- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Block on APP-ID (Apache Log4j )
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Block on APP-ID (Apache Log4j )
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Block on APP-ID (Apache Log4j )
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-13-2021 04:37 AM
Hello All,
After a bit of help ...I' have never created a block type rule on a Palo and now my boss wants me to create a .block rule for the above.
We have about 300 policies in the our firewall so no idea how to create a block and apply it .
Can anybody give me any pointers ?
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-14-2021 07:14 PM
You need to do it by applying vulnerability security profile to each policy, or edit the security profiles you already applied to the security rules.
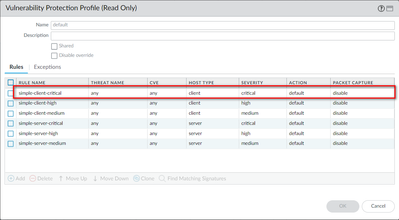
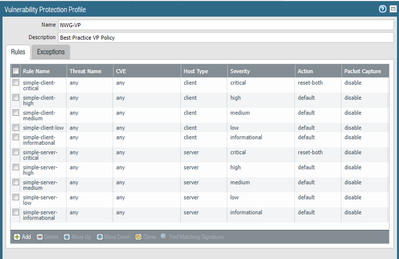
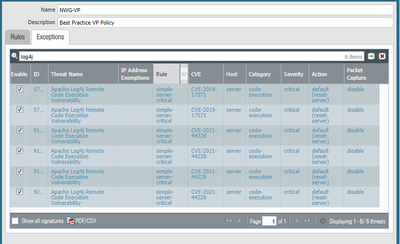
But, the default action of log4j vulnerability signatures are "reset-server" and severity are critical:
You just need to make sure the rule in each security profile is included severity critical and action is default or other suitable type, as below screenshot of the default profile:
just provide me thought for you as a reference.
Regards,
Sample
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-15-2021 03:32 AM
Hi - Thanks for that - I have created what I hope is correct.
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2022 01:46 AM
@Scott64 wrote:Hello All,
After a bit of help ...I' have never created a block type rule on a Palo and now my boss wants me to create a .block rule for the above.
We have about 300 policies in the our firewall so no idea how to create a block and apply it .
Can anybody give me any pointers ?
Regards
Upgrade to Log4j 2.3.2 (for Java 6), 2.12.4 (for Java 7), or 2.17.1 (for Java 8 and later).
In prior releases confirm that if the JDBC Appender is being used it is not configured to use any protocol other than Java.
Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
Also note that Apache Log4j is the only Logging Services subproject affected by this vulnerability. Other projects like Log4net and Log4cxx are not impacted by this.
- 4768 Views
- 3 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!