IPs en lista Barracuda Reputation Block List (BRBL)
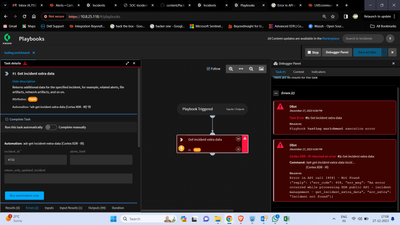
Estimados tengo implementado un playbook en Xsoar que usa varias fuentes de enriquecimiento y se ha identificado que Barracuda esta identificando como IP maliciosa, IPs de redes solciales como facebook, instagram, whatssap, etc y otras publicas de la
...