- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Certificate Error in GP
- LIVEcommunity
- Discussions
- General Topics
- Certificate Error in GP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-23-2022 11:28 PM - edited 08-24-2022 10:05 PM
Hi Team,
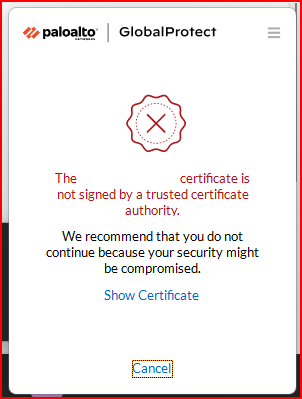
I am getting below error while try to connect to GP.
When I am try to connect to the portal getting this error, any suggestions? before it was showing continue but not it is not showing.
Usually it will give the option to proceed anyway but it is not giving that option. After Reinstallation it is giving that option.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2022 11:47 PM
Hey @SubaMuthuram ,
Yes, but you will need to re-install GP agent again. Because you are in the "catch 22" right now - in order for the GP agent to get the new setting it needs to connect to GP portal, but it cannot because it still has the old setting which will not allow it to proceed with invalid certificate.
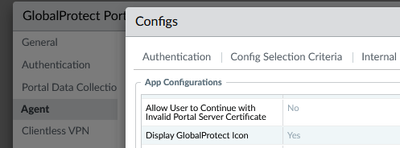
- Set "allow users to continue..." to yes under GP portal settings
- Re-install the GP to get the default behaviour and allow you to continue with invalid cert
- Any subsequent connection should allow you to continue with invalid cert
Although the above will definately solve your problem, I must say the proper way would be to use valid certificate which GP agent trust and leave the setting with default value of no (to block users connecting to portal with invalid certifcate), to prevent any possible man-in-the-middle.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2022 02:19 AM
Hi @SubaMuthuram ,
Did I understand it correctly ? After reinstalling GP your problem was resolved ?
Best,
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2022 10:59 PM
Hi @SubaMuthuram ,
It sounds that like under the portal, agent config you are using either the default value (or specifically set it) for the option "Allow User to Continue with Invalid Portal Server certificate"
As you can imagine from the name it will not allow users to continue with connection if they don't trust the portal certificate.
Now there is a "Catch 22" - this is GP agent behaviour config which GP agent will receive from the portal on his fist connection.
When you manually re-install the GP agent application its default behaviour is restored, which will allow you to continue if you don't trust portal certificate. Once you connect and get the portal config from the firewall any subsequent connection will fail - because agent is now instructed to not continue if portal cert is invalid.
As described on the following link you could control this setting during installation - https://docs.paloaltonetworks.com/globalprotect/9-1/globalprotect-admin/globalprotect-apps/deploy-ap...
This way even the very first connection to portal will fail, because after installation agent default behaviour will be "don't proceed if cert is invalid"
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2022 11:20 PM
If I make "Allow users to continue with Invalid server certificate" to yes will my issue resolve ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2022 11:47 PM
Hey @SubaMuthuram ,
Yes, but you will need to re-install GP agent again. Because you are in the "catch 22" right now - in order for the GP agent to get the new setting it needs to connect to GP portal, but it cannot because it still has the old setting which will not allow it to proceed with invalid certificate.
- Set "allow users to continue..." to yes under GP portal settings
- Re-install the GP to get the default behaviour and allow you to continue with invalid cert
- Any subsequent connection should allow you to continue with invalid cert
Although the above will definately solve your problem, I must say the proper way would be to use valid certificate which GP agent trust and leave the setting with default value of no (to block users connecting to portal with invalid certifcate), to prevent any possible man-in-the-middle.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2022 12:31 PM
That setting can also be deployed in the registry without reinstalling GP:
User Behavior Options (paloaltonetworks.com)
|
PORTAL AGENT CONFIGURATION
|
WINDOWS REGISTRY/ MACOS PLIST
|
MSIEXEC PARAMETER
|
DEFAULT
|
|---|---|---|---|
|
Allow User to Continue with Invalid Portal Server Certificate
|
can-continue-if-portal-cert-invalid yes | no
|
CANCONTINUEIFPORTALCERT INVALID= ”yes | no”
|
yes
|
Regards,
- DM
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2022 10:10 PM
Hi @dmifsud ,
That is interesting...Are you sure GlobalProtect will honor the registry key if it has already have connected at least once to GP portal and received settings from the portal?
From my personal experience I got the impression registry is used only after agent deployment and once it connect to portal it will get settings from the portal and for any subsequent connection it will ignore changes in the registry keys.
I haven't tested to change that specific settings (allow users to continue with invalid cert), but a while ago I tried to change the portal settings refresh timer. We previously had configured portal refresh every 8 hours. I wanted to set it to 2hours, but as you can imagine there were lots of users that didn't receive the new setting (always connecting to cached gateway and never get full 8 hours of connection to trigger portal refresh). So I tried to change the registry key for who were still using the old value, but none of them honored the registry.
- 1 accepted solution
- 23387 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- cloud identity engine and Entra ID certificate warning in General Topics
- while do the factory reset of pa 5250 showing error: findfs: unable to resolve 'label=sysroot0 in Next-Generation Firewall Discussions
- Prisma cloud console is failing to launch in General Topics
- New cert GP cert prompt for people testing Yubikeys for windows logon in GlobalProtect Discussions
- Need help uninstalling Cortex XDR in General Topics