- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
multiple VLANs on one security zone - possible?
- LIVEcommunity
- Discussions
- General Topics
- Re: multiple VLANs on one security zone - possible?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
multiple VLANs on one security zone - possible?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-16-2013 01:12 AM
Hi
I need your help with one (probably simple for You problem).
I have PA200 but I have only one "free" security zone and one phisical interfece free.
I need to create 4 local networks (as a subinterfaces/VLAN) that every one has their own adresses, dhcp server, NAT policy to their own IP.
Intervlan traffic shouldn't be allowed.
Is it possible? Until now I do always one security zone per one network ...
With regards
Slawek
- Labels:
-
Configuration
-
Networking
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2013 03:21 AM
I was stuck with one thing, one of this local networks must have Captive Portal on it.
I can connect proper profile to interface for CP but the CP policy I need to bind to whole Security Zone. I can do exclussions - but is it a good idea?
I doubt, and I would like to ask you whether it is good that I am doing
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2013 03:36 AM
Hi,
No profile for CP but Captiv Portal Policy 🙂 then no issue
v.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2013 11:23 AM
You can create a specific Captive Portal rule based on Source IP subnets .
No-CP rules can be created for IPs that do not need CP ,for granularity if certain IPs need exclusion from CP in an address space.
Additionally ,User-Identification Include (/Exclude) ACLs could be created ,if Zone has multiple interfaces/Subnets ,to filter the IP spaces that need (/dont need) User Id via CP.
HTH
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2013 04:47 AM
Hello
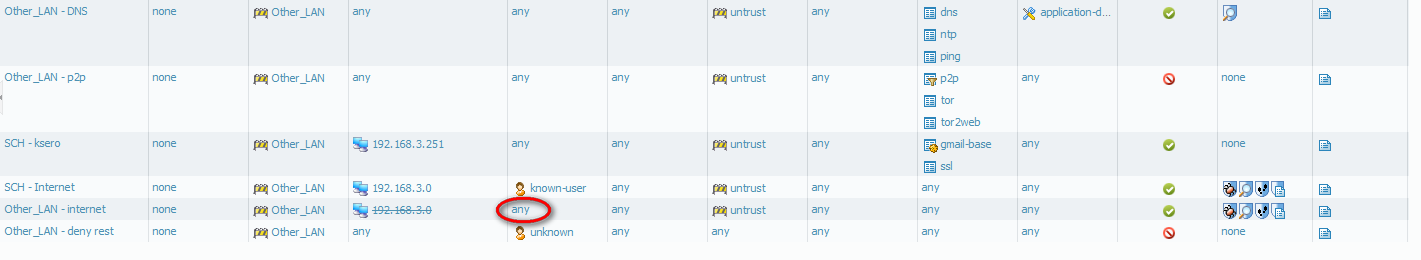
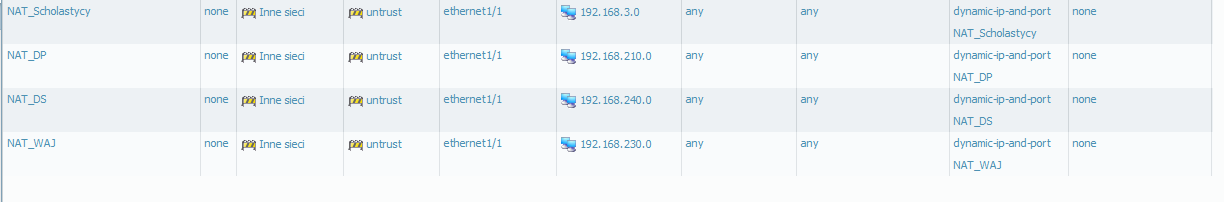
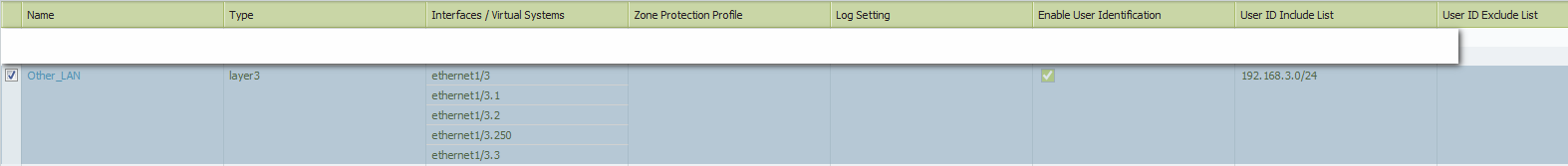
I stuck with configurations .... help me please. My config look like:
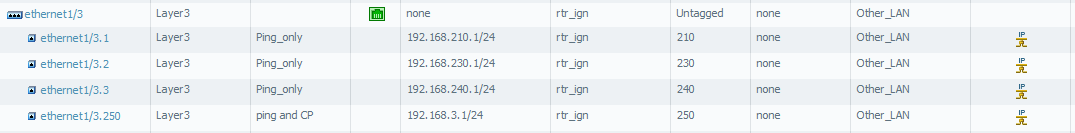

Computer connected to VLAN 210 is able to get IP address from DHCP server (got 192.168.210.2) but is unable to ping gateway in this network (192.168.210.1). Of course it can't ping 8.8.8.8 too
Why?
It's doesnt matter that "any" or "unknown" is chooses in security policy "Other_LAN - internet" - computer cant reach internet or gateway.
User identyfiaction is enabled on "Other_LAN" because I have to do Captive Portal on 192.168.3.0 network (and only on this network)
Computer connected to VLAN 210,230,240 getting IP from DHCP (can't ping gateway), but connected to vlan 250 doesn't even getting IP from DHCP server.
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2013 06:12 AM
Computer connected to VLAN 210 is able to get IP address from DHCP server (got 192.168.210.2) but is unable to ping gateway in this network (192.168.210.1).
Could be getting blocked by the rule deny-rest.Configure a rule above deny-rest rule between zones Other_LAN to Other_LAN to allow this traffic.
Of course it can't ping 8.8.8.8 too
Can you check the Source NAT rule,Shouldn't the Innie siece zone be replaced by OTHER_LAN zone ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2013 08:27 AM
Computer connected to VLAN 210,230,240 getting IP from DHCP (can't ping gateway), but connected to vlan 250 doesn't even getting IP from DHCP server.
A: You don't have it enabled. It shows as disabled.
As Nadir said, your NAT rules need to be from the correct source zone.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2013 11:52 PM
Yes - the traffic was blocked by deny-rest rule.
I added policy from Other_LAN to Other_LAN and now I can ping gateway of network where is locted computer. BUT also I can ping other VLAN gateways!! - that's not good.
Is it a solution for "clever" blocking traffic from ie. vlan250 to every other. At the moment I have 4 networks on Other_LAN interface so I had to 4^2 rules of blocking traffic - is it a solution to do it a bit smarter?
Every of this subinterfaces/networks must be separated, and allow only traffic to the internet (exept for DHCP/DNS/CP).
Sorry for my english ... I hope that you are understand what I want to achieve.
Craymond - you are right, it was disbaled - it's my fault - thx
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 01:20 AM
I have another problems with computer in 192.168.3.x network.
I can't see CaptivePortal, my browser isn't redirected (even when I add rule that allow traffic to it's IP (192.168.110.1) - rule "SCH-CP" - but I can ping it by IP address or name.
I changed dns servers from google dns to my local dns serwers for every of my local network - just for unifications.
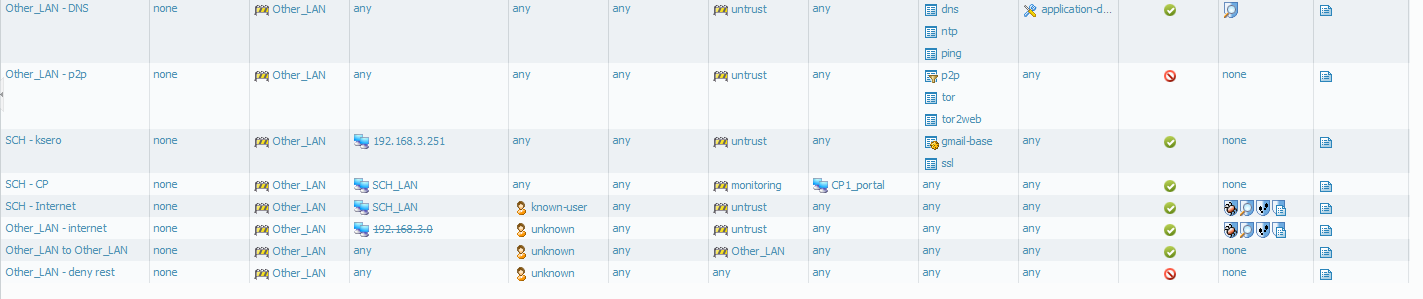
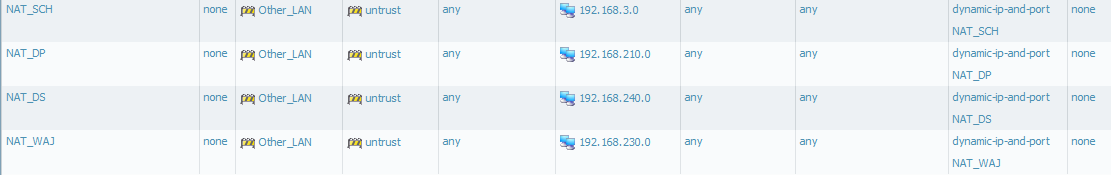
so the problem is in NAT (I can't see errors in configuration, picture from yesterday has polish name of Other_LAN - so it's confusing you) - configurations is similar to my others NAT.
when I try ping google.pl I see traffic that passes rule "Other_LAN - DNS" but my computer dosn't resolve name to it's IP.
I can't ping or browse internet on every LAN on Other_LAN security zone.
I don't understand what is going here, I have 7 other LANs on my PAN device (every has their own security zone) and everyting is working as I expected. When I started to configure 4 LANs on one security zone something is going creazy ...
Please explain me why I need to allow traffic from Other_LAN to Other_LAN to bo able to ping gateways when without such security rule I was able to get IP from DHCP server??
Help me please
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 01:40 AM
By default firewall allows ,Intra-Zone traffic.So you can ping all hosts in Other_LAN to hosts in Other_LAN by default if you dont have deny-rest Rule.You can either create separate Zone for each VLAN.
Having deny-rest rule would warrant creation of specific allow rules from Other LAN to any zone.
Suggestions : You can alter the deny rest to specific zones instead of any. eg Other Zone to Untrust.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 01:45 AM
"so the problem is in NAT (I can't see errors in configuration, picture from yesterday has polish name of Other_LAN - so it's confusing you) - configurations is similar to my others NAT."
Check if you have a zone named inne sieci configured.I dont think Zone names would be translated.
Change "Inne sieci" in NAT config to Other_LAN
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 01:58 AM
it's done today morning, now it's looks like:
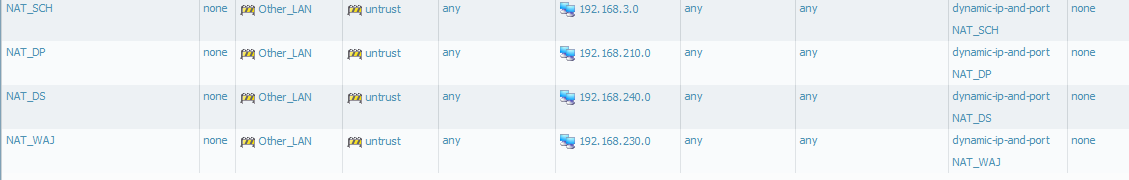

- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 02:19 AM
What do you see in the traffic logs for the outbound traffic failing ?
Can you include additional columns in the traffic log eg : NAT Source IP,Packets sent Packets received etc.
Do you have Default route defined ?
Can try to include the Interface in the Source NAT rule instead of the translated address.
- 10217 Views
- 19 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Best practices for Palo Alto security policy when destination IP/FQDN is dynamic or unknown in Next-Generation Firewall Discussions
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Inquiry regarding Tenant Backu & Recovery in Cortex XDR Discussions
- port issue / nmapping in Next-Generation Firewall Discussions
- Understanding the Agent Security Problem in AI Runtime Discussions



