- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Nominated Discussion: Global Protect Authentication Happened Two Time While Using RADIUS
- LIVEcommunity
- Articles
- General Articles
- Nominated Discussion: Global Protect Authentication Happened Two Time While Using RADIUS
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 10-19-2022 06:55 AM
This article is based on a discussion, Global Protect authentication happened two time while using RADIUS, posted by @AhamadullahM and answered by @Astardzhiev. Read on to see the discussion and solution!
We have faced the Global Protect authentication that happened two times while using the RADIUS server.
First, I am trying to connect to VPN and enter the user name and Password after the OTP has asked then entered the OTP after, again the user name password is asked then OTP is provided after VPN was connected.
We need to avoid the twice authentication.
Kindly help to fix the issue.
This is by design, let me try to break down why it's happening and what you can do.
GlobalProtect VPN consist of two main components — the Portal and Gateway. For sake of simplicity let's say that every time the VPN user connects he will first connect to the Portal and then to the Gateway:
- User will connect to GP Portal, which will provide information of how the GP client will behave and to which Gateways it should try to connect.
- User will then try to establish a connection to the provided Gateways. At this point the VPN tunnel is established and the client is provided with routing information on which traffic to forward over the tunnel.
Now, both of these connections (to Portal and to Gateway) require authentication. Which means GP client will always authenticate twice - once to the Portal and once to the Gateway. This behavior is usually hidden to the end-user when using simple user/password authentication. By default GP client will cache the entered credentials. So when the user is prompted to authenticate to the Portal, the client will cache those credentials and use those first when prompted to authenticate to Gateway. If the gateway uses the same authentication (which is in most of the cases), the user will be connected to the Gateway without being prompted to authenticate a second time. But on the background there is actually second authentication.
This is important, because in your case your are using OTP. OTP is meant to be used one-time (according to its name, right). So when user is prompted by the Portal to authenticate, he will provide the username and password, will be challenged with OTP and he will provide it. After that, the client will receive the list of Gateways and will need to authenticate to the Gateway. The firewall will first try to use the cached credentials, so it will provide the same OTP that was used to authenticate to the Portal. In this case the OTP provide will reject the authentication, because it will notice that OTP is re-used. Failed authentication will force the client to prompt user to re-enter credentials, which will be accomplished with fresh OTP.
As you can see, it is not actually a problem of the RADIUS, but how GlobalProtect actually works.
Of course, user experience is very important in such cases, so there is one solution, probably more of a workaround, but since it is the only possible solution I would say it becomes standard.
Two words: Authentication Override.
GlobalProtect provides you with option to generate an authentication cookie once the user is successfully authenticated. This cookie will be stored on the user's computer and has a configurable life time. The purpose of this cookie is to authenticate the user. Instead of using the authentication method you have setup for your GlobalProtect, the flow would be like this:
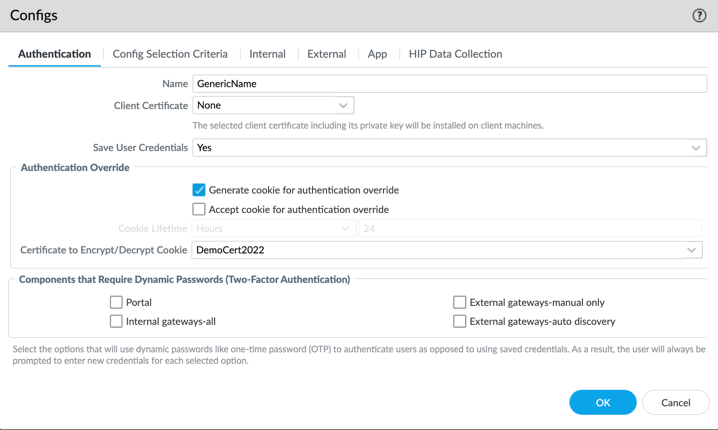
- Configure GP Portal to generate an authentication cookie. (Do not enable accept auth cookie, only generate)
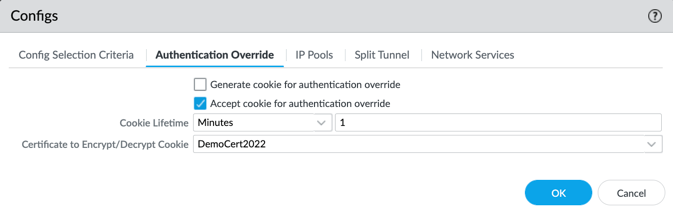
2. Configure GP Gateway to accept authentication cookie with life time of 1min. (Do not enable generate, only accept)
What will happen is:
- User will be prompted by Portal to authenticate
- User will provide valid username, password and OTP
- Portal will generate auth cookie valid for the next one minute. It will be sent to the client along with the list of Gateways
- GP client will try to connect to GP gateway providing it the auth cookie
- Gateway will validate the cookie and if valid (not expired and not tampered) it will connect the user straight away without prompting the user to authenticate again
For the enduser it looks like he is authenticated only once and connected to the VPN.
When the user disconnects and tries to connect again to the Portal, since portal does not accept auth cookie, it will ask the user to authenticate again with OTP.
If the user tries to connect directly to Gateway (which accepts cookies), the gateway will try to validate the cookie, but it will notice it has expired and will prompt the user to authenticate with OTP.
If you search for MFA/OTP with RADIUS in the form you will find a lot of other discussions, where you could even find more detailed config examples.
I configured the same settings but it doesn't work in my case.
In the GP logs I can see that the cookie is generated at the portal log on but it is not reused for the gateway authentication. Users still have to reenter their credentials twice. Any idea where to search why ?
- 9831 Views
- 2 comments
- 6 Likes
- Nominated Discussion: Configure Split Tunneling by Domain in General Articles
- Nominated Discussion - Sorting Question in General Articles
- Nominated Discussion: Using the REST API to Create a Bunch of Address Objects in General Articles
- Nominated Discussion: Check Which IP Address (or User, AD Group) is Utilizing More Bandwidth in General Articles
- Nominated Discussion: PDF Report Generated and Date Is Not In Order in General Articles
-
"Address Objects"
1 -
10.0
1 -
10.1
1 -
10.2
2 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
ADNS
1 -
Advanced DNS Security
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
AI
2 -
AI Security
1 -
AI Threat
1 -
AIOPS
1 -
Ansible
1 -
antivirus
1 -
API
1 -
App-ID
1 -
applications
2 -
APS
1 -
Artificial Intelligence
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
aws
3 -
Basic Configuration
4 -
Beacon
1 -
Best Practices
6 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
5 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
cloud ngfw
1 -
cloud security
1 -
Collector Group
1 -
Commit and Push
1 -
Commit Process
1 -
Configuration
8 -
Configuration and Management
3 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
3 -
CPSP
1 -
Custom Signatures
3 -
cyber elite
1 -
cyberelite
11 -
Cybersecurity
1 -
dag
1 -
DDoS
1 -
Debug
1 -
debugging
2 -
Default Policy
1 -
discussions
1 -
DLP
1 -
EDL
2 -
education
1 -
Education and Training
1 -
Education Services
1 -
Educational Services
1 -
Effective Routing
1 -
End to End Encryption
1 -
Endpoint
1 -
export
1 -
failover
1 -
FAQ
1 -
file upload
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
2 -
GCP
2 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
7 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
2 -
Hardware
2 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Layer 2
1 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
3 -
Log Collector Design
2 -
Logging
1 -
login
1 -
Logs
3 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
1 -
Microsoft 365
1 -
Migration
1 -
minemeld
4 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
network security
34 -
Network Security Management
1 -
Network-Security
1 -
Networking
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
6 -
NGFW
30 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
16 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama Configuration
2 -
PBF
1 -
PCNSA
1 -
PCNSE
1 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma Access
7 -
Prisma AIRS
1 -
Prisma SASE
2 -
Prisma SD-WAN
1 -
proactive insights
2 -
Prompt Poaching
1 -
Radius
1 -
Ransomware
1 -
RBI
2 -
region
1 -
Registration
1 -
Remote Browser Isolation
3 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
1 -
script
2 -
SD WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Selective Push
1 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
2 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Cloud Manager
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
system modes
1 -
Tag
2 -
tags
2 -
Terraform
2 -
Threat
1 -
threat log
1 -
Threat Prevention
1 -
Threat Prevention License
1 -
Tips & Tricks
1 -
TLS
1 -
traffic_log
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
6 -
tunnel
2 -
Tutorial
2 -
Unified Monitoring
1 -
upgrade
1 -
upgrade-downgrade
2 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
7 -
VM-Series on AWS
3 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
3 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
WhatsApp
1 -
WildFire
2 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next