- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Packet capture hitting specific security policies?
- LIVEcommunity
- Discussions
- General Topics
- Packet capture hitting specific security policies?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Packet capture hitting specific security policies?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2021 05:45 AM
I would really like the capability to setup packet captures for traffic that hits specific security rules. For example, we have rules that block outbound connections to Palo's dynamic IP list for known malicious IP addresses and would like packet captures taken when traffic hits that rule. I've not seen that capability and haven't seen a forum post related to it for several years. Anyone know if this is currently supported?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2021 10:45 AM
At this time packet captures are still pretty much source-destination-port type of deal
You could reach out to your local sales guys to submit a feature request, that way it may eventually get added (post the FR number here so we can all reach out to our sales guys and vote for this feature to be added 😉 )
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2021 12:29 PM
Hello,
What type of information are you looking to get out of the pcap that already isnt in the logs?
Just curious at the use case to better assist.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2021 07:37 PM
The answer is a bit open ended. It depends on the rule being hit or the traffic we want to monitor. For example, traffic going outbound hitting the known malicious IP list could be any service or application including NTP, DNS, HTTP, etc. Packet captures would give us more details including potential payload info, URIs, hostnames in queries, etc. Don't always see that in the firewall logs.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2021 09:45 AM
Hello,
That was my assumption but wanted to be sure. Within the Security Profiles, you can set them to perform a pcap. This is however not a full blown pcapc, but something that the PAN san in brevity and already knows about. However if you want full pcaps, a 3rd party solution would be the best answer.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2021 10:12 PM
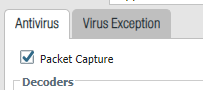
Yes, we're aware of the PCAP options on the threat prevention profiles, but those won't fire on the block rules that we're interested in, unfortunately.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2021 02:49 AM
The only idea I have is to first test a filter to see that it matches a policy that drops traffic with the test security policy feature https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/test-policy-rule-traffic-matches.ht...
After that you can use the same filter for pcap captures on the drop stage (captures only packets dropped by the firewall)
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClTJCA0
You can also use global counters and flow basic with the same pcap filter if you need see something more:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CloNCAS
https://palo-alto.fandom.com/wiki/Flow_Basic
You need to play but Palo Alto has better options than most firewalls in my opnion. There is even option to capture traffic for a specific application or service/deamon:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClS8CAK
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2021 04:11 AM - edited 03-26-2021 04:12 AM
I forgot to add that if you want to monitor which source IP tried to connect to which bad destination on a specific rule, then just make a custom report. You can then even schedule the report and recieve an email. Just add log at session end under the security rule and use the below example but also add the source and destination and maybe how many times the rule was hit (this maybe is not needed in the report as it is seen under the security policy itself https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-new-features/management-features/rule-usage-trac...).
Example custom report:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClcgCAC
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2021 07:44 AM
Hello,
3rd Party solutions would be used to just capture everything then you can search for the traffic that was blocked. I know SecurityOnion does this fairly well, however you needs taps/span ports and a lot of storage to capture the traffic.
Just a thought.
- 7228 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Best practices for Palo Alto security policy when destination IP/FQDN is dynamic or unknown in Next-Generation Firewall Discussions
- Inquiry regarding Tenant Backu & Recovery in Cortex XDR Discussions
- PAC Retention and URL Category Priority Behavior in Prisma Access in Strata Cloud Manager
- PAN-OS 12.1, IPv6 and Region/GeoIP in General Topics
- Regarding ADNSR Licensing and Region Support in Advanced DNS Security Discussions