- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Questions about EDL
- LIVEcommunity
- Discussions
- General Topics
- Re: Questions about EDL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2023 01:52 AM
Hello,
I have a firewall rule on the Internet Firewall list this
Source: Palo Alto Networks - High risk IP addresses - Palo Alto Networks - Known malicious IP addresses
Destination Any
Service Any
Action: drop
So if an ip inside the two EDL try to reach a Public Customer Service will be drop right?
How is this list updated? There is a package like the Threat that I have to download with the PA scheduler?
I found an ip that is flagged as malicious by AbuseIPDB with the 28% of confidence.
I check the same ip on the Internet firewall:
request system external-list global-find string x.x.x.x
the answer was IP not present in the list.
So It's means that Palo Alto didn't consider this ip malicious?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2023 11:32 PM
Hi @Charlie80
It does not necessary mean that paloalto consider it as benign, but maybe it is simply not confident enough to add it as the goal also is to have as few as possible false positives. 28% confidence on abjseIP is also not that high. In addition you will always find other sources with additional IP/URLs that are not blocked by paloalto as this company also does not know everything. Sometimes it makes sense to create such drop policies with more than just one list.
@kiwi isn't it updated with the antivirus updates as only this one is updated daily?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2023 03:42 AM
Hi @Charlie80
Yes, an IP within the EDL should be dropped by your policy.
With an active Threat Prevention license, Palo Alto Networks provides multiple built-in dynamic IP lists that you can use to block malicious hosts. The list is updated daily. The download is part of the Threats dynamic update schedule.
Kind regards,
-Kim.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2023 04:46 AM
Thanks,
Have you any idea regarding the last question?
I found an ip that is flagged as malicious by AbuseIPDB with the 28% of confidence.
I check the same ip on the Internet firewall:
request system external-list global-find string x.x.x.x
the answer was IP not present in the list.
So It's means that Palo Alto didn't consider this ip malicious?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2023 11:32 PM
Hi @Charlie80
It does not necessary mean that paloalto consider it as benign, but maybe it is simply not confident enough to add it as the goal also is to have as few as possible false positives. 28% confidence on abjseIP is also not that high. In addition you will always find other sources with additional IP/URLs that are not blocked by paloalto as this company also does not know everything. Sometimes it makes sense to create such drop policies with more than just one list.
@kiwi isn't it updated with the antivirus updates as only this one is updated daily?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2024 06:50 AM
Hello Team,
We are not able to add Predefine EDL list into the security Policy. Please help on it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2024 07:31 AM
Hi @ltinetwork ,
What seems to be the problem ?
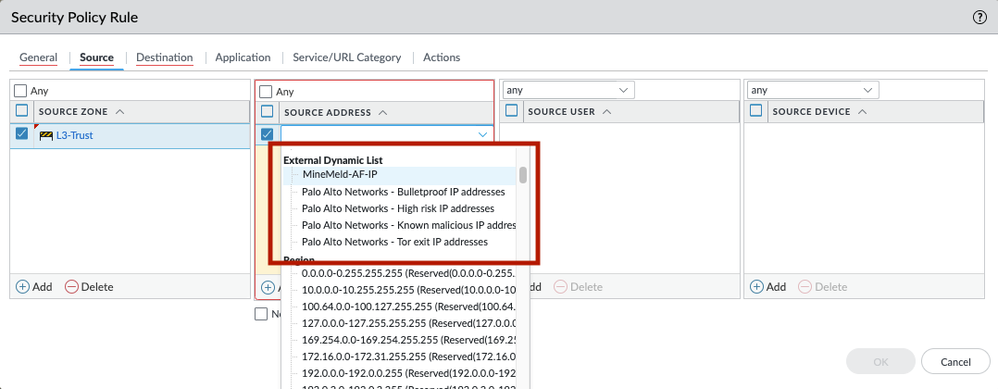
With an active Threat Prevention license, Palo Alto Networks provides built-in IP address EDLs that you can use to protect against malicious hosts. You should be able to select them as a source or destination address object in a Security Policy Rule as shown below.
What seems to be the problem exactly ?
You don't see them ? Is your threat license active ?
Kind regards,
-Kim.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- 1 accepted solution
- 4188 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- make image of PA_3220 in Next-Generation Firewall Discussions
- web file blocking in Next-Generation Firewall Discussions
- XSOAR Engineer Exam Experience in General Topics
- Inquiry Regarding Publishing Custom Third-Party IOC Feed via EDL Hosting Service in Next-Generation Firewall Discussions
- Question on "default" VLAN Interface in Next-Generation Firewall Discussions