- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Juniper SRX Nat Support
- LIVEcommunity
- Tools
- Expedition
- Migration Tool Blogs
- Juniper SRX Nat Support
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
Juniper SRX Nat support has been added in version 3.2.2 for the first time. This Document describes the limitations of this new functionality.
The Configuration needs to be in XML format as usual in SRX migrations using the Migration Tool.
The command to generate the configuration in XML format is :
show configuration | display xml | no-more
Sanity Check: Once we have captured the output from the previous command ensure that the information saved on the file starts with the tag <configuration> and ends with </configuration>. Whatever tag before or after those must be removed.
Nat types Supported:
Source Translation: The pools are read but we are capturing only the IP-address (or range). commands like (in set commands to show only as example, we need the configuration in XML format)
set pool src-nat-pool-2 port no-translation set pool src-nat-pool-2 overflow-pool interface set pool src-nat-pool-2 port range 5000 to 6000
The Source nat rules will be translated as "dynamic-ip-and-port" in Palo Alto Networks. We will translate the sources with the pools previously defined or if the interface was used for that purpose. In the case to use the Interface the tool will assign the IP-address from the interface used.
Destination Translation: The MT will read the pools with the IP-address and ports. Those will be applied in the destination translation rules.
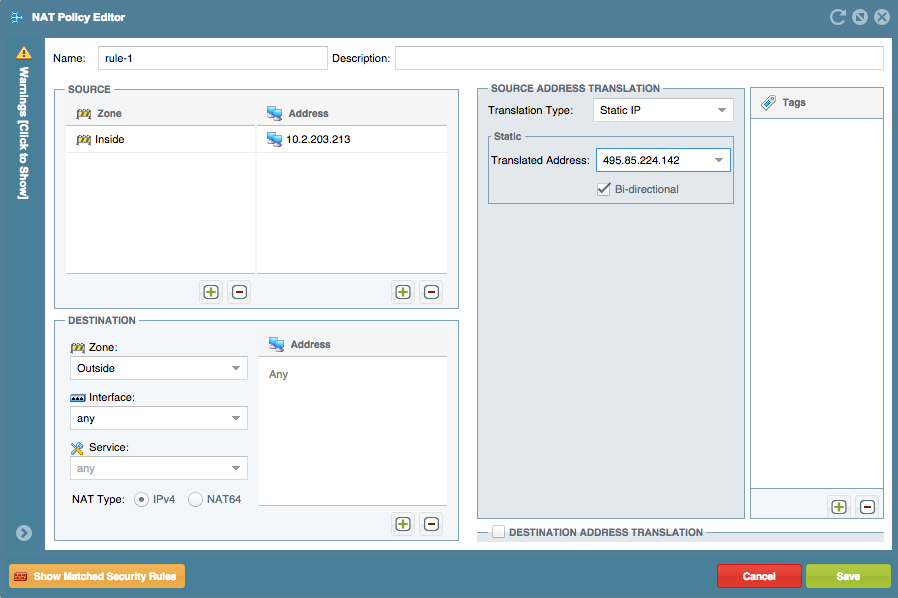
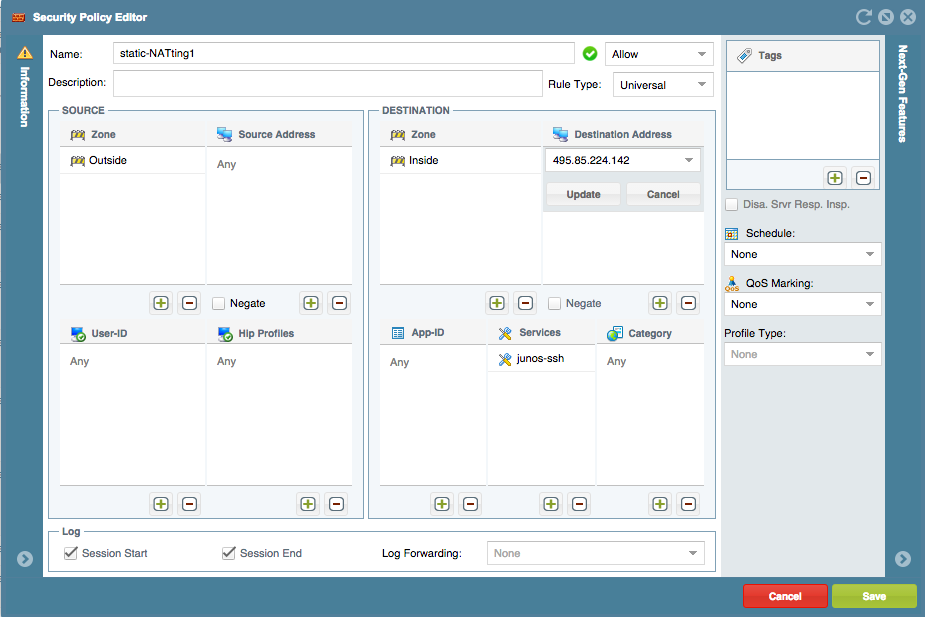
Static Translations: The MT will use the address (prefix) used in the static rule as a Source address in the Palo Alto Networks Nat Rule and the Destination will be used for the static address. We will active the bidirectional flag.
Fixes in the Security Rules: The MT will replace the objects in the security policy to match the address before the Nat is applied what is Palo Alto Networks firewall expects to find and then for all the Destination Translation or Static it will keep the zone for the post nat address. The limitation is the tool will replace object by object if a network is used in the security policy the tool will not fix those rules with the right pre-nat ip addresses.
Example
<static> <rule-set> <name>static-nat-Untrust</name> <from> <zone>Outside</zone> </from> <rule> <name>rule-1</name> <static-nat-rule-match> <destination-address> <dst-addr>495.85.224.142/32</dst-addr> </destination-address> </static-nat-rule-match> <then> <static-nat> <prefix> <addr-prefix>10.2.203.213/32</addr-prefix> </prefix> </static-nat> </then> </rule> </rule-set> </static>
How looks into the tool: Nat Rule
How looks into the tool: Security Rule
This is the first time we release support for SRX Nats so if you find something is not accurate just let us know and we will fix it.
thanks
- 11311 Views
- 0 comments
- 0 Likes
- Expedition retirement in Expedition Discussions
- Machine Learning support for newer PAN-OS Versions in Expedition Discussions
- Does the last version of Expedition support Panos 11.1.x code? in Expedition Discussions
- Can't import xml from any of my firewalls in Expedition Discussions
- Checkpoint to Palo Alto in Expedition Discussions