- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Issue with NAT over Site-2-Site VPN
- LIVEcommunity
- Discussions
- General Topics
- Issue with NAT over Site-2-Site VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Issue with NAT over Site-2-Site VPN
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2016 11:21 PM
Hi there,
I am reasonably good with Palo Alto Firewall however struggling with the NAT over VPN. I am trying to hide some internal IPs behind 9.9.0.1/32 and 9.9.0.1/32 is configured in Proxy ID as Local host. VPN phase 3 comes up but i think the way i am doing NAT is wrong.
NAT policy is created is as follows
Source Zone Destination Zone Sourec Address Destination Address Destination Translation
VPN T rust 10.1.0.1 9.9.0.1 Internal Host 10.129.34.9
When i check on CLI it tells me that request for 9.9.0.1 will be translated to 10.129.34.9
PA-1(active)> test nat-policy-match source 10.1.0.1 destination 9.9.0.1 protocol 70
Destination-NAT: Rule matched: Total_VPN_NAT-1
9.9.0.1:0 => 10.129.34.9:0
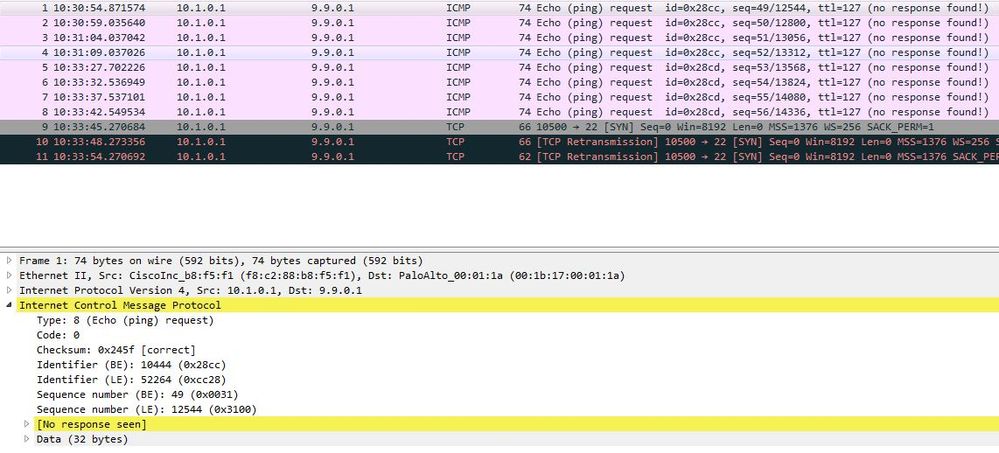
I dont see request coming when i monitor the traffic. However when i packet capture i do see ping request coming but it dies off becuase of no return response.
Can someone help or suggest what could be wrong please?
Many Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2016 12:11 AM
No i wudn't say ping comes thru because i dont see anything in monitor tab however when i capture the packet using packet capture tool i do see ping coming but my firewall isn't responding.
Routing is not a problem because other Proxy IDs are working fine. It only this specific IP which i am trying to NAT is having problem.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2016 12:18 AM
This packet isn't translated, it has original destination 9.9.0.1. Seems your NAT isn't working.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2016 12:27 AM
Thats what i think as well however when i check the CLI is does say 9.9.0.1 will be translated to 10.129.34.9.
PA-1(active)> test nat-policy-match source 10.1.0.1 destination 9.9.0.1 protocol 70
Destination-NAT: Rule matched: Total_VPN_NAT-1
9.9.0.1:0 => 10.129.34.9:0
Is there any way to check why my NAT rule isnt working please?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2016 01:10 AM
Is 9.9.0.1 in trust zone? If it isn't, NAT won't hit.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2016 02:01 AM
Hi nvirmani,
When you run a test nat policy command, try putting in the 'to' & 'from' fields to include the zones, as your NAT rule is done with zones. Personally I always make the test commands as accurate as possible for the best results.
Ben
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2017 10:51 AM
Hello
I'm having a very similar issue with trying to configure a NAT translation from VPN to Trusted zone. In my case I'm building a VPN tunnel for monitoring using /32 ProxyIDs. My configuration VPN ProxyID is like the example below:
Remote: Local:
3.3.3.3/32 172.25.40.3/32
My NAT is configured as follows.
Source Zone: Dest Zone: Source Address: Dest Address: Destination Trans:
VPN Trusted 3.3.3.3/32 172.25.40.3/32 10.100.10.10/32
I can't get the translation to happen when send pings from the VPN and that's what I need working.
If I switch from a Dest translation to Source translation it works when I ping from Trust to VPN.
Source Zone: Dest Zone: Source Address: Dest Address: Source Trans:
Trusted VPN 10.100.10.10/32 3.3.3.3/32 172.25.40.3/32
What am I missing? Do I need to add a static route for the V-Router? To get to 172.25.40.0/32 use tunnl.x?
Please advise. Thanks.
Ben
- 5232 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Tuning Panorama HA Timers to Stop False HA1 Alerts over MPLS in Panorama Discussions
- Cortex XDR 8.9 Non-Persistent Citrix Servers and Cache Write Issue in Cortex XDR Discussions
- Windows Installer DB: Current agent installation is missing in Cortex XDR Discussions
- About PAN-183404 in Next-Generation Firewall Discussions
- About PAN-293673 in Next-Generation Firewall Discussions