- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
NAT sessions
- LIVEcommunity
- Discussions
- General Topics
- Re: NAT sessions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-24-2013 03:47 PM
Hello All,
Is anyone know how to see or debug nat translations on PAN device, similar like "sh ip nat translation" on cisco devices?
Txs...
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2013 07:01 AM
Hello Tician,
Here are some of the useful commands for NAT troubleshooting ( "nat-inside-2-outside" is the rule used for reference):
> show running nat-policy // Show currently deployed NAT policy
> show running nat-rule-cache // Show all NAT rules of all versions in cache
> show running nat-rule-ippool rule nat-inside-2-outside // NAT rule ippool usage
> debug dataplane nat sync-ippool rule nat-inside-2-outside // To kill sessions pertaining to a particular NAT rule and re-sync the ippool
>> For a particular session, the NAT translation can be viewed as:
admin@88-PA-VM-300> show session all filter application ping
--------------------------------------------------------------------------------
ID Application State Type Flag Src[Sport]/Zone/Proto (translated IP[Port])
Vsys Dst[Dport]/Zone (translated IP[Port])
--------------------------------------------------------------------------------
172307 ping ACTIVE FLOW NS 192.168.88.206[512]/trust-L3/1 (10.66.24.88[512])
vsys1 4.2.2.2[6912]/untrust-L3 (4.2.2.2[6912])
admin@88-PA-VM-300> show session id 172307
Session 172307
c2s flow:
source: 192.168.88.206 [trust-L3]
dst: 4.2.2.2
proto: 1
sport: 512 dport: 6912
state: INIT type: FLOW
src user: unknown
dst user: unknown
s2c flow:
source: 4.2.2.2 [untrust-L3]
dst: 10.66.24.88
proto: 1
sport: 6912 dport: 512
state: INIT type: FLOW
src user: unknown
dst user: unknown
start time : Mon Nov 25 08:50:18 2013
timeout : 6 sec
total byte count(c2s) : 74
total byte count(s2c) : 74
layer7 packet count(c2s) : 1
layer7 packet count(s2c) : 1
vsys : vsys1
application : ping
rule : trust-2-untrust
session to be logged at end : True
session in session ager : False
session synced from HA peer : False
address/port translation : source + destination
nat-rule : nat-inside-2-outside(vsys1)
layer7 processing : enabled
URL filtering enabled : True
URL category : any
session via syn-cookies : False
session terminated on host : False
session traverses tunnel : False
captive portal session : False
ingress interface : ethernet1/4
egress interface : ethernet1/3
session QoS rule : N/A (class 4)
Probably you might have done this, but you can also bookmark this document for future reference:
Let me know if that is what you were looking for!
Thanks and regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2013 07:01 AM
Hello Tician,
Here are some of the useful commands for NAT troubleshooting ( "nat-inside-2-outside" is the rule used for reference):
> show running nat-policy // Show currently deployed NAT policy
> show running nat-rule-cache // Show all NAT rules of all versions in cache
> show running nat-rule-ippool rule nat-inside-2-outside // NAT rule ippool usage
> debug dataplane nat sync-ippool rule nat-inside-2-outside // To kill sessions pertaining to a particular NAT rule and re-sync the ippool
>> For a particular session, the NAT translation can be viewed as:
admin@88-PA-VM-300> show session all filter application ping
--------------------------------------------------------------------------------
ID Application State Type Flag Src[Sport]/Zone/Proto (translated IP[Port])
Vsys Dst[Dport]/Zone (translated IP[Port])
--------------------------------------------------------------------------------
172307 ping ACTIVE FLOW NS 192.168.88.206[512]/trust-L3/1 (10.66.24.88[512])
vsys1 4.2.2.2[6912]/untrust-L3 (4.2.2.2[6912])
admin@88-PA-VM-300> show session id 172307
Session 172307
c2s flow:
source: 192.168.88.206 [trust-L3]
dst: 4.2.2.2
proto: 1
sport: 512 dport: 6912
state: INIT type: FLOW
src user: unknown
dst user: unknown
s2c flow:
source: 4.2.2.2 [untrust-L3]
dst: 10.66.24.88
proto: 1
sport: 6912 dport: 512
state: INIT type: FLOW
src user: unknown
dst user: unknown
start time : Mon Nov 25 08:50:18 2013
timeout : 6 sec
total byte count(c2s) : 74
total byte count(s2c) : 74
layer7 packet count(c2s) : 1
layer7 packet count(s2c) : 1
vsys : vsys1
application : ping
rule : trust-2-untrust
session to be logged at end : True
session in session ager : False
session synced from HA peer : False
address/port translation : source + destination
nat-rule : nat-inside-2-outside(vsys1)
layer7 processing : enabled
URL filtering enabled : True
URL category : any
session via syn-cookies : False
session terminated on host : False
session traverses tunnel : False
captive portal session : False
ingress interface : ethernet1/4
egress interface : ethernet1/3
session QoS rule : N/A (class 4)
Probably you might have done this, but you can also bookmark this document for future reference:
Let me know if that is what you were looking for!
Thanks and regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2013 07:04 AM
Hi,
Agree with Kadak but you can also enable "pre source NAT adress / Post NAT source adress" and "pre destination NAT adress / Post destination NAT adress" colum in monitor traffic page. And in this case, with no CLI, you have all info.
Hoipe help
Vincent
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2013 07:18 AM
Hello Tician,
As Vince stated earlier this is how it looks in Monitor Logs if we can enable the columns what is needed to be viewed.
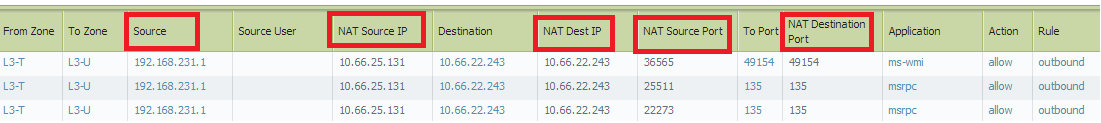
We can enable the required columns by moving the cursor to the right most section of any column header where we get a drop down to select columns.
Hope this helps. !
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-26-2013 06:04 AM
Hello Tician,
As Phonenix said, you can look there. But you also can look in CLI, or Monitor Session...
show session all filter (filters) you can see what policy NAT the session passed.
Best Regards
- 1 accepted solution
- 32136 Views
- 4 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA1420 IKE packet disappear between receive (ingress) and firewall session state in General Topics
- port issue / nmapping in Next-Generation Firewall Discussions
- Update from 10.1.14-h13 to 11.1.13 in Next-Generation Firewall Discussions
- False positive (generic.ml): HelpDesk Viewer in VirusTotal
- False Positive request for RemotePC HelpDesk Viewer in VirusTotal



