- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
User id connected but users name not showing in the security policy
- LIVEcommunity
- Discussions
- General Topics
- Re: User id connected but users name not showing in the security policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
User id connected but users name not showing in the security policy
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2021 12:35 AM
Dear Team,
I have integrated AD to my PA NGFW. User id is showing connected but when I create any user based policy there is no users.
I have tried cleared user is cache, refresh etc. But still same.
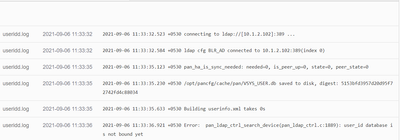
Please find the below SS for reference
useridd.log
2021-09-06 11:33:32
2021-09-06 11:33:32.523 +0530 connecting to ldap://[10.1.2.102]:389 ...
useridd.log
2021-09-06 11:33:32
2021-09-06 11:33:32.584 +0530 ldap cfg BLR_AD connected to 10.1.2.102:389(index 0)
useridd.log
2021-09-06 11:33:35
2021-09-06 11:33:35.123 +0530 pan_ha_is_sync_needed: needed=0, is_peer_up=0, state=0, peer_state=0
useridd.log
2021-09-06 11:33:35
2021-09-06 11:33:35.230 +0530 /opt/pancfg/cache/pan/VSYS_USER.db saved to disk, digest: 5153bfd3957d20d95f72742fd4c88034
useridd.log
2021-09-06 11:33:35
2021-09-06 11:33:35.633 +0530 Building userinfo.xml takes 0s
useridd.log
2021-09-06 11:33:36
2021-09-06 11:33:36.921 +0530 Error: pan_ldap_ctrl_search_device(pan_ldap_ctrl.c:1889): user_id database is not bound yet
Please help me to resolve this issue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2021 01:15 AM
Thank you for posting message @VishnuPS
If I understand it correctly, you are not able to select source user while creating a new policy? Have you configured Group Mapping Setting? Here is a reference: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClFQCA0 If yes, could you navigate to: Device > User Authentication > Group Mapping Settings > (Name) > Group Include List > Available Group, then type AD Group or User and try to search it by pressing Apply Filter button. If LDAP integration works well, the AD Group or User will appear in the list. All the AD Groups / Users that are available here, should be also selectable in new policy under source user.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2021 02:52 AM
Hi Pavel,
We verified the configurations it's good only.
I forgot you telling one thing, actually, I configured the user-id configuration from the panorama. I need to enable anything in the panorama.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2021 06:05 AM
Thank you for reply @VishnuPS
I see. When it comes to Panorama and pushing user information, there is one difference compared to configuring it locally on Firewall. The format of AD information has to be in Distinguished Name (DN). Here is the KB for reference (Please go to point No.5): https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClIOCA0
After you configure it in this format, and push it to managed Firewall, the user information should be available in security policy.
Alternative solution would be to enable one Firewall that already has all information as a Master Device in the Device Group. Here is a KB for reference: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PMtpCAG
I have tested both of the solutions and both were functional.
Thank you and Regards
Pavel
- 7547 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- unable to view traffic in moniter in General Topics
- Questions Regarding Output Difference in "show ctd-agent status security-client" Command in General Topics
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- About the output of the "show ctd-agent status security-client" command in Next-Generation Firewall Discussions