- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
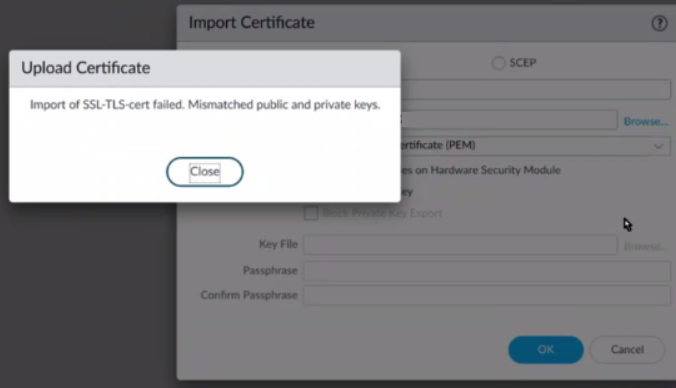
Import of SSL-TLS-cert failed. Mismatched public and private keys.
- LIVEcommunity
- Discussions
- General Topics
- Import of SSL-TLS-cert failed. Mismatched public and private keys.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2022 07:57 AM
We are adding a new Web Server certificate for portal validation in our brand new firewall.
We created the CSR in the Firewall and exported it to sign it with GoDaddy CA.
Once we download the bundle from GoDaddy we extracted the root, intermediate, and server certificate in Base64 format.
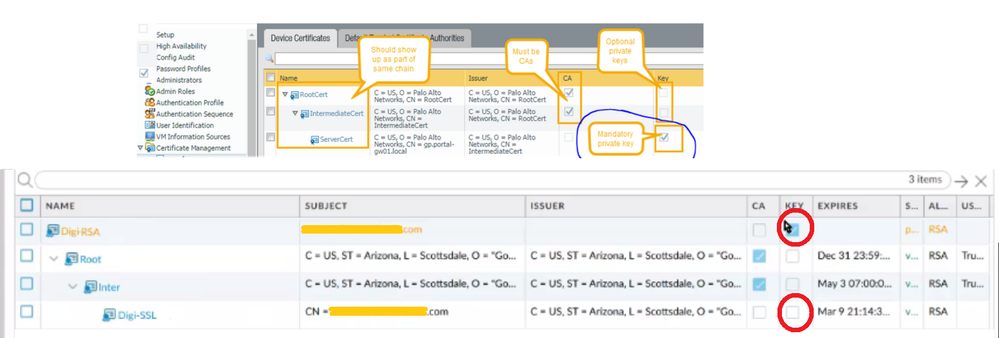
We can import the root and intermediate without any problems and we can see Root \_ Intermediate right below the Pending CSR.
However when we are trying to import the server certificate we get an error: Import of SSL-TLS-cert failed. Mismatched public and private keys.
SSL-TLS-cert is the name of the file, however we found documentation that indicates to use the name of the CSR file to import this last certificate, and in other use the name of the file that we exported initially.
This last one worked, however the "pending" CSR doesn't go away.
As you can see even when the server certificate was successfully imported to the chain, it is not taking the private key and removing the pending CSR Digi-RSA at the top that contains the private key.
Any ideas on how to properly import a third party CA to the Firewall?
Thanks in advance and have a great day.
Jorge.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2022 07:25 PM
When you generate the CSR it needs to be the name that you actually want to use for the server certificate going forward, as you will need to use that same name when you import the server certificate to "tie" the private key to the certificate in question. Your Root and Intermediate certificates it doesn't matter, you don't have a private key to associate with that so you're just doing a normal certificate import.
From your screenshot you didn't import the server certificate with the same name of the original CSR (Digi-RSA), so the firewall doesn't know to tie the private key to the imported server certificate. Re-import the server certificate with the exact same name as the original CSR. In your screenshot where you were "successful" in importing the certificate on the firewall is missing the private key because it wasn't imported with the proper name.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2022 08:39 AM
I had issues with importing certs as well. Using Firefox instead of Chrome fixed the issue for me.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2022 08:59 AM
Did you have exactly the same error about "Import of certificates failed. Mismatched public and private keys".
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2022 04:02 PM
Hi @JorgeOrtega ,
Unless you are hitting a bug, the firewall is telling you that the public and private keys do not match. Is there a chance that a different CSR was uploaded to GoDaddy than the one on your firewall? You can go to this site -> https://www.sslshopper.com/certificate-key-matcher.html to verify that the CSR on the firewall matches the cert you have imported.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2022 07:25 PM
When you generate the CSR it needs to be the name that you actually want to use for the server certificate going forward, as you will need to use that same name when you import the server certificate to "tie" the private key to the certificate in question. Your Root and Intermediate certificates it doesn't matter, you don't have a private key to associate with that so you're just doing a normal certificate import.
From your screenshot you didn't import the server certificate with the same name of the original CSR (Digi-RSA), so the firewall doesn't know to tie the private key to the imported server certificate. Re-import the server certificate with the exact same name as the original CSR. In your screenshot where you were "successful" in importing the certificate on the firewall is missing the private key because it wasn't imported with the proper name.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2022 05:46 AM
BPry you got it right. I tried in another firewall and after several testing I could import it using the same name. I couldn't find anything related about this "must match" name in the regular Palo documentation but in one from a CA.
Thank you so much.
Jorge.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2022 05:49 AM
Thanks Tom. I think this also could match a bug but the fact that I could do it on mine tells me that it might be a process error. I will follow what I did on my firewall and if that doesn't work then I will know it is a bug.
Thanks.
Jorge.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2023 09:19 AM
Importing the signed certificate with the same name as the CSR does not work. It results in a mismatched public/private key error message. Only when importing the signed certificate with the name "cert_" prefixed to the name will it work. For example, when exporting the CSR, Panorama adds "cert_" to the front of the name. So the filename is cert_MyCert.csr. When importing the signed certificate, if you use 'MyCert' it fails. If you use 'cert_MyCert' it succeeds, but the Key checkbox remains unchecked and the CSR remains in 'pending' state.
- 1 accepted solution
- 20788 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- XSOAR Dev to Prod - Builtin content repository in Cortex XSOAR Discussions
- Service Connection for Prisma Access Browser- How to ? in Prisma Access Discussions
- ION Security Stack in Advanced SD-WAN for NGFW Discussions
- What is the Best Practice to block iCloud relay? in General Topics
- Multiple Logins on internal network (macOS Platform SSO) in GlobalProtect Discussions