- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Show hit count in CLI
- LIVEcommunity
- Discussions
- General Topics
- Show hit count in CLI
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-24-2015 05:26 AM
I was searching this forum and official documentation, but I can't find the following:
Is there equivalent to Cisco ASA "show access-list acl_name" command in the PAN-OS CLI. I am looking for the command that will show hit count for every configured security rule. Also if the object groups are used either in source or destination address it would be great if this command would show exact IP address that have hit count. Some thing like this:
access-list outside_in line 1 extended permit tcp any host 192.168.1.1 eq www (hitcnt=2176) 0x9e62d266
access-list outside_in line 2 extended permit tcp object-group PUBLIC_IPs host 192.168.1.2 eq smtp 0xd1a0241c
access-list outside_in line 2 extended permit tcp 1.2.3.0 255.255.255.192 host 192.168.1.2 eq smtp (hitcnt=5421) 0x13f4d6dc
access-list outside_in line 2 extended permit tcp 2.3.4.0 255.255.255.224 host 192.168.1.2 eq smtp (hitcnt=0) 0x9366dd12
access-list outside_in line 3 extended permit tcp any host 192.168.1.3 eq https (hitcnt=8957) 0x83457acc
All that I have found is this command that can show unused rules:
show running rule-use rule-base security type unused vsys vsys1
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-24-2015 03:29 PM
You cannot find this because the feature does not exist. PAN does not at this time track hit count at all. The unused rule feature is not hit count but simply a flag that is triggered when a rule is first used after reboot. As long as the rule was used at least once the rule will be removed from the unused rule list.
I am pretty sure hit counters are an existing feature request in the PAN database. If you contact your sales engineer you can get your companies vote for the feature request recorded.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2020 06:31 AM
For PAN-OS version 9.x, the hit counter is available via CLI using ---
show rule-hit-count vsys vsys-name vsys1 rule-base security rules all | match " 0 "
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2024 08:25 AM
@ChrisHuang Yes this command works on PAN OS 10.1 and above also
show rule-hit-count vsys vsys-name vsys1 rule-base security rules all | match " 0 "
NetGear_Adobe 0 - - - Fri Jul 28 23:20:20 2023 Fri Sep 29 18:21:48 2023
NetGear_Goto_Meeting 0 - - - Fri Jul 28 23:20:20 2023 Fri Sep 29 18:21:48 2023
TPLink_Zoom 0 - - - Thu Dec 7 10:04:11 2023 Thu Dec 7 10:04:11 2023
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-24-2015 03:29 PM
You cannot find this because the feature does not exist. PAN does not at this time track hit count at all. The unused rule feature is not hit count but simply a flag that is triggered when a rule is first used after reboot. As long as the rule was used at least once the rule will be removed from the unused rule list.
I am pretty sure hit counters are an existing feature request in the PAN database. If you contact your sales engineer you can get your companies vote for the feature request recorded.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-24-2015 10:39 PM
Hi there.
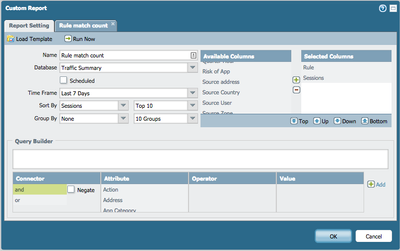
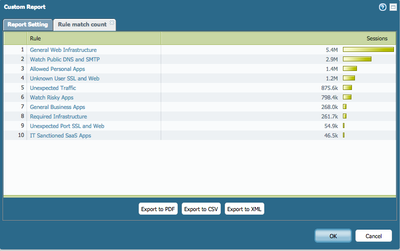
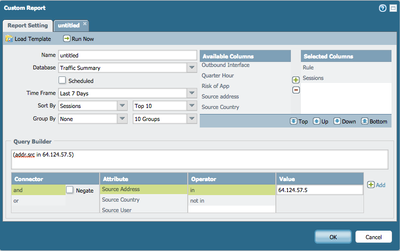
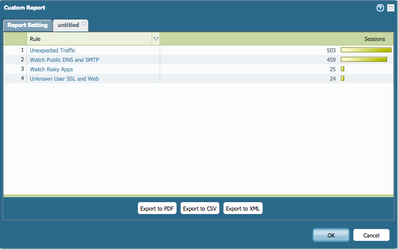
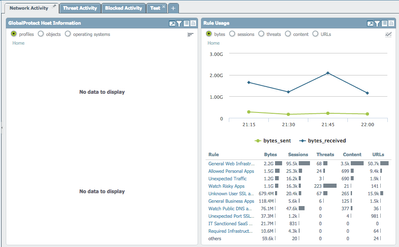
This is doable with custom reports, and has been for a long time. If you want to specify one specific source IP, you can do this with the query builder. See pictures. With 7.0 this is actually now visible in the ACC
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2015 05:14 AM
This is a nice work around but this is not a hit counter and not a CLI option as requested.
This custom report is looking a logged sessions over the report time period and further reporting by your filter choices.
The desired function is a BY RULE hit counter. Traffic hits the rule a counter is incremented and this continues until the cournter is reset manually or the firewall rebooted.
We typically use this during active live troubleshooting sessions to reset the counter and confirm traffic generated is live hitting the expected rule. Or to reset the counters after we think no more traffic should hit a rule and turn at a later time and confirm there is no increment of the counter.
The function is not yet implemented in PAN.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2015 06:54 AM
If you require a by-rule hit counter, please contact your Palo Alto Networks SE and vote for that feature request.
Aside from the custom report suggestion, I have one from the CLI as well. This doesn't necessarily "count" the rules, but it may be enough to confirm if traffic is hitting the expected rule or answer the question "when was the last time this rule was hit".
admin@pa0(active)> show log traffic direction equal backward rule equal 'deny any to dbl'
Time App From Src Port Source
Rule Action To Dst Port Destination
Src User Dst User End Reason
====================================================================================================
2015/11/25 07:31:24 not-applicable trust 58750 10.1.1.10
deny any to dbl deny untrust 80 46.21.151.38
policy-deny
2015/11/25 07:31:23 not-applicable trust 58749 10.1.1.10
deny any to dbl deny untrust 80 46.21.151.38
policy-deny
2015/11/25 07:31:21 not-applicable trust 58748 10.1.1.10
deny any to dbl deny untrust 80 46.21.151.38
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2015 08:18 AM
thanks for answer. We will certainly send our vote for this feature
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-30-2015 08:18 AM
Hello,
you could also run this for live sessions on a per-policy basis:
>show session all filter rule Rule_Name count yes (state active)
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2020 06:31 AM
For PAN-OS version 9.x, the hit counter is available via CLI using ---
show rule-hit-count vsys vsys-name vsys1 rule-base security rules all | match " 0 "
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2020 06:57 AM - edited 03-03-2020 06:58 AM
Gosh darnit Chris...What are you doing browsing 5 year old threads?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2024 08:25 AM
@ChrisHuang Yes this command works on PAN OS 10.1 and above also
show rule-hit-count vsys vsys-name vsys1 rule-base security rules all | match " 0 "
NetGear_Adobe 0 - - - Fri Jul 28 23:20:20 2023 Fri Sep 29 18:21:48 2023
NetGear_Goto_Meeting 0 - - - Fri Jul 28 23:20:20 2023 Fri Sep 29 18:21:48 2023
TPLink_Zoom 0 - - - Thu Dec 7 10:04:11 2023 Thu Dec 7 10:04:11 2023
Help the community: Like helpful comments and mark solutions.
- 3 accepted solutions
- 18505 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA1420 IKE packet disappear between receive (ingress) and firewall session state in General Topics
- while do the factory reset of pa 5250 showing error: findfs: unable to resolve 'label=sysroot0 in Next-Generation Firewall Discussions
- Do Palo Alto VMs support GCP N4 gve driver? in General Topics
- Address Group and Tag limitations in General Topics
- port issue / nmapping in Next-Generation Firewall Discussions