xdr-get-incident command date time dispute
Hello everyone,
I have a script that need to get incidents from server.
Hello everyone,
I have a script that need to get incidents from server.
Hi ,
Is there a way to automate the process of mapping every incident to its MITRE Technique ,
or it should be manual for every incident ?
Hi,
I have been using Panorama integration to block the IP. Is there any way where I can unblock the IP or remove the IP from address group of Panorama.
does anyone have a xql query that will return endpoint_names with and associated CVE count?
Hi everyone. I am new to this industry and I am looking for guidance on how to extract IOC from threat intel email body in Xsoar Playbook. Hoping if someone can help out. Thank you.
XSOAR server based community edition is always asking me my admin cred. It happens every 10 seconds. How can I remediate this issue ? Thanks in advance.

Hey,
I need your help.
We are receiving alerts "XDR Incident 945 - 'Large upload (generic)' generated by #XDR Analytics detected...
Basically, this appears when the user makes a call, shares documents, or shares their screen (using Microsoft Teams)
...
Hi Team,
Can you please suggest a few case studies where CrowdStrike XDR is integrated with Cortex SOAR and what were the areas and use cases that were implemented and helped the customer?
We wanted to present this to a management that already has
...
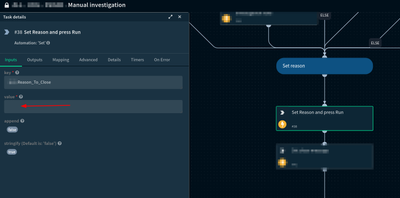
Hello community,
I have some playbooks that are responsible for closing incidents in the various sources (XDR, QRadar, XSOAR, JIRA, ...) once I enter a reason or reason for them to be closed.
I have done this using a "Set" automation that wa
...
Hi,
I am trying to take a sum of incidents over a given time, and divide this sum per month, using Beve Syntax.
I there any syntax that would give me a per-month break down? So I can take incidents per month, and display them in a widget using a b
...
Hi,
I am trying to setup remote repositories, in a first step only the dev environment.
In About -> Troubleshooting I have set "ui.version.control.show.remote" to "true" (copy-pasting it from the documentation [1] and checking multiple times for ty
...
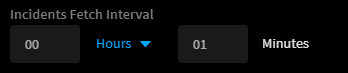
Hi ,
in my Qradar integration I don't have this parameter ,
I have enabled the "Long Running Instance" and still it takes too long for the incidents to be fetched.
Is there a way to manually configure the Incident Fetch Interval.
I'm using IBM QRad
Hi, I am trying to create a custom widget that calculate follwing (Total Incident+ Total Command Execution) with date paramters adjusted by widget. I tried to implement this with JSON method and Automation Script but unable to get the solution. Can y
...
Kind of similar to the below link:
LIVEcommunity - Cortex XSOAR Context Issue - LIVEcommunity - 437729 (paloaltonetworks.com)
I've tried mapping content from the Abnormal Security integration and from the Syslog v2 integration. The Abnormal Securit
...
I am attempting to create a Slack channel from XSOAR using the slack-create-channel command. After a few minutes, I get the following error:
"Reason

