- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect: Pre-Logon Authentication
- LIVEcommunity
- Products
- Network Security
- GlobalProtect
- GlobalProtect Articles
- GlobalProtect: Pre-Logon Authentication
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 04-10-2020 12:08 PM - edited on 10-03-2022 09:51 AM by jforsythe

In my previous article, "GlobalProtect: Authentication Policy with MFA," we covered Authentication Policy with MFA to provide elevated access for both HTTP and non-HTTP traffic to specific sensitive resources. You can see a diagram of the environment here.
In this post, we are going to add pre-logon authentication using machine certificates.
The value of pre-logon authentication means that a device can be connected to a gateway before an actual user logs into the machine, allowing certain internal resources to be accessible or scripts to be run. For more information about pre-logon, please review this TechDocs article: Remote Access VPN with Pre-Logon.
- You have already followed the previous articles in this series.
Part V - Pre-logon Authentication
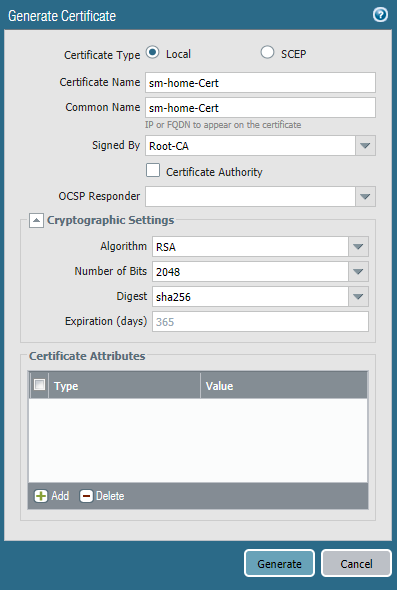
- Navigate to Device > Certificate Management > Certificates > Generate to create a machine certificate signed by the root CA that was previously created
- Enter a Certificate Name that represents the device
- Enter a Common Name that represents the device
- Select the root CA that was previously created for Signed By
- Click Generate
- NOTE: It is recommended to use an enterprise CA in a production environment
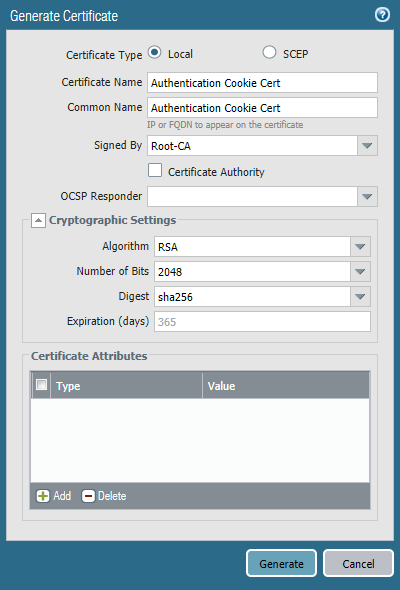
- Navigate to Device > Certificate Management > Certificates > Generate to create an authentication cookie certificate signed by the root CA that was previously created
- Enter a Certificate Name that represents the device
- Enter a Common Name that represents the device
- Select the root CA that was previously created for Signed By
- Click Generate
- Navigate to Device > Certificate Management > Certificates > select the newly created machine certificate > Export Certificate
- Set the File Format to Encrypted Private Key and Certificate PKCS12 and enter a Passphrase twice
- Install the certificate on your test machine
- For the steps with Windows machines, read the following article:
- For the steps with OS X machines, please read the following articles:
- For the steps with iOS machines, please read the following article:
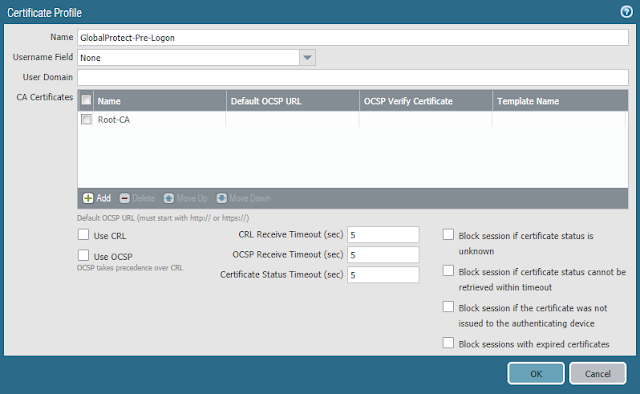
- Navigate to Device > Certificate Management > Certificate Profile > Add to create a new Certificate Profile
- Enter a Name
- Navigate to CA Certificates > Add to add the root CA that was created previously
- Click OK
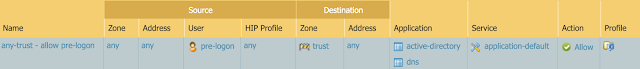
- Navigate to Policies > Security > Add to create a rule above your existing rules which allows access from devices assigned the Pre-logon user to the minimum internal resources necessary
- Navigate to Network > GlobalProtect > Portals > select the existing portal that was previously created
- Navigate to Agent > Add
- Enter a Name
- Enable Authentication Override and select the certificate to be used for authentication cookies that was created previously
- NOTE: Pre-logon will only work if:
- Authentication Override is enabled and the Certificate Profile created previously is applied under the Portals > (your portal) > Authentication tab
- Authentication Override is enabled and the Certificate Profile created previously is not applied under the Portals > (your portal) > Authentication tab
- Authentication Override is not enabled and the Certificate Profile created previously is applied under the Portals > (your portal) > Authentication tab
- In this use case, we are using option two, but it's important to note that it will fail if the user has not been previously connected. As we have an internal gateway configured, this will allow the user to connect, or refresh the connection, while on the internal network to generate the Pre-logon cookie.
(See "GlobalProtect Pre-Logon Using Cookie-Based Authentication" for more information.)
- Navigate to Agent > Add

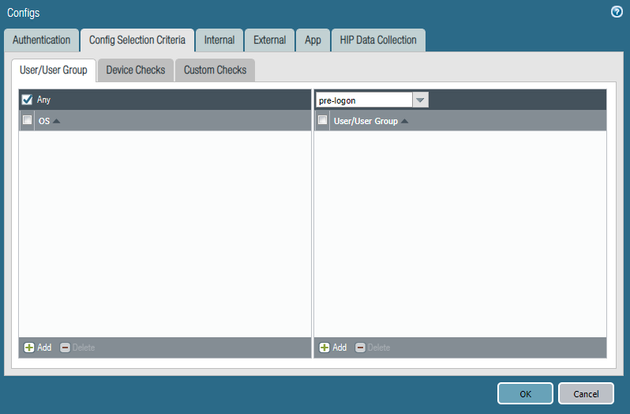
- Navigate to Config Selection Criteria and set User/User Group to pre-logon
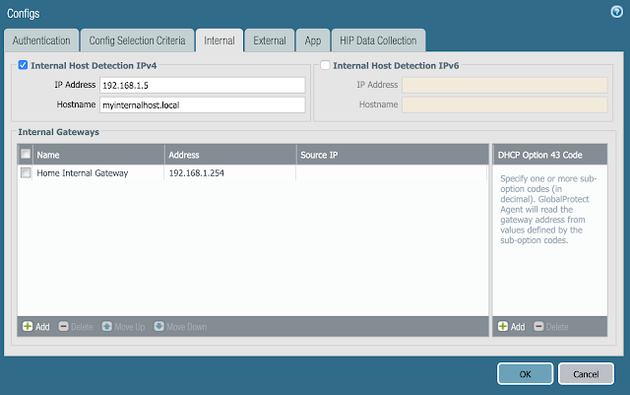
- Navigate to Internal and enter the same information that exists in your other agent configuration
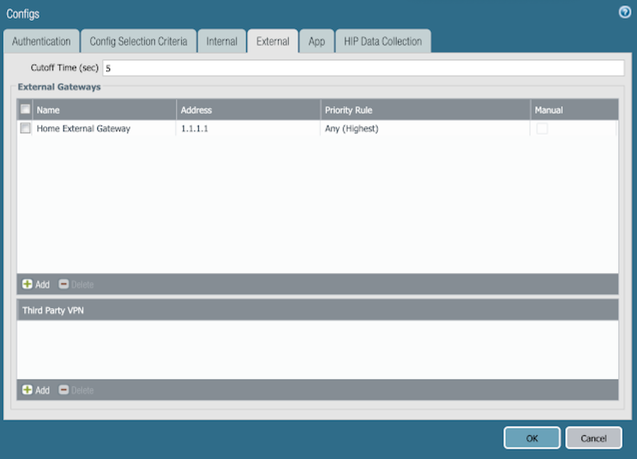
- Navigate to External and enter the same information that exists in your other agent configuration
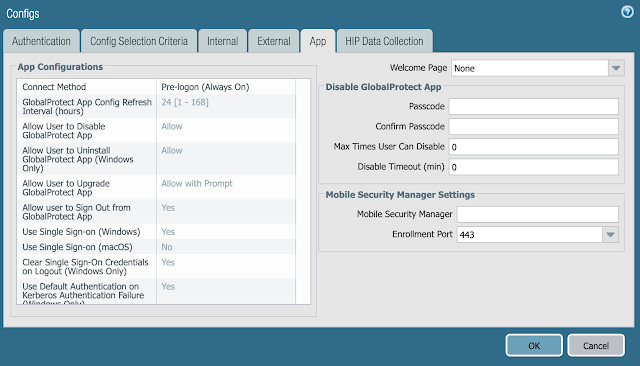
- Navigate to App and set the Connect Method to Pre-logon (Always On)
- Click OK
- Navigate to Network > GlobalProtect > Portals > select the existing portal that was previously created
- Navigate to Agent and select the other Agent that was created prior to beginning the configuration changes in this article (NOT the portal machine config you created above)
- Enable Authentication Override and select the certificate to be used for authentication cookies that was created previously
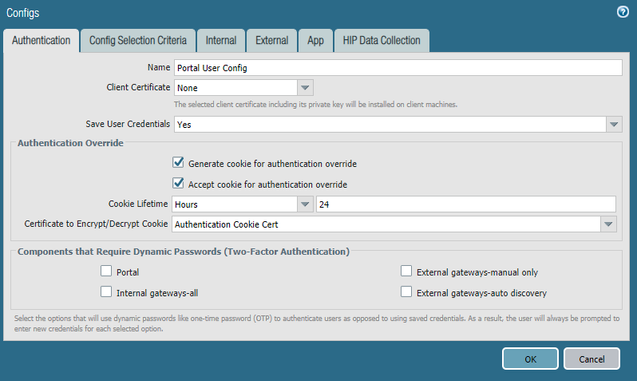
- Navigate to App and set the Connect Method to Pre-logon (Always On)
- Click OK

- Navigate to Network > GlobalProtect > Gateways > select the external gateway that was previously created
- Navigate to Authentication > Certificate Profile and the certificate profile that was previously created
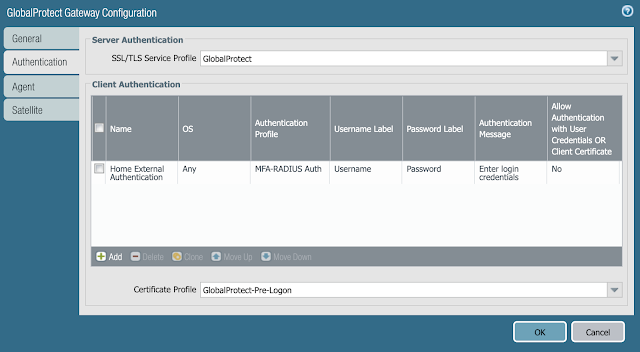
- Navigate to Agent > Client Settings > select the existing config > Authentication Override then enable it and select the certificate to be used for authentication cookies that was created previously
- Click OK
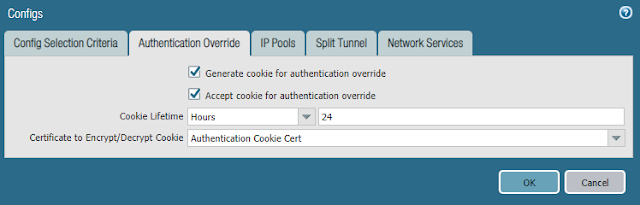
- Click OK
- Commit the configuration
Hopefully you see this and can offer some advice. We have pre-logon set up and was working in testing. As it relates to the gateway, we have the following client configs:
Pre-logon
Students
Staff
Each has their own IP Pools. When you boot you successfully authenticate to the gateway in the pool for pre-logon. When you log on we are seeing the user stay in that pool but show the proper username. If you do a "refresh connection" you land in the proper ip pool based on user. Have you seen this?
Hi Brian,
I haven't seen this behavior before. That stated, it seems logical that this would occur because the tunnel and its corresponding IP address won't refresh when the user changes from Pre-logon to the actual user's account. What is the reasoning behind the multiple client configs and pools?
-Spencer
Thanks for your reply. The engineer that installed our palos originally set it up that way (different ip pools for different users groups - students vs staff vs it staff) prior to me implementing pre-logon. In an on-demand world it worked fine. It makes sense to me to have different pools. Are you saying that you don't think it will ever switch during a logon? I don't think the user changes until they're fully logged in (desktop visible) so it could happen then and not have any impact. Perhaps something is wrong, because our clients do actually disconnect from GP as they are logging on. I see the client go through "Connecting" again.
Hi Brian,
It wouldn't hurt to open a case just to validate the behavior. I would think that if it doesn't go through a full refresh of the connection then it would retain the existing IP.
In the past with traditional VPN concentrators I have seen the use of different IP pools as a mechanism to segment user traffic at the network layer. Many times this was because there was lack of security capabilities beyond basic ACLs to control user access after authentication on the concentrator, and segmenting traffic at layer 3 would allow security admins to control the traffic in different ways as it traversed the rest of the security stack (i.e. firewall, IPS, content filter, etc.) to access internal resources and the Internet. My recommendation would be to explore the Source User and HIP aspects of security policy. As every user must authenticate to use GlobalProtect for access, you will have a user mapping as well as host information that you can leverage to determine identity/posture and subsequently enforce policy based on that context. In other words, leveraging a policy construct based on those elements makes it unnecessary to split users up into different pools. I would just have a single pool because there is no loss in visibility or granularity of control. Not sure if that is helpful or not, but I just thought I would share what I've seen and recommended while in the field :).
-Spencer
Thanks for taking the time to reply. I know you were waiting with anticipation on the answer... I heard back from support - sounds like I just needed to change the pre-logon tunnel rename timeout from -1 to 0.
Pre-Logon Tunnel Rename Timeout (sec) (Windows Only)
This setting controls how GlobalProtect handles the pre-logon tunnel that connects an endpoint to the gateway.
A value of -1 means the pre-logon tunnel does not time out after a user logs on to the endpoint; GlobalProtect renames the tunnel to reassign it to the user. However, the tunnel persists even if the renaming fails or if the user does not log in to the GlobalProtect gateway.
A value of 0 means when the user logs on to the endpoint, GlobalProtect immediately terminates the pre-logon tunnel instead of renaming it. In this case, GlobalProtect initiates a new tunnel for the user instead of allowing the user to connect over the pre-logon tunnel. Typically, this setting is most useful when you set the Connect Method to Pre-logon then On-demand, which forces the user to manually initiate the connection after the initial logon.
I would like to share my experience with GlobalProtect which forced me to use different IP pools instead of relying on user identification. We use Active Directory authentication via RADIUS profile for our users. If a user connects via GlobalProtect and then logs via Remote Desktop on a machine in internal network, connected user losses it's association to the IP address received from VPN pool, and is associated with the IP address of remote machine on which he/she logged. All the user can do is work via established RDP session until it disconnects. When RDP session disconnects, VPN connection must be reset, as no other session can be made from the client's IP (because rules are user-based, and Palo Alto Firewall no longer associates IP address of GP client with that user, so request are not recognized as coming from that user). Because of this we made several IP pools and we make rules based on IP addresses instead of users. I feel that this is wrong, but can't find a way around the user identification problem.
@brianjreed thanks for finding that setting.
I have 2 gateways... pre-logon users all go to gateway A. Post-login, default users stay on gateway A but a certain user group needs to connect to gateway B. The trouble is that the user group was staying on A instead of switching to B. So hopefully this timeout will fix my issue.
- 61561 Views
- 8 comments
- 2 Likes
- Seamless Single Sign-On with Palo Alto Networks GlobalProtect in GlobalProtect Articles
- Seamless Login With GlobalProtect (Client Certificate Authentication) in GlobalProtect Articles
- GlobalProtect App Log Collection and Troubleshooting FAQ in GlobalProtect Articles
- Troubleshooting GlobalProtect MTU Issues in GlobalProtect Articles
-
DHCP
1 -
ESXi
1 -
Global Protect
1 -
GlobalProtect
19 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect-COVID19
12 -
GlobalProtect-Resources
9 -
Layer 3
1 -
NGFW Configuration
11 -
Prisma Access
1 -
PrismaAccess-COVID19
1 -
VM-Series
1
- Previous
- Next




