- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Adding an External Dynamic List Object and importing the Intermediate CA certificate from the external web server that the EDL is hosted on
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Re: Adding an External Dynamic List Object and importing the Intermediate CA certificate from the external web server that the EDL is hosted on
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Adding an External Dynamic List Object and importing the Intermediate CA certificate from the external web server that the EDL is hosted on
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2023 02:55 PM - edited 02-15-2023 02:57 PM
I am trying to add an External Dynamic List to our PA-440.
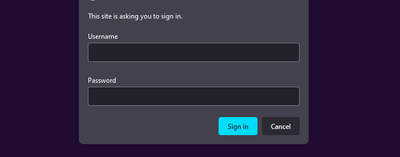
The External Dynamic List is hosted on an external web server by one of our security partners. This web server is https enabled and authentication is via username/password. This is the screenshot when you go to the EDL's Source URL:
According to this documentation, in order for the firewall to authenticate to this server, I will need to add the Intermediate CA certificates that match the certificates installed on the server the firewall is authenticating. With that profile, I will have the option to add a username and password to the External Dynamic List object when I add the correct Certificate Profile.
Here is the documentation that states I need to add the Intermediate CA certificates that match the certificates installed on the server the firewall is authenticating:
My understanding of this is I needed to:
- Download the Intermediate CA certificate from the external web server that's hosting the EDLs
- Import this Intermediate CA certificate into the Certificate Manager
- Create a Certificate Profile to add to the EDL object.
Downloading the Intermediate CA Certificate:
To download the Intermediate CA certificate from the external webserver that's hosting the EDLs.
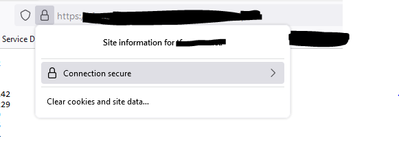
- Click the lock icon:
- Click on "Connection Secure":
- Click on "More Information":
- Click "View Certificate":
- Click the middle certificate (the Intermediate CA), scroll down and download the cert file (.PEM)
> Is this the correct file to be downloading?
> The UserTrust CA is already in the list of Trusted Certificate Authorities in the Certificate manager of the PA-440, so this Intermediate CA Certificate is all I should need.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2023 07:14 PM
Hi @user9891 ,
Yes, that process is correct. The document actually says to add the root and intermediate to the certificate profile. That is the process that I use, and it works. Your reasoning makes sense that the root is already trusted. Let us know if only the intermediate CA works in the certificate profile.
Thanks,
Tom
- 2704 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- need to renewal certs for Panorama in Panorama Discussions
- CRL for Certificate-Device access denied in AIOps for NGFW Discussions
- Machine Certificate Check/ Not working for me in GlobalProtect Discussions
- IOS and Globalprotect using Multifactor authenticator in GlobalProtect Discussions
- GP fails on iOS, connects on Android, Mac and Windows... in GlobalProtect Discussions