- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
vulnerability block action
- LIVEcommunity
- Discussions
- General Topics
- vulnerability block action
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2014 06:29 AM
Hi,
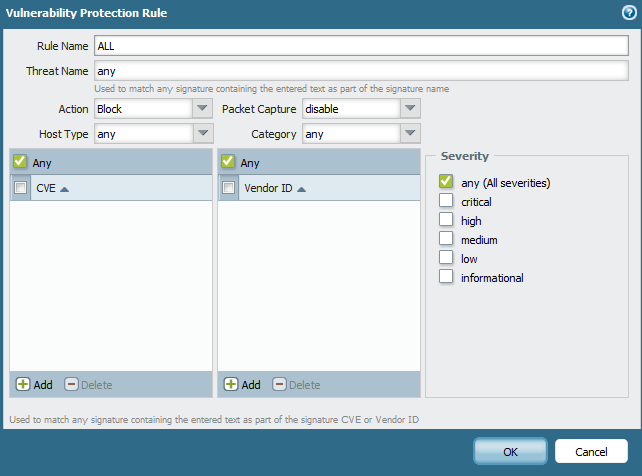
when creating a profile choosing block action is seen as "reset-both" on the logs.
is that normal behaviour or not ? Thanks.
- Labels:
-
Content-ID
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2014 08:08 AM
PA should probably update the help file for these vulnerability options. The wording is ambiguous and I assume that block was a drop and not a reset action.
Choose the action (Alert, Allow, Default, or Block) to take when the rule is triggered. The Default action is based on the pre-defined action that is part of each signature provided by Palo Alto Networks. To view the default action for a signature, navigate to Objects > Security Profiles > Vulnerability Protection and click Add or select an existing profile. Click the Exceptions tab and then click Show all signatures. A list of all signatures will displayed and you will see an Action column.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2014 07:55 AM
Hello Panlst,
This is an expected behavior. In this case, the PAN firewall blocked that Vulnerability and send TCP RST packet to both parties ( Server and client) to close the connection.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2014 08:08 AM
PA should probably update the help file for these vulnerability options. The wording is ambiguous and I assume that block was a drop and not a reset action.
Choose the action (Alert, Allow, Default, or Block) to take when the rule is triggered. The Default action is based on the pre-defined action that is part of each signature provided by Palo Alto Networks. To view the default action for a signature, navigate to Objects > Security Profiles > Vulnerability Protection and click Add or select an existing profile. Click the Exceptions tab and then click Show all signatures. A list of all signatures will displayed and you will see an Action column.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2014 08:08 AM
Hello Panlst,
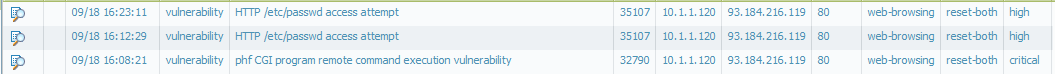
As per the screenshots attached in this discussion thread, the firewall identifies the vulnerability with threat ID: 35107

If you check the default action of this Vulnerability signature, is to reset the connection.
Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2014 08:21 AM
But PanLst is choosing "Block" not "Default" for the action.
The help file does not specify which action occurs with "Block" drop or reset. Are you saying above that the action is reset both?
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2014 12:25 AM
but we choose block not default.There is something wrong here.Block = reset both
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2014 08:08 AM
Hello Panlst,
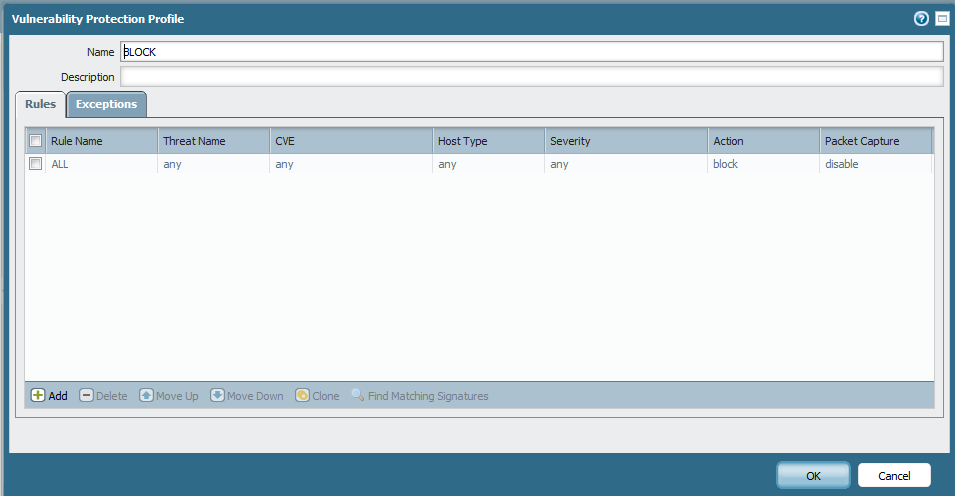
My apologies, i understand it wrongly. You are correct, As per the DOC: Vulnerability Profile Actions if traffic is hitting this vulnerability-protection rule, it should simply drop all packets for that session.
Could you please provide a snapshot of the traffic logs and security rule, just to confirm the vulnerability rule "ALL" applied to the correct policy.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2014 01:58 PM
Hi HULK;
I replicated that.
Here are the screens.I think there is something wrong with definitions or explanations.
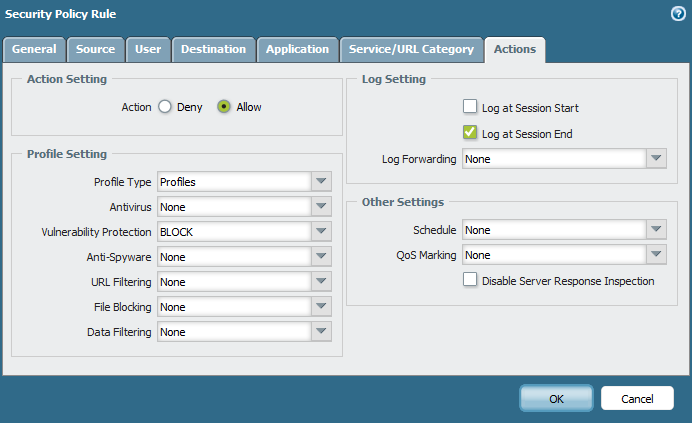

- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2014 02:21 PM
The default action is defined by Palo Alto Networks on a per-threat basis as either alert or block.
Every vulnerability has a "block" behavior. Some block behaviors send a reset to the server or client, or in this case, both. For this example the default action is block, and the block behavior is reset-both. Even though the action being taken is block, the threat log will show the block behavior that was used to terminate the session under the action column.
Quick edit:
If you want to change the "block" behavior for a threat, you must configure an exception.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2014 02:25 PM
Thanks for answer.
So block behaviour should be added somewhere on the guides as definiton also I think.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-31-2022 01:20 AM
It's hard form me make Definition to any of this Threat ID, Like XMRig Miner Command and Control Traffic Detection(85886) or MVPower DVR Shell Unauthenticated Command Execution Vulnerability(57566).
Do you have any guide or E-Book for make any definition of Threat ID.
- 1 accepted solution
- 9929 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Request for Query to Retrieve Endpoint Security Details. in Cortex XDR Discussions
- How to Patch Vulnerability - Plugin 43160 (CGI Generic SQL Injection) on GlobalProtect in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Security Posture Settings are now moved to Incident Settings in Strata Cloud Manager
- Anti virus profile not able to scan a file? in Next-Generation Firewall Discussions



