- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PA UID LAB not working correctly
- LIVEcommunity
- Discussions
- General Topics
- Re: PA UID LAB not working correctly
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2021 10:34 AM
Hi Everyone,
I am currently having issues trying to get UID to work on Eve-NG using PANOS 9.0.4, it is a only a EVAL license but everything is working except for UID.
I have followed agentless guide to setup and AD server is connected to the PA as per the "User Mapping" tab.
Policy is setup correctly, however as soon as I add "Domain Users" as the Source to the policy and commit, the host loses connectivity to the internet..
- Now, if I was to leave the Users blank then the host is able to get the internet.
Currently, seeing the below error, but been unable to find any resolution.
2021-03-27 21:41:10.163 +0000 Warning: pan_user_group_user_prime_uid_lookup(pan_user_group_multi_attr.c:1279): For palo\pauser user, domain palo does not exist in group-mapping
2021-03-27 21:41:13.157 +0000 Warning: pan_user_group_user_prime_uid_lookup(pan_user_group_multi_attr.c:1279): For palo\pauser user, domain palo does not exist in group-mapping
2021-03-27 21:41:16.149 +0000 Warning: pan_user_group_user_prime_uid_lookup(pan_user_group_multi_attr.c:1279): For palo\pauser user, domain palo does not exist in group-mapping
domain palo does not exist in group-mapping - It is mapped correctly (so, i think) and I am able to pull the directory directly from AD.
======
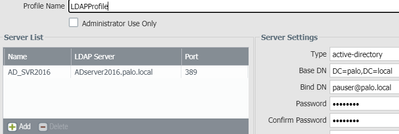
This is the Group Mapping:
Group Mapping(vsys1, type: active-directory): GroupPro
Bind DN : pauser@palo.local
Base : DC=palo, DC=local
Group Filter: (None)
User Filter: (None)
Servers : configured 1 servers
ADserver2016.palo.local(389)
Last Action Time: 1020 secs ago(took 0 secs)
Next Action Time: In 2580 secs
Number of Groups: 2
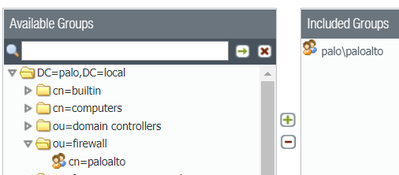
cn=paloalto,ou=firewall,dc=palo,dc=local
cn=domain users,cn=users,dc=palo,dc=local
Please let me know if you need more information.
Thank you in advance.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2021 04:49 AM
in your user identification settings, check if you have probing enabled. probing wil periodically send out a WMI probe to see if a user is still logged on, if the WMI user doesnt have enough privileges or the laptop firewall blocks the probe (or per the use case, the user is logged off or the laptop is shut down), the user will be unregistered from the user-ip mapping
also check your 'cache' as the default is 45 minutes which is too short in most cases (go for 9 hours which corresponds to the average kerberos ticket/time spent at work)
check to see if your mapped user corresponds to the group members:
show user group list
show user group name cn=paloalto,ou=firewall,dc=palo,dc=local
did you enable user-id in the dmz and trust zones (network > zones > enable user identification)
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2021 01:49 PM
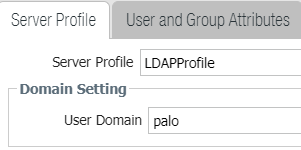
how did you set the 'domain' in the group mapping object (Device > user identification > group mapping settings)?
it needs to be the netbios domain (so 'palo' in your case), or empty. anything else will make it fail
are you seeing the user in "show user ip-user-mapping all" ?
in your security rule, are you setting "Domain Users" or is it "known-user" ? ("Domain Users" does not exist as a default value so it must be an object you created)
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2021 02:44 PM
Many thanks for replying,
Under "Group Mapping", I have set it "palo" instead of "palo.local"
Within AD, I have a OU called "Firewall"
- Within the Firewall OU > I have a Security Group called "paloalto"
- I have two test account Members within "paloalto"
- dmzuser
- trustuser
- The "paloalto" is attached to the Source User within the Policy.
- Now, I am using 1 of those test account (dmzuser) to test the connectivity (from Winz7) but cannot access the internet.
Here is what I am finding, I keep on seeing "Unknown"
admin@PA-VM> show user ip-user-mapping all
IP Vsys From User IdleTimeout(s) MaxTimeout(s)
--------------------------------------------- ------------------- ------- -------------------------------- -------------- -------------
192.168.40.3 vsys1 AD palo\dmzuser 770 770 <<<<<<<< even though its listed I am unable to reach the internet.
192.168.20.1 vsys1 AD palo\pauser 2655 2655
192.168.20.3 vsys1 Unknown unknown 1 4
Total: 3 users
=======================
The host would just disappear:- 192.168.40.3 is the host where i am testing the connectivity from
admin@PA-VM> show user ip-user-mapping all
IP Vsys From User IdleTimeout(s) MaxTimeout(s)
--------------------------------------------- ------------------- ------- -------------------------------- -------------- -------------
192.168.20.1 vsys1 AD palo\pauser 2688 2688
Total: 1 users
There is no connectivity issue between the hosts/PA and AD
When i do Tracerotue from the test machine (192.168.40.3), I just get Request Timed Out...
- this is only when I have OU "paloalto" attached as Source.
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2021 04:49 AM
in your user identification settings, check if you have probing enabled. probing wil periodically send out a WMI probe to see if a user is still logged on, if the WMI user doesnt have enough privileges or the laptop firewall blocks the probe (or per the use case, the user is logged off or the laptop is shut down), the user will be unregistered from the user-ip mapping
also check your 'cache' as the default is 45 minutes which is too short in most cases (go for 9 hours which corresponds to the average kerberos ticket/time spent at work)
check to see if your mapped user corresponds to the group members:
show user group list
show user group name cn=paloalto,ou=firewall,dc=palo,dc=local
did you enable user-id in the dmz and trust zones (network > zones > enable user identification)
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2021 07:28 AM
Probing is enabled, Interval is set as default of 20min.
"also check your 'cache' as the default is 45 minutes which is too short in most cases (go for 9 hours which corresponds to the average kerberos ticket/time spent at work)"
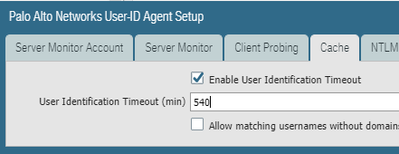
I increased "Cache" User ID Timeout to 540min, Commited…
Soon after committing, I got CONNECTIVITY....
traffic is being allowed.
Thank you very much for your help and guidance.
- 1 accepted solution
- 5779 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR Agent & MDE in Endpoint (Traps) Discussions
- Cortex XDR Broker VM content cashing verification in Cortex XDR Discussions
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- Cortex XDR – Unable to Assign Read/Write Permissions for Mobile Device (Detected as CD-ROM) in Permanent Exceptions in Cortex XDR Discussions
- Identify Manual Cases Using Filter - Layout Rules in Cortex XSIAM Discussions