- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect Pre-Logon NULL issue
- LIVEcommunity
- Discussions
- General Topics
- GlobalProtect Pre-Logon NULL issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
GlobalProtect Pre-Logon NULL issue
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-06-2020 03:20 PM
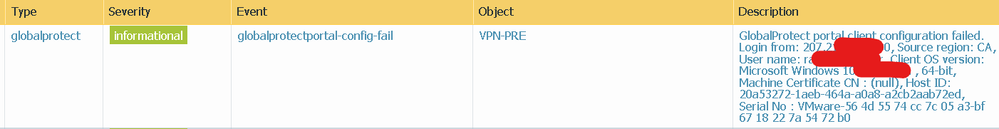
Trying to setup new config for pre-logon, seems to be not working. I am getting machine certificate null error.
First i was using internal PKI but then i found this KB and i was hitting the same issue.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClR8CAK
I then tried to setup with self generated certs, while i have asked the system admin team to add subject info, but still having same issue.
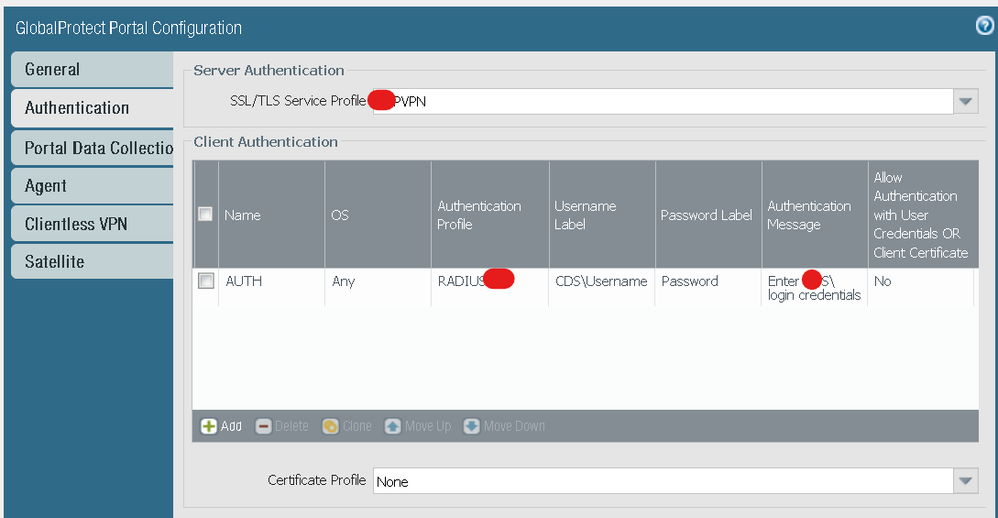
Below are portal config screenshots, i don't know what i am missing. PANOS 9.0.8, GP 5.1.4
External Gateways in both agent configs point to same public fqdn/ip
I have also tried selecting both options below
Server Authentication below uses public cert, while certificate profile use self generated root CA on firewall.
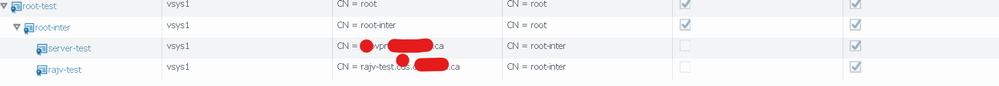
Below are the local root CA and profile screenshots
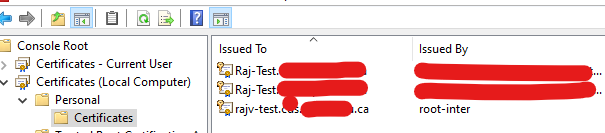
Certificate imported in to personal store of local machine, generated on firewall.
On reinstall of Agent it asks to select certificate which is this that i select and get not authorized message.
Also imported root certificate from firewall in trusted certs.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-06-2020 06:21 PM
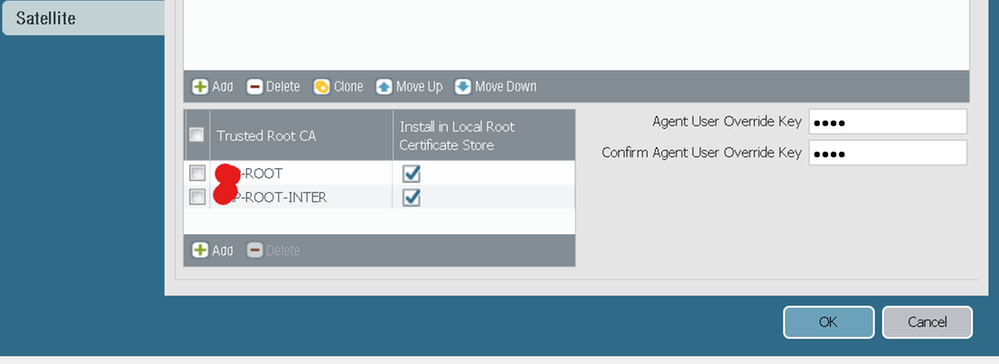
Seems you need Root and Intermediate Cert in Device and Certificate profile.
Also your Machine cert need to be part of
Root
Intermediate
Machine
When you create Machine cert then it need to be signed by Intermediate cert.
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-06-2020 10:24 PM
@MP18 As per your suggestion i have made below changes. new root > inter > sever cert created
Included them in server profile used in Gateway authentication config tab
exported and imported rajv-test.xxx.yyy.ca from firewall into Windows local store.
reinstalled GP and tried connection, same result. Null with not authorized.
And this time i did not see any popup from GP for which cert to use from the local store.
Am i generating machine cert rajv-test right, do i need to include server-test cert somewhere.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-07-2020 10:53 AM
@MP18 I have updated the config now with actual certs that are to be used, no self generated certs, but still hitting the same issue.
Test PC has both root and intermediate certs from our internal PKI. Machine cert pushed by GroupPolicy with subject field populated.
Portal authentication uses public cert in ssl-tls profile and none in certificate profile.
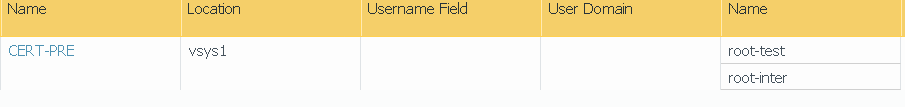
under agent tab root and intermediate certs from internal PKI are selected.
Gateway authentication uses same public cert ssl-tls profile and cert profile with root and intermediate in it from internal PKI
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-07-2020 11:50 AM
This is what i have observed now.
Including the group that works in On-demad mode, pre-logon config fails
If any users is set, user gets authenticated but i still don't see any pre-logon happening
| Portal Authentication | Connect Method | Working |
| cn=emp,ou=groups,ou=emp,dc=aaa,dc=bbbbb,dc=ca | On-Demand | Yes |
| Portal Authentication | Connect Method | Working |
| pre-logon | pre-logon (always-on) | No |
| cn=emp,ou=groups,ou=emp,dc=aaa,dc=bbbbb,dc=ca | pre-logon (always-on) | No |
| Portal Authentication | Connect Method | Working |
| pre-logon | pre-logon (always-on) | No |
| Any | pre-logon (always-on) | Yes |
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-07-2020 12:38 PM - edited 07-07-2020 12:59 PM
Machine Cert need to be imported in both Local user and Local machine in Certificate Store - Personal on each machine.
Under Portal and Gateway Authentication for SSL/TLS profile has to be same
And also the Certificate profile under authentication in Portal and gateway has to be same
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-07-2020 01:34 PM
Thanks @MP18 I did not need to import to Local user store, but fixing the cert config did fix the issue.
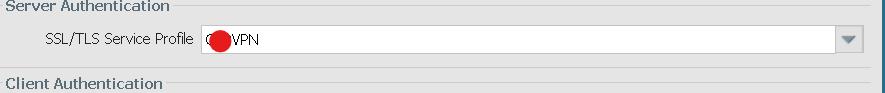
Portal/Gateway authentication - SSL/TLS profile - This is using Public cert
Portal/Gateway authentication - Certificate Profile - This is using internal PKI root and intermediate certs
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-07-2020 07:10 PM
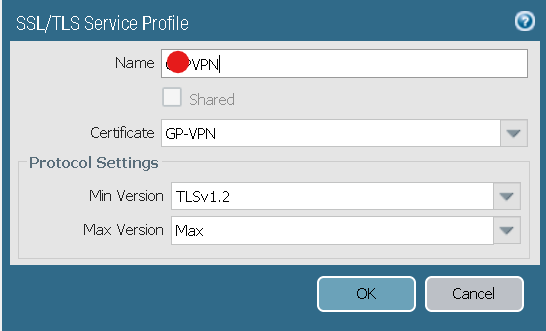
Make sure Cert in SSL/TLS profile has CN the FQDN of the VPN url and is trusted by the PA and end user.
Portal/Gateway authentication - Certificate Profile - This is using internal PKI root and intermediate certs
My assumption is that if you are using Cert PRofile with internal root and intermediate certs need to be same as Cert in SSL/TLS profile -
Can you please test by using either external Root or Internal Root certs and intermediate certs for both SSL/TLS and Certificate Profile?
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-07-2020 10:52 PM - edited 07-07-2020 10:55 PM
@MP18 I am pasting all the relevant screenshots of my config, and since all the documentations show config with self generated certs. This is with actual public cert and internal certs.
SSL/TLS Profile used in both portal and gateway configs
SSL/TLS Profile config
above ssl-tls profile refers this Public Certificate
Portal > agent > config >External refers public fqdn
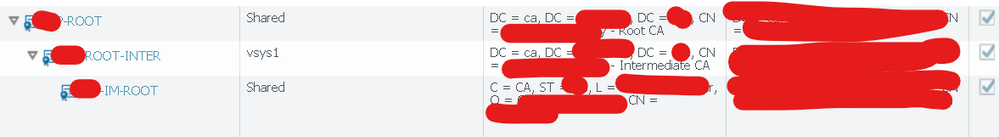
portal > agent > root and inter certs added here issued from internal certificate authority
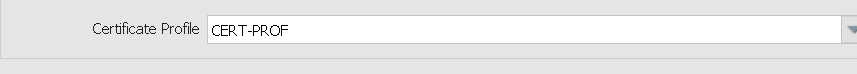
Certificate profile used in both portal and gateway configs
Certificate profile config referring same internal certificates
Internal certs added to firewall. In case someone my wonder about 3rd IM-ROOT below, we had setup that previously for decryption.
ROOT and ROOT-INTER and Machine cert are automatically pushed to PC by Group Policy under Local Computer. I don't know why 2 are pushed. And as per earlier mentioned KB Subject field should not be empty and refers to the PC name.
Status at login screen on reboot
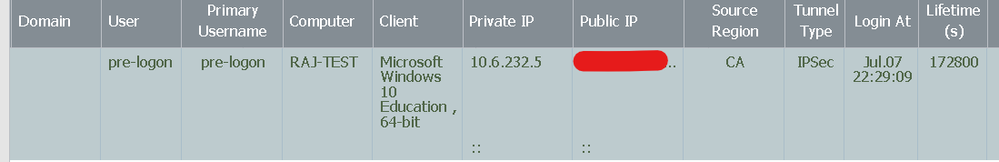
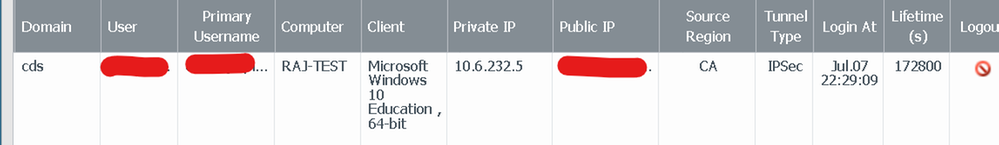
Tunnel status on firewall before usre logs in to PC, that is the previous screenshot state. User is pre-logon
Tunnel status after user logs in, connection is automatically established if credentials have been entered before.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-08-2020 08:00 PM
So As per these logs it seems pre logon is working.
Does the user name pre logon to the specfic user as configured in LDAP profile?
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2020 07:54 AM
@MP18Yes it logs as the user according to the ldap profile.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2020 08:43 AM
So seems then it is working as expected now ?
Help the community: Like helpful comments and mark solutions.
- 12264 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA Global Protect in GlobalProtect Discussions
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- stream timeout in General Topics
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions