with TAC. Turns out that you just have to specify the userPrincipalName as the primary username attribute within the Group Mapping profile. I also choose to specify the sAMAccountName as the alternate username attribute. Once this was configured, I could use AD groups in the GW client config.
Support for multiple username formats was added in 8.1:
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-11-2019 09:24 PM
Thanks for letting us know.
Will test this in our environment.
Help the community: Like helpful comments and mark solutions.
- 11181 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!