- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Third party SSL cert for Global Protect
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Third party SSL cert for Global Protect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Third party SSL cert for Global Protect
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2022 10:19 AM
I have a third party (Network Soluitions SSL cert that expires in 2023 but validation not past July 22nd of 2022. What is the process from start to finish with the cert and on the firewall? I'm assuming I need to have NS reissue another cert with another request and then follow this article but just wanted to confirm these are the steps? https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-admin/certificate-management/obtain-certificates...
Thank You
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2022 05:24 PM
Depending on how you issue your certificates for GlobalProtect (there are 3 sources, but only 2 are discussed here), if the old certificate is expiring you will need generate a signing request and have an external authority (i.e. Network Solutions) or your internal CA sign it. The document you listed is the general procedure, but 7.1 is a very old version of PANOS. Is that what you are actually running on your device? You can check the running version from the Dashboard tab ("Software Version" line) or from Device tab -> Software. On the listed page you can go to instructions for other versions by selecting/changing the drop-down box "CURRENT VERSION: 7.1 (EoL)".
General steps are:
1) Generate a new certificate. Give it a unique Certificate Name, I would suggest something like "GlobalProtect_2022" to differentiate it from the previous/future versions of the same use. Set the Common Name to be your GP FQDN. Set "Signed by:" to be "External Authority". Important part - under Certificate Attribute be sure to set a "Host Name" value to be the same as your GP FQDN and any other FQDNs you will be connecting as (this will appear in a Subject Alternative Name tag in the final certificate, which is what browsers/etc. use now instead of Common Name). Your certificate provider may restrict what names you can use. Also fill out the Country, State, Locality, and Organization values as your cert provider will probably require those as well. Generate the certificate and then select/export it. You will get a CSR (Certificate Signing Request), to send to your CA.
2) After you CA has generated your certificate, import the file from the same page. Important - from the import page use the exact same "Certificate Name" you created above. This will match the certificate to the CSR you generated before and convert the CSR into a private/public certificate pair that can be used on the VPN Portal/Gateway.
3) When you are ready to switch to the new certificate, go to your Portal and Gateway configurations and determine which SSL/TLS Service Profile they are currently using:
Network -> GlobalProtect -> Portals -> [config] -> Authentication -> SSL/TLS Service Profile
Network -> GlobalProtect -> Gateways -> [config] -> Authentication -> SSL/TLS Service Profile
Depending on how you have the Portal/Gateway setup, these may be the same or separate profiles. Update the profile to use the new certificate. After commiting it may take a few minutes for the VPN/web services to restart using the new certificate.
Device -> Certificate Management -> SSL/TLS Service Profiles -> [config] -> Certificate:
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2022 05:15 AM
one more question, when I do the renewal with N.S., do I choose IIS from
the list for the web hosting server software or something else?
Jamie
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2022 09:26 AM
I am not familiar with the list of NS options. I would select Apache/Unix or general HTTP if those are options. You will want to download the new certificate in Base64-encoded PEM format, not DER-encoded.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2022 07:08 AM
Okay, I tried to bring up the list again to post here but wasn't able to. I chose IIS most recent versions so hopefully it will work but it was in the correct format. I'll let you know how it goes once the cert is issued to me. Thank you again for all your help!
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2022 07:18 AM
You'll know if it is valid or not when you upload to the firewall. You should get green checks if the cert is validated on the firewall. From there you can deploy it in the global protect client.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2022 07:30 AM
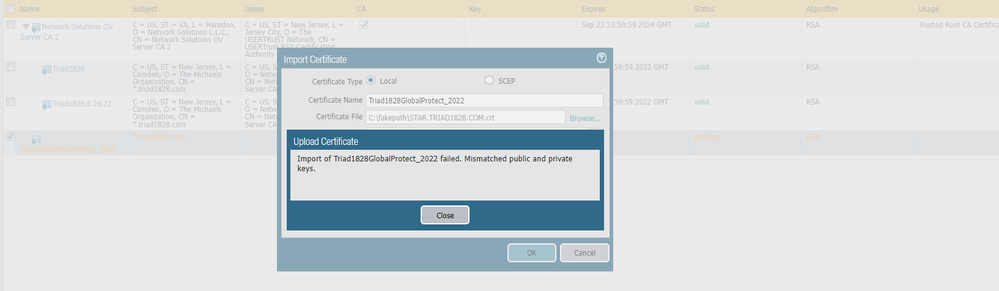
I received the reissued cert but am running into an error which I screen shot below. I used the same name so not sure why?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2022 07:39 AM
It's telling you that that keys do not match. What cert types do you have the option of downloading from your CA? Try to get a cert that contains all of the cert files including the key. You may have to do some evaluation of the cert with OPENSSL to determine why the key is a mismatch. Your CA could potentially help with that as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2022 08:59 AM
As @danoman2 says, the private key you generated in step #1 does not match the public key you received back from the CA in step #2. I am not exactly sure why that happened and you would probably have to investigate the certs to determine why they mismatched. Some causes could be (but not limited to):
- You exported the wrong cert to sign and/or switched certs between multiple firewall you were signing.
- Your CA change the cert values during signing causing a problem (they shouldn't do this, they should reject the request if something is wrong).
- Your CA issued a renewal against your previous certificate instead of generating a new certificate (try importing against the old?)
- ???
You may need to inquire with the CA as to why you are getting the error.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2022 11:36 AM
Turns out that when I downloaded the cert, it was the old (expiring this month) one from Network Solutions. For some reason the download link was not updated for the newest cert. Followed your instructions and all is working with the new certificate! Thank You for all your assistance. I'm guessing I can either delete or revoke the old certificates?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2022 12:02 PM
That would do it...
Once you have changed the SSL/TLS Certificate Profile to use the new certificate, you can delete the old certificates. It may take several minutes for the profile changes to take effect and your web management interface/etc may be temporarily unreachable while the web services restart. Once it has changed over you can delete the old certificate. If the old certificate is used somewhere else in the config the PA won't let you delete it until it has been fully remove.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2022 12:17 PM - edited 06-29-2022 12:17 PM
Jaime,
Here is a good resource for all things global protect related. Resource List: GlobalProtect Configuring and Troubleshooting - Knowledge Base - Palo Alto Networks
This is the guide I would follow for your use case. Found it in the cert section of the above link. I hope this helps. How to Generate a CSR (Certificate Signing Request) & Import th... - Knowledge Base - Palo Alto Netw...
- 8662 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Can you configure clientless VPN in SCM ? in GlobalProtect Discussions
- global protect connection failed authentication failed !!! in GlobalProtect Discussions
- PAC Retention and URL Category Priority Behavior in Prisma Access in Strata Cloud Manager
- AWS vpc Global Protect terraform deployment in VM-Series in the Public Cloud
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions