- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IPSEC ikev2-send-p2-delete
- LIVEcommunity
- Discussions
- General Topics
- IPSEC ikev2-send-p2-delete
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-13-2021 11:17 AM - edited 12-13-2021 11:45 AM
Hi all, I have a IKEv2 IPSEC from PA to PA Firewall with tunnel monitoring enabled on one end. The tunnel suddenly went and the peer with no tunnel monitor is sending every 4 seconds a ikev2-send-p2-delete.
What could be the reasons behind this behaviour?
Regards
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-14-2021 03:27 PM
{quote}
selector VPN-PH2_BRB-P_T1018 src is ambiguous, using the first one of the expanded addresses
{quote}
I'd look at your Peer and Local identification configuration and make sure that they actually match on both ends, or the proxy configuration if you have one.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-13-2021 07:35 PM
Have you looked at your ikemgr.log file and verified that you aren't seeing a key delete or anything like that? That would be the first place to start looking.
less mp-log ikemgr.log
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-14-2021 12:33 AM
The logs show the following:
2021-12-14 09:13:27.320 +0100 [PNTF]: { 3: }: ====> IKEv2 CHILD SA NEGOTIATION STARTED AS RESPONDER, non-rekey; gateway VPN-PH1_BRB-P <====
====> Initiated SA: 192.168.170.252[500]-213.41.102.4[500] message id:0x00000493 parent SN:2700 <====
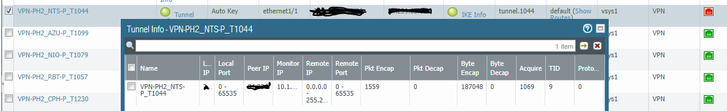
2021-12-14 09:13:27.320 +0100 [WARN]: { 3: 4}: selector VPN-PH2_BRB-P_T1018 src is ambiguous, using the first one of the expanded addresses
2021-12-14 09:13:27.320 +0100 [WARN]: { 3: 4}: selector VPN-PH2_BRB-P_T1018 dst is ambiguous, using the first one of the expanded addresses
2021-12-14 09:13:27.347 +0100 [INFO]: { 3: 4}: SADB_UPDATE proto=255 213.41.102.4[500]=>192.168.170.252[500] ESP tunl spi 0xB91C4A6D auth=NON-AUTH enc=AES256-GCM16/36 lifetime soft 378897/0 hard 432000/0
2021-12-14 09:13:27.347 +0100 [INFO]: { 3: 4}: SADB_ADD proto=255 192.168.170.252[500]=>213.41.102.4[500] ESP tunl spi 0xA3A1EB5D auth=NON-AUTH enc=AES256-GCM16/36 lifetime soft 349193/0 hard 432000/0
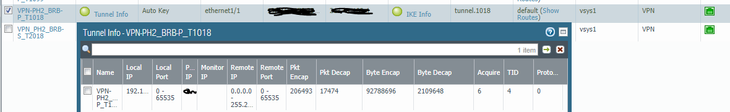
2021-12-14 09:13:27.347 +0100 [PNTF]: { 3: 4}: ====> IPSEC KEY INSTALLATION SUCCEEDED; tunnel VPN-PH2_BRB-P_T1018 <====
====> Installed SA: 192.168.170.252[500]-213.41.102.4[500] SPI:0xB91C4A6D/0xA3A1EB5D lifetime 432000 Sec lifesize unlimited <====
2021-12-14 09:13:27.348 +0100 [PNTF]: { 3: 4}: ====> IKEv2 CHILD SA NEGOTIATION SUCCEEDED AS RESPONDER, non-rekey; tunnel VPN-PH2_BRB-P_T1018 <====
====> Established SA: 192.168.170.252[500]-213.41.102.4[500] message id:0x00000493, SPI:0xB91C4A6D/0xA3A1EB5D parent SN:2700 <====
2021-12-14 09:13:27.350 +0100 [INFO]: { 3: 4}: SPI B91C4A6D inserted by IKE responder, return 0 0.
2021-12-14 09:13:27.354 +0100 [INFO]: { 3: 4}: SPI DCA1C63B removed by keymodify, return 0 0.
2021-12-14 09:13:27.355 +0100 [PNTF]: { 3: 4}: ====> IKEv2 CHILD SA DELETED AS RESPONDER, non-rekey; tunnel VPN-PH2_BRB-P_T1018 <====
====> Deleted SA: 192.168.170.252[500]-213.41.102.4[500] message id:0x00000492, SPI:0xDCA1C63B/0xA3E51416 parent SN:2700 <====
2021-12-14 09:13:27.357 +0100 [INFO]: { 3: }: ikev2_request_initiator_start: SA state ESTABLISHED type 3 caller ikev2_child_delete
2021-12-14 09:13:27.357 +0100 [INFO]: { 3: }: IKEv2 INFO transmit: gateway VPN-PH1_BRB-P, message_id: 0x000002E6, type 3 SA state ESTABLISHED
2021-12-14 09:13:27.357 +0100 [PNTF]: { 3: 4}: ====> IPSEC KEY DELETED; tunnel VPN-PH2_BRB-P_T1018 <====
====> Deleted SA: 192.168.170.252[500]-213.41.102.4[500] SPI:0xDCA1C63B/0xA3E51416 <====
2021-12-14 09:13:27.357 +0100 [INFO]: { 3: 4}: SADB_DELETE proto=255 src=213.41.102.4[0] dst=192.168.170.252[0] ESP spi=0xDCA1C63B2021-12-14 09:13:27.364 +0100 [INFO]: { 3: }: received DELETE payload, protocol ESP, num of SPI: 1 IKE SA state ESTABLISHED
2021-12-14 09:13:27.365 +0100 [INFO]: { 3: }: delete proto ESP spi 0xA3E51416
2021-12-14 09:13:27.365 +0100 [PWRN]: { 3: }: can't find sa for proto ESP spi 0xA3E51416
As i mention initially, this repeats every 4 seconds. Both phases are up on both ends of the tunnel, however on the side of the tunnel were tunnel monitor is enabled, the tunnel interface is down and there is no decaps
On the other end apart from not having tunnel monitor enabled everything appears to be fine, i see packets encap and decap
This tunnel was working fine until it started to behave wierd.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-14-2021 03:27 PM
{quote}
selector VPN-PH2_BRB-P_T1018 src is ambiguous, using the first one of the expanded addresses
{quote}
I'd look at your Peer and Local identification configuration and make sure that they actually match on both ends, or the proxy configuration if you have one.
- 1 accepted solution
- 21998 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Stealth Rule Question in Next-Generation Firewall Discussions
- S2S IPsec VPN with Multiple Domain Encryption in General Topics
- Question on PA-440 Failover in General Topics
- IPSEC VPN for the FW MGMT in Next-Generation Firewall Discussions
- Hotspot Shield VPN still works even though traffic logs show deny – Palo Alto Firewall in General Topics