- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
NAT and site to site VPN
- LIVEcommunity
- Discussions
- General Topics
- Re: NAT and site to site VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
NAT and site to site VPN
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 08:47 AM - edited 11-27-2015 08:48 AM
Hello,
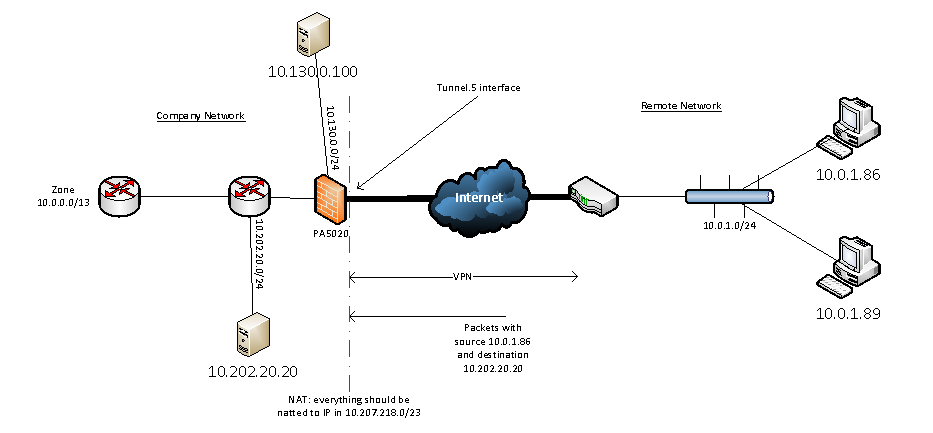
We're trying to build a Site to Site VPN connection with an other company. They are installing software on two of our servers (10.130.0.100 and 10.202.20.20) and they need the VPN to automatically transfer configuration and other files.
The VPN-link is active but we have a problem with overlapping subnets. They use subnet 10.0.1.0/24, but we also use that subnet in our network.
I have little experience implementing NAT. Is it possible to use a NAT-rule on our PA5020 that translates the 10.0.1.0/24-subnet adresses from the other company into a 10.207.218.0/23 IP? I already created a route in the PA to route traffic to 10.207.218.0/23 into the tunnel.5 interface. Can someone explain me in detail the NAT-rule (and other policies, routes) I have to create?
Thanks,
Stefan
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 09:42 AM
You will both have to choose a subnet to NAT the other company network to and apply a NAT rule on your tunnel traffic.
This document outlines the procedures for the process.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 12:29 PM - edited 11-27-2015 12:30 PM
Thank you for your reply. Very interesting document.
There is no way to solve this on the company firewall only? Subnet 10.0.0.0/13 is a subnet of a remote router in our network, it's not a subnet of the firewall itself.
As a test I tried to make NAT rules for client 10.0.1.86 with server 10.202.20.20 on our company firewall:
Source NAT rule for the incoming traffic to our company:
source zone = vpn; dest zone = trust; source ip = 10.0.1.86, dest ip = 10.202.20.20; source translation = static ip / 10.207.218.5 / not bi-directional
and a destination nat for the outbound traffic
source zone = trust; dest zone = vpn; source ip = 10.202.20.20; dest ip = 10.207.218.5; dest interface = tunnel.5 / dest translation = 10.0.1.86
When I run a Packet Capture on interface tunnel.5, I only see (icmp) packets coming from 10.0.1.86, but I don't see anything in the policy log.
Can someone explain this to me?
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-28-2015 12:52 AM - edited 11-28-2015 12:54 AM
You have to configure on both firewall. Configuring only on one firewall is not possible.
Lets say that you have 10.0.1.0/24 on both sides A,B
Now you have to represent 10.0.1.0/24 of side A as 10.0.11.0/24 and represent 10.0.1.0/024 of side B as 10.0.22.0/24
lets say this a host on side A 10.0.1.1 and he is trying to ping a host on side B 10.0.1.2.
Host on side A will do a ping to 10.0.22.2, on firewall A you have to do a source NAT such that when the traffic reaches to firewall B it should appear that it is coming from 10.0.11.1 and a destination NAT on side B such that traffic for 10.0.22.2 should be translated to 10.0.1.2
lets say this a host on side B 10.0.1.22 and he is trying to ping a host on side A 10.0.1.11
Host on side B will do a ping to 10.0.11.11, on firewall B you have to do a source NAT such that when the traffic reaches to firewall A it should appear that it is coming from 10.0.22.22 and a destination NAT on side A such that traffic for 10.0.11.11 should be translated to 10.0.1.11
Keypoint is you have to do two NAT rule on each firewall. One will be source NAT for the traffic coming from behind of your firewall and Destination NAT for traffic coming from other side.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-30-2015 01:30 AM
Thank you for your clear answer.
Stefan
- 7324 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Tunnel Monitoring in Next-Generation Firewall Discussions
- Issue with allowing AnyDesk on a no-internet policy in Next-Generation Firewall Discussions
- Performance impact of using higher DH group for site-to-site VPNs in Next-Generation Firewall Discussions
- Adding PA DR site globalprotect SSL-VPN gateway in GlobalProtect Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions