- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Access Expedition GUI Using Google Chrome
- LIVEcommunity
- Tools
- Expedition
- Expedition Articles
- Access Expedition GUI Using Google Chrome
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 10:06 AM - edited 05-15-2020 06:23 AM
Access Expedition GUI Using Google Chrome with Certification Error
Symptoms
Can't access Expedition GUI using Google chrome, error message 'NET::ERR_CERT_COMMON_NAME_INVALID' displayed as below screenshot, and you are not able to proceed to the website.
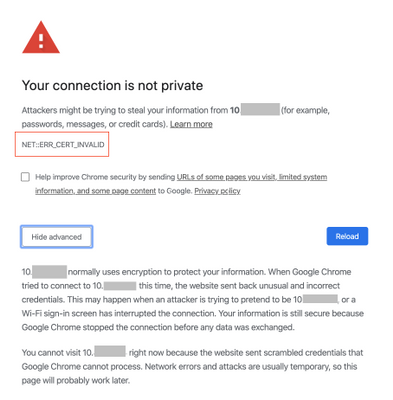
Diagnosis
For Google Chrome 58 and later, only the subjectAlternativeName extension, not commonName, is used to match the domain name and website certificate. If the certificate doesn’t have the correct subjectAlternativeName extension, users get a NET::ERR_CERT_COMMON_NAME_INVALID error letting them know that the connection isn’t private and will not provide you an option to proceed to the URL.
Please see the article for more details: https://support.google.com/chrome/a/answer/7391219?hl=en
Solution
Perform the below steps to re-install the self-signed certification with subjectAltName in Expedition:
-
SSH to Expedition
-
cd to /tmp
-
Modify req.conf by issue below command:
$ sudo vi req.conf
copy and past below section in req.conf, modify attributes in the file to match your organization
........................................................................................
[req]
distinguished_name = req_distinguished_name
x509_extensions = v3_req
prompt = no
[req_distinguished_name]
C = US ( Replace this with your county name)
ST = VA ( Replace this with your state name)
L = SomeCity ( Replace this with your city name)
O = MyCompany ( Replace this with your company name)
OU = MyDivision ( Replace this with your organization name)
CN = 192.168.44.131 ( Replace this IP with your Expedition IP )
[v3_req]
keyUsage = keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1 = 192.168.44.131 ( Replace this IP with your Expedition IP )
DNS.2 = company.com
DNS.3 = company.net
........................................................................................
saves the changes with ESC :wq!
-
Issue below commands in order:
$ sudo openssl genrsa -out server.key 3072 -config req.conf
$ sudo openssl req -new -x509 -key server.key -sha256 -out certificate.pem -days 730 -config req.conf$ sudo cp server.key /etc/ssl/certs/
$ sudo cp certificate.pem /etc/ssl/certs/
-
Modify the default-ssl.conf by issue below command:
$ sudo vi /etc/apache2/sites-enabled/default-ssl.conf
Find below two lines in the default-ssl.conf and replace the path
SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem
SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.keywith
SSLCertificateFile /etc/ssl/certs/certificate.pem
SSLCertificateKeyFile /etc/ssl/certs/server.keysaves the changes with ESC :wq
-
Restart Apache by issue below command:
$ sudo systemctl restart apache2
-
Try access the Expedition GUI again
Google chrome should now present you an option under "Advanced" to proceed to the URL.
I ran into this issue, but the above method did not work for me as I ran into errors from openssl on generating the certificate. It didn't like something in the request file. So I accomplished the above using the command below which takes you through a set of interactive prompts:
sudo openssl req -x509 -nodes -days 730 -newkey rsa:3072 -keyout /etc/ssl/private/server.key -out /etc/ssl/certs/certificate.pem
I then ran through the rest of the commands above to replace the default certificate with a self-signed certificate that was generated. And then I opened Google Chrome to go to the webpage for Expedition and alas, it DIDN'T work! I got the same error as before:
NET::ERR_CERT_INVALID website sent scrambled credentials Self-signed Certificate
And no option to proceed. Well, this was frustrating, especially after checking this on Firefox and seeing that it works. After googling this around, I came up on a solution that I hope would help others here. When you hit the webpage for Expedition using Google Chrome and come across this error without an option to proceed, just type:
badidea
or:
thisisunsafe
And voila! The webpage will come right up. Hope this helps!
Quick fix:
The proper key name for "T = VA" is ST (state).
As-is, you'll get this error:
x509 certificate routines:X509_NAME_ENTRY_create_by_txt:invalid field name:x509name.c:295:name=T
- 21253 Views
- 2 comments
- 2 Likes
- Bug with Expedition UI when using Chrome in Expedition Discussions
- MIgration from Google cloud to IBM Cloud. in Expedition Discussions
- Introducing Expedition 2 Beta [Program Concluded] in Expedition Articles
- Expeditions stopped accepting Syslog in Expedition Discussions
- Issues with ML with Logs Forward from Panorama in Expedition Discussions
-
address to ip address
1 -
addressgroups
1 -
Administrator's Guide
1 -
App-ID
1 -
attach device
1 -
Authentication
1 -
Best Practice Assessment
1 -
Best Practices
1 -
BPA
1 -
caveats
1 -
checkpoint R80
1 -
connection
1 -
CVE-2021-44790
1 -
Dashboard
1 -
database
1 -
devices
1 -
DNS
1 -
documentation
1 -
edit
1 -
Expedition
32 -
export
1 -
Filtering
1 -
filters
1 -
Gaia
1 -
Google Chrome
1 -
How to
1 -
import
3 -
installer
1 -
Iron Skillet
1 -
IronSkillet
1 -
LDAP
1 -
Logs
1 -
Machine Learning
2 -
migrate
1 -
Migration
2 -
Migration Tool
3 -
Objects & Security Profiles
1 -
one member
1 -
optimization
3 -
panreadorders
1 -
permissions
1 -
php
1 -
policies
1 -
policy
1 -
predefined filters
1 -
project
1 -
queue
1 -
rbac
1 -
roles
1 -
Rule
1 -
search and replace
1 -
settings
2 -
sharing
1 -
srx
1 -
task manager
2 -
Tools
1 -
Ubuntu 16.04 LTS
1 -
Ubuntu 20.04
1 -
users
1 -
Zones
1
- Previous
- Next




