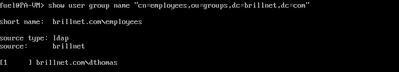- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Group Based network policy not being blocked.
- LIVEcommunity
- Discussions
- General Topics
- Re: Group Based network policy not being blocked.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Group Based network policy not being blocked.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-26-2024 12:38 PM
Hello,
I have an openldap server setup as well as an LDAP policy and group mapping on the Palo Alto firewall.
When I run the 'show user group name "cn=employees,ou=groups,dc=brillnet,dc=com". I can see the users in the group just fine. Refer to the output below.
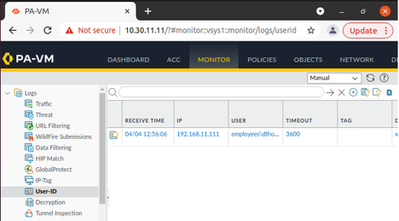
I am using the UserID xml api to associate group/user to ip mappings. Calls to the api are working when a user logs into the openldap server. I know this because I can see the user-id tagging in the api log, refer to the screenshot below.
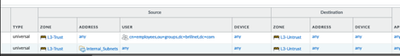
I created a policy that blocks any user in the employees group referenced in the screenshots above. Refer to the output below.
However the above deny is not working. Does anyone know why this is happening?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-27-2024 09:11 AM
Hello,
Have you enabled User identification when you configure L3-trust security zone?
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/user-id/enable-user-id
If you don't enable user identification on source zone, then the security policy will not take into account User-ID info.
Cosmin
Don't forget to Like items if a post is helpful to you!
Please help out other users and “Accept as Solution” if a post helps solve your problem!
Read more about how and why to accept solutions.
Disclaimer: All messages are my personal ones and do not represent my company's view in any way.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2024 05:08 AM - edited 04-29-2024 09:28 AM
Hello,
Thank you for your reply. Yes, user identification is enabled on the trust zone. Refer to the screenshot below.
- 1895 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Trying the DNSProxy feature for Static Response in General Topics
- Problem with downloading PAN OS in General Topics
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- LGTV and Netflix bugs out when going through Palo Alto in General Topics