- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Rule syntax/ordering question
- LIVEcommunity
- Discussions
- General Topics
- Rule syntax/ordering question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Rule syntax/ordering question
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2012 03:58 PM
We've just installed a PA-2050 in our school and I'm trying to get it configured with some basic rules but I'm not quite sure I have the syntax or ordering of my rules right to achieve the outcome I want.
The simple side of things that I want to do is allow access to Facebook to members of the Active Directory group Staff Users while denying access to everyone else.
Here are the two rules that are causing me issues

A complicating factor here is that a large number of my students who I'm trying to block here are using their own devices on the wireless and as yet I am unable to identify their AD username which is why I have an "any" in the user field of the deny rule.
Any suggestions as to how I can structure my rules to get this outcome.
The next step will be allowing Facebook and Tumblr to those same blocked users on a schedule but for now, I'm happy with just blocking them outright.
- Labels:
-
Configuration
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2012 04:54 PM
To allow facebook and tumblr, you need to allow web browsing and ssl if you have not already done so. The rule set you have should allow facebook and tumblr access to the staff users.
If you want to have control over the users who are not identified by AD, I would suggest using Captive Portal which will provide an authentication page before they can access any resources.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2012 06:19 PM
Here's my full rule set
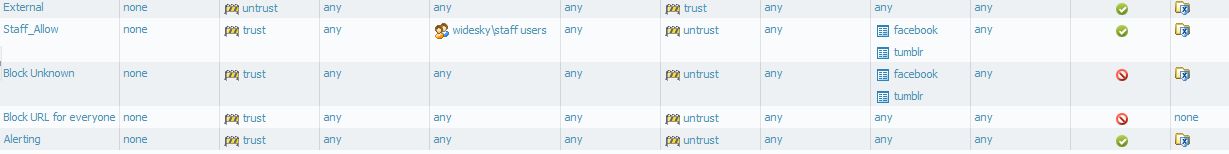
Even when I explicitly put my user name in the Staff_Allow rule, the rule below it continues to override it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2012 12:27 AM
PA uses top-down first-match (like most FW's do nowadays) which gives that your "Alerting" rule will never be hit since its shadowed by "Block URL for everyone".
Could you paste the output you get from the commit-window when you commits?
There should be warnings about the shadowing I mentioned above aswell as lack of dependencies (which what I guess is why your user never hits that allow rule).
To test if your userid is correct you could as a test (if possible) set application to "any" to verify that its application related and not userid related.
By the way - your service-column should NEVER be set to any (in my opinion) - you should use "application-default" OR set this manually (like TCP80, TCP443 if you only want browsing to occur on these ports).
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-04-2012 08:31 AM
Do you see any activity on that rule in the Traffic Logs on the Monitor page?
Try this from the command line…
test security-policy-match application facebook-base source-user 'staff username here' source x.x.x.x destination y.y.y.y destination-port XX protocol 6
From: rangiruru <live@paloaltonetworks.com<mailto:live@paloaltonetworks.com>>
Reply-To: live <live@paloaltonetworks.com<mailto:live@paloaltonetworks.com>>
To: Brad Spilde <brad.spilde@daktronics.com<mailto:brad.spilde@daktronics.com>>
Subject: Rule syntax/ordering question
We've just installed a PA-2050 in our school and I'm trying to get it configured with some basic rules but I'm not quite sure I have the syntax or ordering of my rules right to achieve the outcome I want.
The simple side of things that I want to do is allow access to Facebook to members of the Active Directory group Staff Users while denying access to everyone else.
Here are the two rules that are causing me issues
Image:pa rules.jpg (https://live.paloaltonetworks.com/servlet/JiveServlet/showImage/3027/pa+rules.jpg)
A complicating factor here is that a large number of my students who I'm trying to block here are using their own devices on the wireless and as yet I am unable to identify their AD username which is why I have an "any" in the user field of the deny rule.
Any suggestions as to how I can structure my rules to get this outcome.
The next step will be allowing Facebook and Tumblr to those same blocked users on a schedule but for now, I'm happy with just blocking them outright.
- 4240 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!



