- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IP blocked then allowed
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- IP blocked then allowed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
IP blocked then allowed
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-18-2024 07:45 PM
Hi,
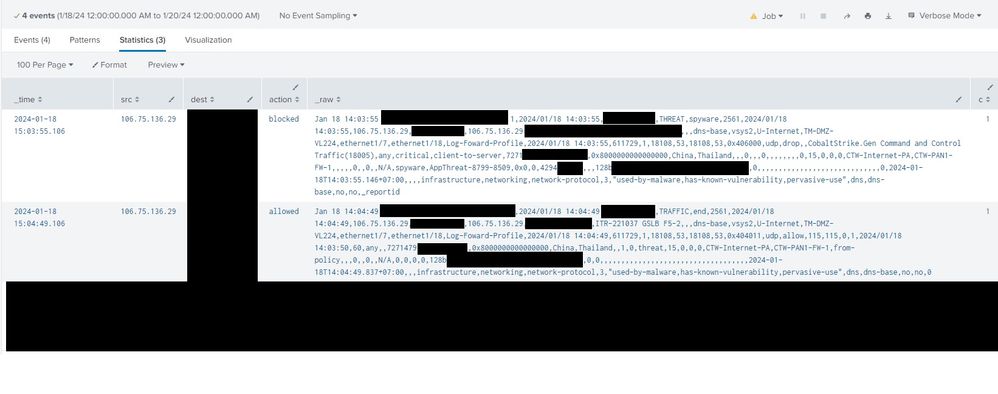
I'm reviewing a logs regarding a low reputation IP which in the first log it's action is dropped, and 5 minutes later 3 logs with action allowed. Why does it dropped then allowed it?
Logs
category: spyware
action: dropped
Threat Name: CobaltStrike.Gen Command and Control Traffic
Threat ID: 18005
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-22-2024 01:19 PM
Hello,
Not sure if its the case here however logs are typically written at 'session end'. We would need to see redacted logs to try and figure this out. Just black out the source and destination IP's along with anything that could identify your company etc.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2024 12:35 AM
Hi, please find the ss below
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2024 07:43 AM
Hello,
So the 'later' traffic is UDP (DNS-Base) so it has to 'time out' since there is no fin packets. This is the most likely reason for the later timestamp in the logs. The policy is most likely set to log at session end, which is best practice.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2024 10:42 PM
does UDP has fin packets?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2024 10:45 PM
i did a bit of research from your explanation, using the first link below to understand the session end. then using data from Session End reason: threat, i found out the answer in the second link. thanks for your help
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/monitoring/use-syslog-for-monitoring/sysl...
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u000000HCQlCAO
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-29-2024 09:41 AM
Hello,
Glad you found what you needed.
Cheers!
- 2409 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Disconnect Internally but not remotely in GlobalProtect Discussions
- Geo blocking after GP login in GlobalProtect Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Migration problem from PA220 to PA540 - Virtual Router in Next-Generation Firewall Discussions
- Device Certificate Enforcement Issue Encountered in Next-Generation Firewall Discussions