
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
The content you are looking for has been archived. View related content below.
Log forwarding has been part of firewalls since, well, the beginning of firewalls. The sheer amount of logging can be intimidating and some challenges can occur. For example, how can I forward a particular set of logs to start troubleshooting across a variety of teams? Do you have time to filter through your flood of unwanted logs manually to filter out what you need exactly? No one has time for all that.
Using PAN-OS log filtering features you can:
Log forwarding profiles are designed to accommodate log filtering. Users can create match lists in the log forwarding profile.
All the forwarding actions mentioned in the match list will be taken against that particular traffic log. A traffic log can match more than one match list, forwarding actions mentioned in all the matching lists will be taken. New match criteria can be added to the forwarding profile with “Add” option. In the example below, two match lists are configured:
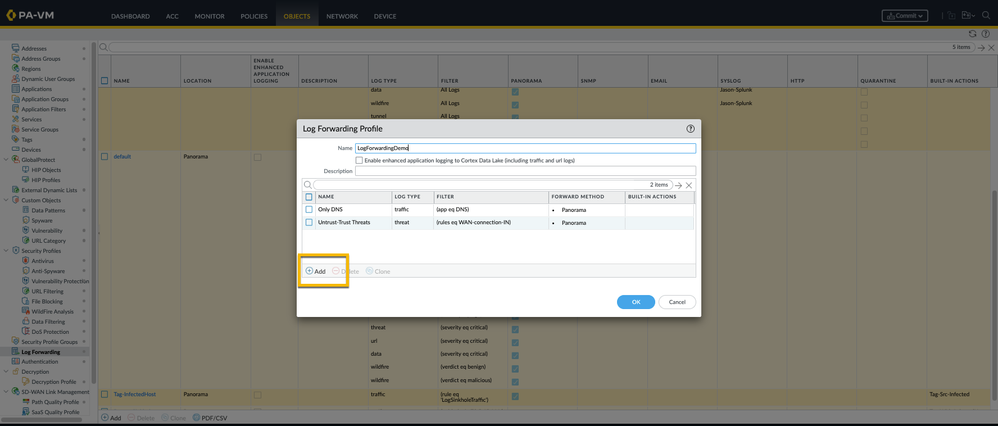
Log Forwarding Profile Match List allows for the creation of custom filters as shown here:
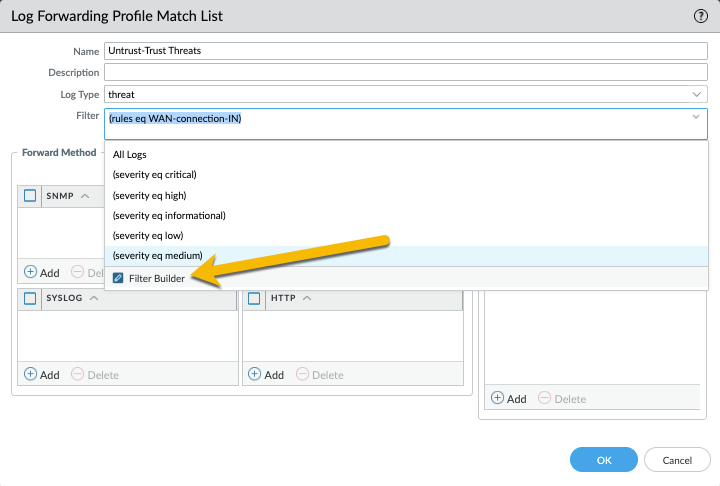
By default, the firewall forwards ALL logs of the selected Log Type. To forward a subset of the logs, select an existing filter from the drop-down or select 'Filter Builder' to add a new filter to select interesting logs to be forwarded. These filters are similar to the filters that you can use on the monitor tab:
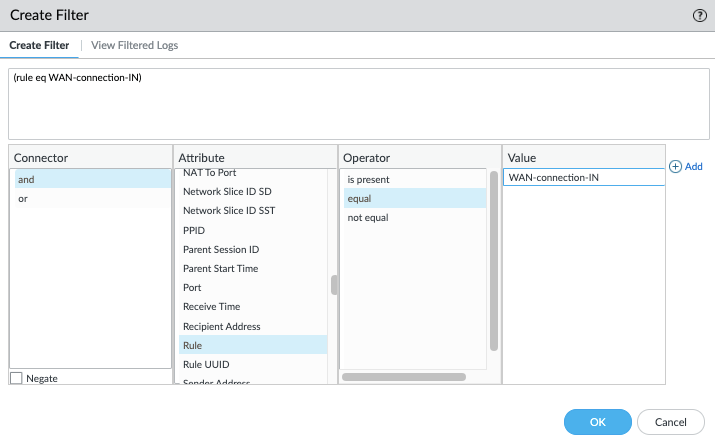
You can check the ‘View Filtered Logs’ tab to verify which logs exactly will be forwarded.
It can be challenging to create your own filter, but you can work backwards and have the firewall create a filter for you. Without a configured filter you can go to the 'View Filtered Logs' view and you will have an unfiltered view. From here you can make any selection from the displayed logs and the firewall will create a filter for you in response to that. Notice how the firewall creates a filter for me when I make any selection in the 'View Filtered Logs' tab.
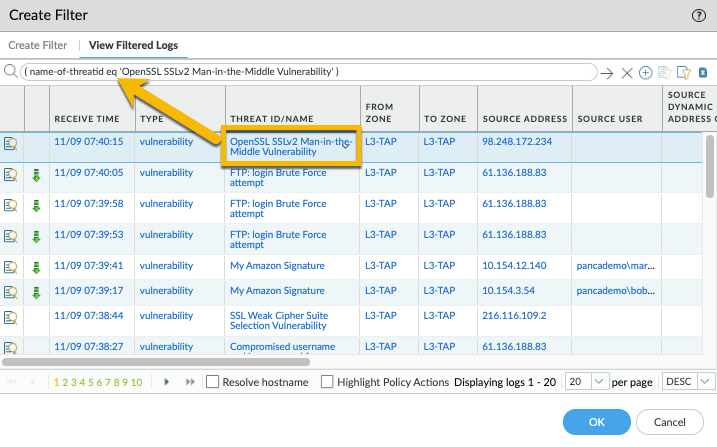
Click the 'Apply Filter' button to see exactly which logs exactly will be forwarded:
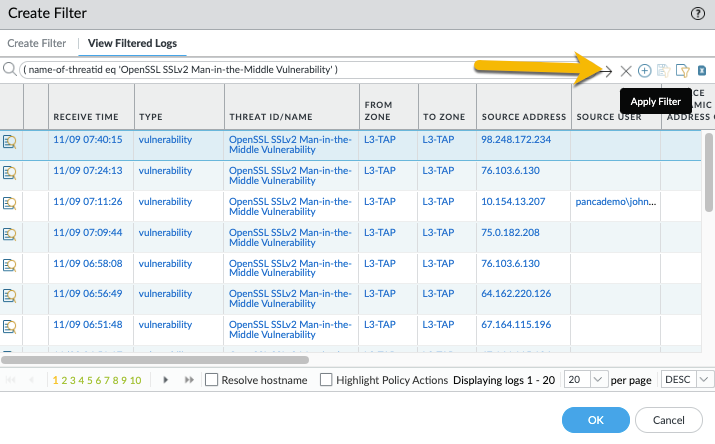
Click OK and all that remains to be done is select your Forward method (Panorama in this example) and name it (MITM Vulnerability), for example. Once you do that you can click the OK button and you can confirm if the Log Forwarding Profile looks fine and you can click the OK button once more.
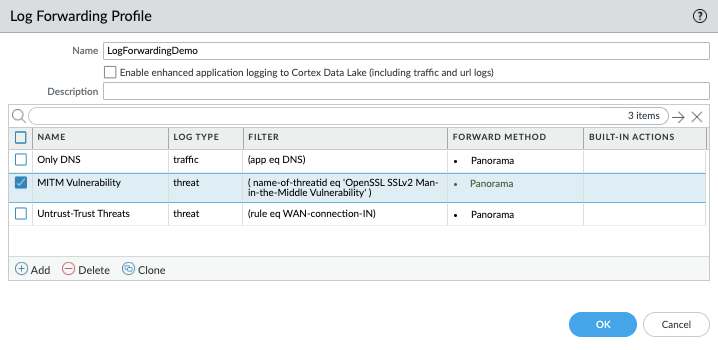
With this your log forwarding profile is created.
Similarly, you have the log settings feature on the device tab. You can configure system logs, config logs, UserID, GlobalProtect and HIP match logs. The same granularity was added in all of these logs:
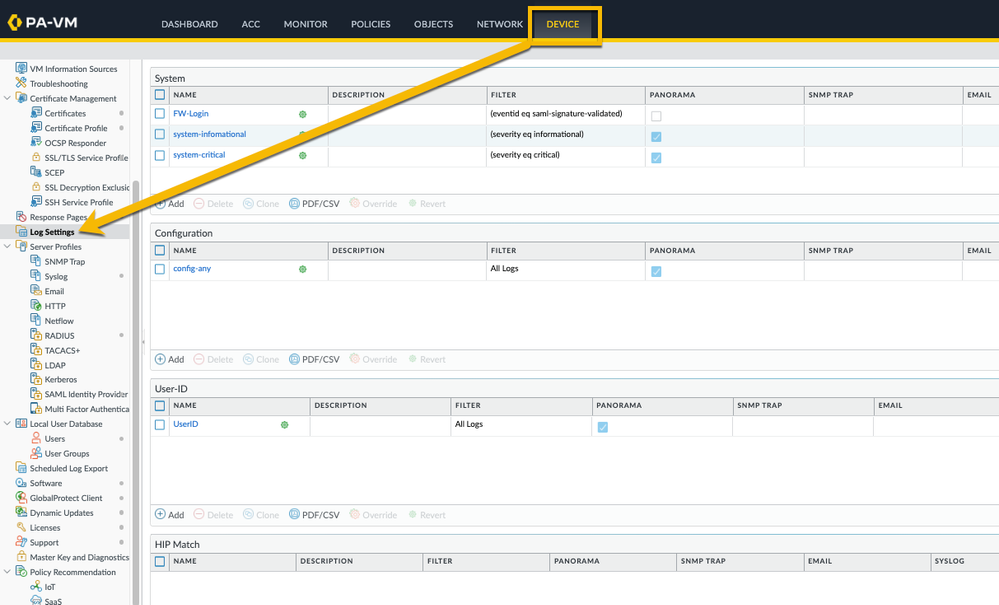
As an example check out the 'Log Settings - Configuration' below, where I configured a forwarding option for the filter (admin eq kiwi):
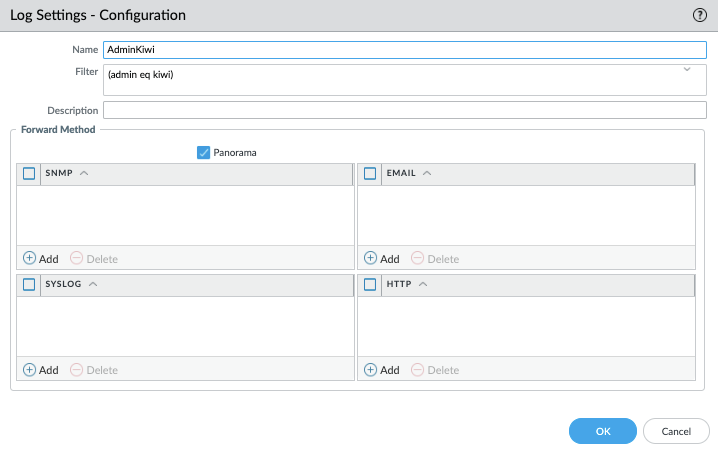
Notice in the example above that I've set my forwarding option to Panorama. If you are happy with this you can go ahead and click OK and commit the change.
With this new feature, a flood of unwanted logs will soon be a thing of the past!
How have you implemented filtered log forwarding?
Feel free to share your questions, comments and ideas in the section below.
Thank you for taking time to read this blog.
Don't forget to hit the Like (thumbs up) button and to Subscribe to the LIVEcommunity Blog area.
Kiwi out!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 5 Likes | |
| 4 Likes | |
| 3 Likes | |
| 2 Likes | |
| 2 Likes |
| User | Likes Count |
|---|---|
| 12 | |
| 5 | |
| 4 | |
| 2 | |
| 2 |




